DDoS Protection and Mitigation Market Report Scope & Overview:
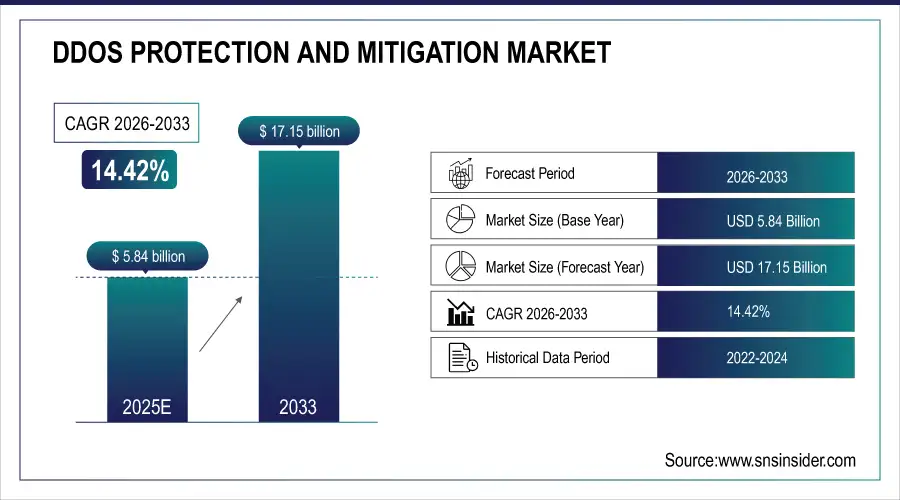
The DDoS Protection and Mitigation Market was valued at USD 5.84 billion in 2025E and is expected to reach USD 17.15 billion by 2033, growing at a CAGR of 14.42% from 2026-2033.
The DDoS protection and mitigation market is experiencing significant growth, due to the increasing frequency and sophistication of cyberattacks. In Q3 of 2024, DDoS attacks saw a 49% QoQ increase and a 55% YoY rise, highlighting the escalating threat landscape. As organizations continue to expand their digital operations and integrate cloud-based services, the need to protect these platforms from DDoS attacks has become more urgent. With 5.44 billion internet users worldwide in 2024 and the rise in IoT device usage, new vulnerabilities are created, giving attackers more opportunities for large-scale assaults. For example, in 2024, Radware successfully mitigated a massive Layer 7 DDoS attack campaign, blocking over 1.4 trillion attacker transactions without customer impact. As a result, businesses are prioritizing advanced DDoS protection solutions to safeguard their networks, fueling demand for mitigation technologies.
DDoS Protection and Mitigation Market Size and Forecast:
-
Market Size in 2025E: USD 5.84 Billion
-
Market Size by 2033: USD 17.15 Billion
-
CAGR: 14.42% from 2026 to 2033
-
Base Year: 2025E
-
Forecast Period: 2026–2033
-
Historical Data: 2022–2024
To Get More Information on DDoS Protection and Mitigation Market - Request Sample Report
This heightened demand is particularly evident in industries like finance, e-commerce, healthcare, and government, where the reliance on online transactions and sensitive data makes them prime targets for DDoS attacks. As these sectors face increasingly sophisticated multi-vector attacks, the need for adaptive solutions that can provide real-time traffic analysis and automated mitigation has intensified. In 2024, Huawei launched its Intelligent Anti-DDoS Solution, leveraging AI-driven detection and mitigation to counter advanced DDoS attacks, ensuring enterprise security. The growing complexity of securing hybrid cloud environments and the shift towards remote work have further amplified this demand, pushing organizations to seek integrated, scalable protection solutions.
Looking forward, the DDoS protection and mitigation market offers significant growth potential, particularly with the integration of AI and machine learning technologies into mitigation platforms. These advanced technologies enable faster and more accurate attack detection, helping businesses stay ahead of emerging threats. In 2024, Cloudflare introduced "Firewall for AI," a Web Application Firewall designed to secure large language models from threats like prompt injection and data exfiltration, underscoring the growing importance of AI-driven security solutions. Furthermore, the advent of 5G networks introduces both new challenges and opportunities, as larger, more dispersed attack surfaces demand innovative, scalable solutions. As regulatory frameworks around cybersecurity tighten and the cost of data breaches continues to rise, the DDoS protection market is set to expand further, driven by technological advancements and an ever-evolving threat landscape.
