Container Security Market Report Scope & Overview:
Get More Information on Container Security Market - Request Sample Report
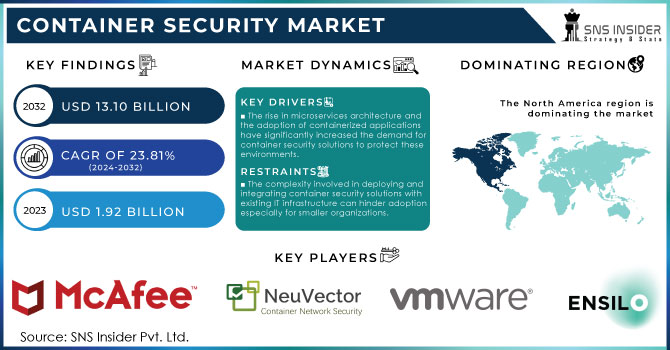
Container Security Market Size was valued at USD 1.92 Billion in 2023 and is expected to reach USD 13.10 Billion by 2032, growing at a CAGR of 23.81% over the forecast period 2024-2032.
The adoption of container applications among enterprises helps to drive the growth of container security market for security models and methods, along with cloud computing across additional sectors. Serverless technologies are on the rise, and solutions like Customer Identity Management (CIAM) offer advanced security to protect company and user data. The shift towards cloud-based platforms such as Zoom and Salesforce, and the success of public cloud providers like AWS, Microsoft Azure, and Google Cloud, further fuel this growth. Enterprise customers demand application portability between clouds with Containers and Docker/Kubernetes simplifying development and reducing Time to Market for Application Development. Such as the purchase by Docker of Tilt in 2022 which adds to Kubernetes development, providing reproducible environments and live updates, helping container adoption. The U.S. Department of Defence (DoD) in 2023 issued an update to its Cybersecurity Maturity Model Certification (CMMC), requiring all defence contractors subject to Level 3 and above certifications be compliant with container security guidelines by 2024. A 47% of IT decision makers in North America are accelerating their deployment of container security solutions as part of cyber defence strategies, according to a 2023 survey by Global Tech Outlook that showed the number was driven largely by rising cyber-attacks against vulnerable containers.
Containerization supports the DevOps model and can help deliver software at scale, which is often required for large-scale IoT systems. Benefit like flexibility, cost effectiveness; Scaling services easily. The trend for businesses becoming more digital is already causing automation and cloud transitions at a faster rate. DevOps is key to this transformation by bringing operations into software and quality practices, making business much agile and adaptive with DevOps. The growth in the container security market is likely to result from these trends. In a study by the National Institute of Standards and Technology (NIST), they found that nearly 30% of all vulnerabilities reported in container environments were around misconfigurations which is stated as most common security issue in this field. The UK National Cyber Security Centre (NCSC) as it stated in its latest annual review that container environments were implicated in 18% of all cybersecurity breaches this year, making the case for better security practices around these.
Market Dynamics
Drivers
-
The rise in microservices architecture and the adoption of containerized applications have significantly increased the demand for container security solutions to protect these environments.
-
The increasing frequency and sophistication of cyberattacks targeting container environments have driven the need for robust security measures to safeguard containerized applications.
-
The growing use of DevOps practices and CI/CD pipelines necessitates container security to ensure secure code deployment and infrastructure management.
-
The shift towards cloud-native technologies and digital transformation initiatives by enterprises are driving the adoption of container security solutions to protect cloud workloads.
The increasing adoption of containerized applications which is impacting the growth of Container Security Market. Containers provide a lightweight and efficient way to deploy applications, which is why they have been more commonly adopted across industry. Containers have a number of advantages ranging from quicker deployment, to better scaling and resource efficiency on top. It has also increased the attack surface for cyber threats due to this wide use of containers. In fact, over the last year alone about 50% of organizations using containerized applications experienced a security breach, 2023 recent report. This certainly increases the need for powerful container security solutions to protect this threat.
Additionally, as the industry matures and enterprise organizations rapidly adopt microservices architecture, the managing containers and securing containerized applications increase in complexity. The variety of tools available points to the need for specialized security solutions that can work in harmony with DevOps practices and CI/CD pipelines, providing confidence in secure application deployment and operation. The increasing adoption of containers and hybrid cloud architectures, combined with the growing threat landscape is driving the need for holistic container security solutions to protect critical business applications.
Restraints
-
The complexity involved in deploying and integrating container security solutions with existing IT infrastructure can hinder adoption, especially for smaller organizations.