DDoS Protection and Mitigation Market Drivers
-
The Expanding Role of Internet-Connected Devices and Its Growing Impact on the Demand for DDoS Protection and Mitigation Solutions
The rapid growth of Internet of Things devices has significantly expanded the attack surface for cybercriminals, which, in turn, is escalating the need for robust DDoS protection and mitigation solutions. As more connected devices—ranging from smart home gadgets to industrial sensors—enter the networked ecosystem, they provide additional entry points for potential DDoS attacks. These devices, often lacking strong security measures, can be compromised and used in botnet attacks, overwhelming systems and networks with malicious traffic. Consequently, organizations must implement advanced DDoS mitigation technologies to safeguard their digital infrastructure, ensuring business continuity and data integrity. This increasing reliance on IoT devices drives the demand for more sophisticated and scalable DDoS protection solutions to defend against the ever-evolving threat landscape.
-
The Integration of Artificial Intelligence and Machine Learning in DDoS Mitigation Technologies to Improve Detection and Response Speed
The integration of artificial intelligence and machine learning into DDoS protection and mitigation solutions significantly enhances the ability to detect and respond to attacks more effectively. AI and ML algorithms can analyze large volumes of network traffic in real time, identifying potential threats and distinguishing between legitimate and malicious activities with greater accuracy. This capability allows for faster detection and automated responses to DDoS attacks, minimizing downtime and reducing the impact on business operations. As these technologies evolve, they continue to improve the efficiency of mitigation strategies, making it easier for organizations to defend against increasingly sophisticated DDoS attacks. The ongoing advancements in AI and ML are driving broader adoption of DDoS protection solutions, as businesses seek to stay ahead of the rapidly growing cyber threat landscape.
DDoS Protection and Mitigation Market Restraints
-
Challenges with False Positives and Overblocking in DDoS Protection Solutions Impacting Adoption and User Experience
Despite advancements in DDoS mitigation technologies, false positives remain a significant challenge. These technologies may occasionally misidentify legitimate traffic as malicious, leading to overblocking of websites or services. This disruption can result in downtime, affecting the user experience and operational efficiency of businesses. Organizations may face difficulties balancing security with user accessibility, as overly aggressive mitigation strategies could block valid users or services, causing frustration and loss of business. The possibility of false positives can deter some companies from fully adopting DDoS protection solutions, particularly in industries where uptime and seamless user experiences are critical. As a result, the market faces a hurdle in ensuring that mitigation systems are both accurate and non-intrusive, encouraging wider adoption while maintaining a positive user experience.
-
The High Initial and Ongoing Costs of Advanced DDoS Protection Solutions Limiting Widespread Adoption, Especially Among Smaller Businesses
Advanced DDoS protection solutions, particularly those utilizing artificial intelligence and machine learning, often come with a significant price tag. The high initial costs associated with implementing these solutions can be a substantial barrier, especially for small and medium-sized enterprises that may already operate under budget constraints. In addition to the upfront expenses, there are ongoing costs related to system maintenance, updates, and training staff to manage the technology effectively. These financial burdens may deter businesses from investing in the necessary infrastructure to protect against DDoS attacks, particularly when smaller organizations may struggle to justify the investment without clear, immediate return. As a result, the high costs of implementation and maintenance limit the adoption of DDoS protection solutions, particularly among businesses with limited resources.
DDoS Protection and Mitigation Market Segmentation Analysis
By Enterprise Size
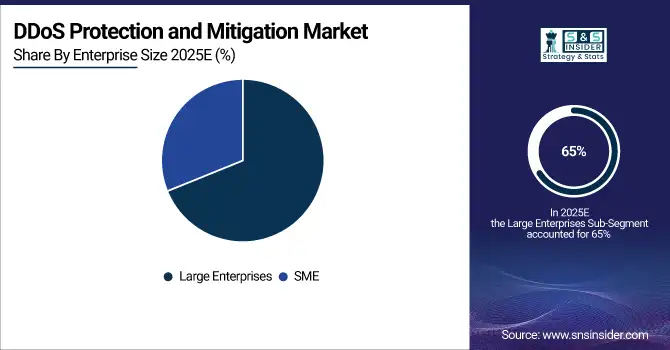
In 2025, the large enterprises segment dominated the DDoS protection and mitigation market, accounting for approximately 65% of the revenue share. These organizations typically have complex digital infrastructures that are critical to their operations, making them prime targets for DDoS attacks. The substantial financial resources available to large enterprises allow them to invest in advanced, scalable mitigation technologies, ensuring a robust defense against increasingly sophisticated cyber threats. This capability to adopt cutting-edge solutions and the high stakes involved in safeguarding business continuity are key factors driving their dominant position in the market.
The SME segment is expected to grow at the fastest CAGR of about 15.82% from 2026 to 2033. As cyber threats become more prevalent, SMEs are increasingly recognizing the need for DDoS protection to maintain business operations and protect their reputation. The growing availability of affordable, cloud-based solutions and the increasing awareness of cybersecurity risks are empowering SMEs to adopt mitigation technologies. Additionally, the scalability of DDoS protection services enables SMEs to access robust solutions that fit their budgets, fueling rapid growth in this segment.
By Application
In 2025, the network security segment led the DDoS protection and mitigation market, capturing around 44% of the revenue share. Network security remains the primary defense mechanism against DDoS attacks, as it directly protects an organization's core network infrastructure. With growing concerns over network downtime and service disruption, businesses are increasingly investing in advanced network-level solutions to block malicious traffic and ensure seamless connectivity. The critical role of network security in maintaining operational continuity, particularly for large enterprises with expansive networks, contributed to its dominant market position.
The application security segment is anticipated to grow at the fastest CAGR of approximately 15.79% from 2026 to 2033. As businesses continue to move their operations and services to web-based platforms, the risk to application-layer vulnerabilities has escalated. Attackers are now targeting application layers with more precision, exploiting weaknesses in web applications. This shift in attack strategies is driving the demand for specialized application security solutions, which offer targeted protection against evolving threats. As organizations prioritize safeguarding customer-facing applications, the application security segment is poised for rapid expansion.
By Industry Vertical
In 2025, the IT and telecommunication segment led the DDoS protection and mitigation market, holding a revenue share of approximately 27%. This dominance is driven by the essential role these industries play in global communication and connectivity. Telecom providers and IT companies face constant threats to their vast networks and services, which are integral to everyday operations. Given the critical need for uninterrupted service and network security, these sectors are heavily investing in advanced DDoS mitigation technologies to prevent disruptions and ensure reliability, making them the largest contributors to the market.
The BFSI segment is expected to grow at the fastest CAGR of around 16.98% from 2026 to 2033. The increasing digitalization of banking services, mobile transactions, and online insurance platforms has led to a surge in cyberattacks targeting financial institutions. These organizations handle sensitive financial data, making them prime targets for DDoS attacks that could disrupt operations or compromise customer information. As a result, the growing need for robust protection against such attacks is fueling rapid adoption of DDoS mitigation solutions in the BFSI sector, positioning it for significant growth in the coming years.
Regional Analysis
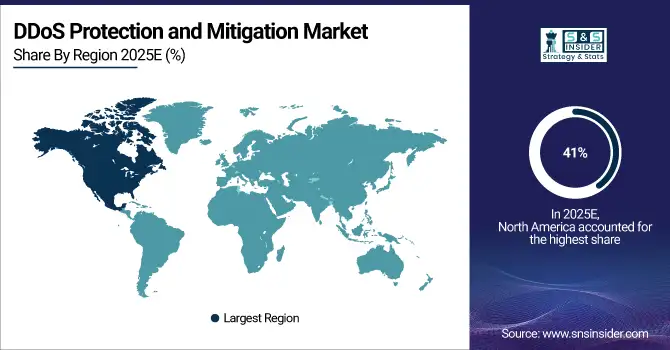
In 2025, North America dominated the DDoS protection and mitigation market, capturing approximately 41% of the revenue share. The region’s dominance is attributed to its advanced technological infrastructure, high levels of cybersecurity awareness, and the presence of leading DDoS protection solution providers. With a large number of enterprises across industries such as finance, telecommunications, and healthcare relying on secure online services, North American businesses are heavily investing in cutting-edge DDoS mitigation technologies to protect their critical networks and data from sophisticated cyber threats.