-
The shortage of skilled professionals with expertise in container security can be a significant barrier to the implementation and management of these solutions.
As organizations adopt container security solutions, they face challenges integrating these solutions with existing IT infrastructures. According to a 2023 report some IT professionals said that the majority of them (53%) specified integration complexity as an important restriction limiting their capability to implement container security effectively. That complexity is often due to the need for different cloud platform compatibility, as well as with their respective legacy system support that can amount in extensive customization/configuration. A 47% percent of organizations experience frequent deployment time delays related to integration challenges, and that have compromised their security posture overall. These are barriers to integrating container security solutions, which may slow the benefits and discourage some organizations from fully embracing deployment.
Segment Analysis
By Deployment
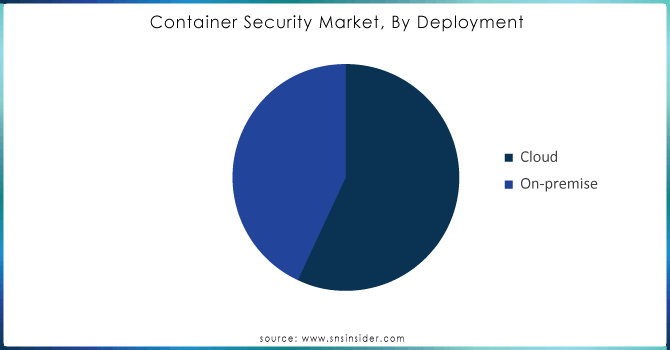
The cloud-based deployment segment accounted for more than 53% share of market in 2023. Even with the rise of cloud computing, security issues still make networks a weak technology for protection from cyber threat and data breaches. Because personal security measures off-premises are too expensive, companies often turn to computer security software pools which offer similar results of discovery and prevention. This provides a massive opportunity for the sector, as it means that Software as a Service (SaaS) platforms are increasingly accessible to more corporations, and enhancements driven by Artificial Intelligence (AI) can now be used great data resources good security practices proficient services The compelling cost savings associated with cloud-based platforms are encouraging commercial enterprises and government bodies to transition towards the adoption of cloud storage & services which is in turn, propelling demand for cloud-based container security solutions throughout the forecast period.
On-premise segment expected to grow at a significant CAGR over the forecast period. Various companies prefer on-premise solutions as it gives full control business data will be the only place held and upgrades became easy which in turn increases security level to its maximum. On-prem deployments decrease reliance on third party providers since customers can directly monitor and control data. For example, Qualys container security provides visibility and continuous bastion for on-premise containers along with vulnerability scanning that is highly accurate leaving the job of remediating to Security teams. The importance placed on keeping data in house will drive sales of 'on premise' solutions for the during forecast period.
Need any customization research on Container Security Market - Enquiry Now
By Organization size
The large enterprise segment dominated the market with a share of over 54% in 2023, As they are typically managing lots of applications and services for various distributed environments, large enterprises need to constantly update them in order to fulfil business requirements. This includes security, productivity gains and cost savings. These firms are increasingly putting their money in DevOps solutions with an aim to write error-prone code, release high-quality software products and carry out consistent customer interactions. Improved collaboration between development and operational teams due to DevOps leads to better product delivery, encouraging large enterprises in the adoption of container security solutions.
Small & Medium Enterprises (SMEs) segment is projected to grow at the highest CAGR during the forecast period. They also find new ways to increase speed of delivery without creating new mistakes or delays. The SMEs are enabled to absolutely overcome all problems related with service delivery through integration of DevOps tools such as software development, quality assurance and infrastructure operations in a composite automated framework. DevOps leads to smoother processes, reduced delivery time and bottlenecks while increasing speed of production, which in turn enhances overall productivity response towards business needs.
By End User
The IT and telecom segment accounted the highest market share over 20.8% in 2023. The COVID-19 pandemic drove IT and telecom providers to quickly embrace the use of cloud applications/services, so top workers could replicate traditional office-based work experiences from anywhere (remotely), while they traverse legacy network security perimeters. These companies to shift their focus towards developing in-house cloud network security solutions which helped them sustain the market growth. IT and telecom companies are particularly attractive targets due to the sensitive personal data they store, including names, addresses or financial details. The need of the hour for telecom companies is to protect this data and avoid any instances of breaches, which often leads them towards increasing their investments on security solutions. Furthermore, with the growing complexity of global regulatory environments present day telecom companies are also having to evolve and increase their compliance efforts warranting further growth in such sectors.