Do You Need any Customization Research on DDoS Protection and Mitigation Market - Enquire Now
The Asia Pacific region is expected to grow at the fastest CAGR of around 16.84% from 2026 to 2033. The rapid digitalization of economies in countries like China, India, and Japan is driving increased adoption of DDoS protection solutions. As businesses across the region expand their online presence and cloud infrastructure, they become more vulnerable to cyberattacks, prompting heightened demand for effective mitigation strategies. Moreover, the increasing focus on cybersecurity and growing investments in IT infrastructure are fostering the rapid growth of the DDoS protection market in Asia Pacific, positioning it as the fastest-growing region globally.
Key Players
-
NetScout (Arbor Networks APS, Arbor Cloud)
-
Akamai Technologies (Kona Site Defender, Prolexic)
-
Radware (DefensePro, AppWall)
-
Huawei (AntiDDoS8000, Cloud DDoS Protection)
-
Fortinet (FortiDDoS, FortiWeb)
-
Imperva (Incapsula DDoS Protection, SecureSphere)
-
F5 (BIG-IP Advanced Firewall Manager, Silverline DDoS Protection)
-
Cloudflare (DDoS Protection, Web Application Firewall)
-
BT (DDoS Mitigation Service, Assure DDoS Protection)
-
A10 Networks (Thunder TPS, Thunder ADC)
-
Link11 (DDoS Protection Cloud, Web DDoS Protection)
-
Fastly (Next-Gen WAF, DDoS Protection)
-
Corero (SmartWall Threat Defense System, SecureWatch Analytics)
-
Allot (DDoS Secure, Secure Service Gateway)
-
StrataCore (DDoS Protection Services, Managed Security Services)
-
Sucuri (Website Firewall, DDoS Protection)
-
StackPath (DDoS Mitigation, Web Application Firewall)
-
Seceon (Open Threat Management Platform, aiSIEM)
-
Haltdos (DDoS Mitigation Platform, Web Application Firewall)
-
DDoS-Guard (DDoS Protection Cloud, Application Layer Protection)
-
Indusface (AppTrana, Indusface WAF)
-
activereach (DDoS Testing, DDoS Protection Services)
-
Mlytics (Smart Load Balancer, DDoS Protection)
-
Nexusguard (DDoS Protection, Origin Protection)
-
RioRey (DDoS Mitigation Appliances, Behavioral Analytics)
-
PhoenixNAP (DDoS Protected Servers, Managed DDoS Protection)
Recent Developments:
-
In December 2024, NETSCOUT announced the enhancement of its Adaptive DDoS Protection Solution, leveraging AI and machine learning to defend critical IT infrastructure against AI-enabled DDoS attacks.
-
In December 2024, Akamai introduced a new Behavioral DDoS engine to its App & API Protector platform, enhancing its defense capabilities against advanced, dynamic DDoS attacks. The engine leverages AI and machine learning to detect and mitigate threats more effectively, improving security for applications and APIs.
| Report Attributes | Details |
|---|---|
| Market Size in 2025E | USD 5.84 Billion |
| Market Size by 2033 | USD 17.15 Billion |
| CAGR | CAGR of 14.42% From 2026 to 2033 |
| Base Year | 2025E |
| Forecast Period | 2026-2033 |
| Historical Data | 2022-2024 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Component (Hardware, Software, Services) • By Enterprise Size (SME, Large Enterprises) • By Deployment Mode (On-premises, Cloud-based) • By Application (Network Security, Endpoint Security, Application Security, Database Security) • By Industry Vertical (Government and Defense, BFSI, Manufacturing, IT and Telecommunication, Healthcare, Education, Retail, Other) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles | NetScout, Akamai Technologies, Radware, Huawei, Fortinet, Imperva, F5, Cloudflare, BT, A10 Networks, Link11, Fastly, Corero, Allot, StrataCore, Sucuri, StackPath, Seceon, Haltdos, DDoS-Guard, Indusface, activereach, Mlytics, Nexusguard, RioRey, PhoenixNAP |