BFSI segment is projected to exhibit with a significant CAGR. Container technology is imperative for financial institutions to remain competitive against fintech rivals. This is leading many banks to rethink and refresh their IT processes and technologies, thus increasing application portability in this era of heightened operational resilience. Containers Make It Easier for Banks to Implement Microservices, Helping Them Modernize IT at Their Own Pace The innovations are likely to fuel adoption of container security solutions in the BFSI industry over the upcoming years.
Regional analysis
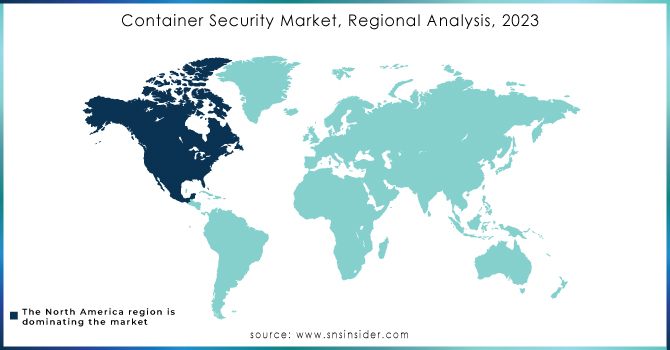
North America dominated the container security market and held largest share more than 32% in 2023. The growth of this region can be attributed to the reliance on emerging technologies by small and medium-sized businesses (SMBs), despite growing microservices demand, as well as a drive towards digital transformation among enterprises. Rapid adoption of cloud solutions by the SMEs is contributing to further business. Intensified way. For instance, Docker (a U.S.-based software provider) purchased Atomist in June 2022 to further equip it's the company secure software supply chain within businesses. With this acquisition, client organizations can now see and govern their software supply chains without adding friction to existing workflows and tools. These factors are anticipated to propel the demand of container security solutions in North America throughout the forecast period.
APAC region is growing with a significant CAGR during forecast period. This growth is driven by the rising load of organizational data, increasing number of SMEs and vulnerability management applications being extensively used for tackling cyberattacks. According to Red Hat’s 2022 survey, a majority of IT executives in Asia Pacific are employing open-source code for DevOps teams overseeing infrastructure updates. Furthermore, leading IT solutions in the region seek for superior software development practices followed by advanced technologies backed with professional endorsements; which has consequently created traction for container security solution offerings across enterprise scale businesses within Asia Pacific during the forecast timeline.
Key Players:
The key market players are NeuVector, enSilo, VMware, IBP Corporation, McAfee Corporation, Palo Alto Networks, Aqua Security, Juniper Networks, CrowdStrike Holdings, Fidelis Cybersecurity, Tenable Inc, Check Point Software Technologies, Aqua Security, Cisco System, Inc., Sonatype, and others.
Recent Developments:
-
The Kaspersky released a complete solution for container environments, called Kaspersky Container Security (KCS), in October 2023. The intention of the product is to secure container applications from development to production. KCS is production-ready, low-cost and modular for easy customization and deployment within a company's IT ecosystem.
-
The same month in 2023, Net Feasa revealed a patent-pending update on its IoTPASS smart container tracking system that would be further secure. It is the secure link between a shipping container and its locking bar, It utilizes Net Feasa's context-aware AI to intelligently detect security breaches and anomalies.
-
Palo Alto Networks purchased Cider Security in November 2022, a company that specializes software supply chain and application security (AppSec). The purchase is in support of Palo Alto's Prisma Cloud strategy to secure the full stack of application security through its lifecycle.
| Report Attributes | Details |
| Market Size in 2023 | USD 1.92 Bn |
| Market Size by 2032 | USD 13.10 Bn |
| CAGR | CAGR of 23.81% From 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Components (Products, Services) • By Organizational Size (Small & Medium Enterprises, Large Enterprises) • By Deployment (Cloud, On-premises) • By End User (BFSI, Retail & Consumer Goods, Healthcare & Life Science, Manufacturing, IT & Telecommunication, Government & Public Sector, Others) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]). Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia Rest of Latin America) |
| Company Profiles | NeuVector, enSilo, VMware, IBP Corporation, McAfee Corporation, Palo Alto Networks, Aqua Security, Juniper Networks, CrowdStrike Holdings, Fidelis Cybersecurity, Tenable Inc, Check Point Software Technologies, Aqua Security, Cisco System, Inc., Sonatype |
| Key Drivers | • Popularity of microservices and digital transformation are consistently Increasing across enterprises. • Containers are being used by businesses to optimize their application operations increasingly |
| Market Restraints | • Absence of awareness and facing challenges in operations about operational technology. • Insufficient financial stability for small and medium-sized businesses. |

