Cryptojacking Solution Market Report Scope & Overview:
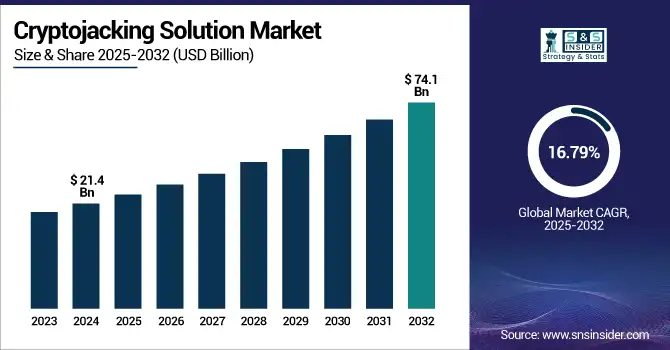
The Cryptojacking Solution Market size was valued at USD 21.4 billion in 2024 and is expected to reach USD 74.1 billion by 2032, growing at a CAGR of 16.79% during 2025-2032.
To Get more information on Cryptojacking Solution Market - Request Free Sample Report
The cryptojacking solution market growth is driven by the increasing instances of unauthorized cryptocurrency mining across networks, devices, and cloud environments. With cybercriminals increasingly turning to system weaknesses to commandeer processing power for mining digital currencies, organizations are determined to adopt innovative cryptojacking prevention tools. Also, an increase in remote work, IoT devices, and cloud infrastructure usage plays a crucial part in this growth. Governments and enterprises are putting earnest money into the development of cybersecurity frameworks that would deploy cryptojacking detection and response techniques.
Cryptojacking solution market trends are the implementation of artificial intelligence and machine learning to detect the mining antics in real-time, allowing immediate response to mitigate the effect. Furthermore, increasing cognizance regarding the functional and cost implications of cryptojacking incidents is boosting the market demand in end-use industries, including BFSI, healthcare, and IT. Over the next 5–7 years, this market is likely to see strong growth.
The U.S. cryptojacking solution market is propelled by growing cloud adoption, escalating cyber threats, and stringent data privacy regulations. Valued at USD 480 million in 2024, it is anticipated to reach USD 1.32 billion by 2032, registering a CAGR of 13.2%.
Over the year of 2023, while the number of cryptojacking incidents in the U.S reached 211.7 million, a 340% of year-to-year growth compared to former 48 million, thus making the meaning of rampant for cryptojacking incidents. This spike indicates that mining attacks are becoming larger and more complex by targeting enterprise networks and cloud environments.
Cryptojacking Solution Market Dynamics:
Drivers:
-
Rise in Cryptocurrency Popularity Increases Cryptojacking Attacks, Driving the Demand for Advanced Protection Solutions
Unfortunately, the huge impact of cryptocurrency has also opened it to cryptojacking attacks, where cybercriminals hijack a device and mine for digital currencies without permission. These attacks are hidden and often unnoticed for a long period, and during that time, they overwhelm and perform poorly on the system while consuming a lot of electricity. So far, enterprises are more conscious of these risks and are spending on the best secure cryptojacking solutions. Rising instances of cyber incidents and their increasing severity, particularly in cloud environments and IoT devices, are boosting the market. The demand for these real-time AI-based threat detection systems is growing rapidly as more organizations move their operations online and into a remote infrastructure.
Restraints:
-
Lack of Awareness and Expertise in SMEs Delays Cryptojacking Detection, Hindering the Adoption of Preventive Solutions
Although cryptojacking is a growing concern these days, many small and medium enterprises continue to stay in the dark about its potential impact. Few of them have the technical skills or subset of personnel focused on cybersecurity, which are needed to expose and counter these types of threats. Many signs of the presence of a cryptojacker are misinterpreted as regular system issues, so detection and response are delayed. In addition to this, the implementation cost of many sophisticated solutions, particularly those that utilize AI or machine learning, can be prohibitively expensive for organizations with tight budgets. For less digitally mature regions, this unawareness and unpreparedness limit the global uptake of cryptojacking protection solutions.
Opportunities:
-
Advancements in AI and Cloud Technologies Enable More Efficient Detection, Creating Opportunities for Scalable Cryptojacking Solutions
Cryptojacking solution is among the areas of opportunity, driven by fast-evolving AI and cloud technologies. The AI systems spot irregular activity patterns associated with illegal cryptocurrency mining among large datasets of network data. Similarly, cloud-based security solutions provide on-demand, cost-effective protection by enabling centralized monitoring and automation, making them a viable option for organizations of any size. The approach of having AI-based cryptojacking solutions deeply embedded in these environments would be a key differentiator as enterprises are ramping up the migration toward the never-ending cloud-first strategies. Thus, vendors with end-to-end and cloud-native solutions that combine predictive analytics with behavioral detection will likely gain a sizeable share of the enterprise market.
A 2024 report by the Cloud Security Alliance and Google Cloud shows 55% of organizations plan to adopt GenAI, and 67% have tested AI for security, highlighting AI’s rising role in detecting and preventing threats like cryptojacking.
Challenges:
-
Cybercriminals’ Use of Sophisticated Evasion Tactics Forces Continuous Updates in Security Solutions to Combat Evolving Cryptojacking Threats
The evolving techniques of the attackers are one of the biggest barriers to combating cryptojacking. Tactical use of obfuscation, fileless malware, and encrypted traffic to bypass traditional detection is common among cybercriminals. They also use appropriate tools and processes, such as browser-based scripts or reputable cloud services, to obscure their activities. This creates a challenge for traditional security tools to differentiate between good and bad activity. Also, since cryptojacking payloads are often packaged with seemingly benign applications or websites as drive-by downloads, their footprint and sophistication become exponentially larger. Therefore, security providers have a seemingly endless challenge to update their solutions and expand threat intelligence to outpace these tactics.
For instance, according to McAfee's Threat Report 2024, cryptojacking attacks that successfully evaded detection surged by 60% over the past year, highlighting a sharp rise in the use of stealthy, sophisticated evasion techniques.
Cryptojacking Solution Market Segmentation Analysis:
By Component
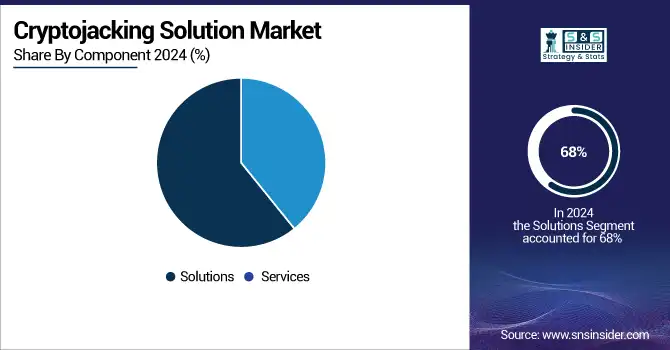
The solution segment dominated the cryptojacking solution market and contributed 68% revenue share in 2024, including software tools to mitigate and detect the cryptojacking threat. These AI and machine learning-based solutions work by analyzing network activity, detecting anomalies, and issuing real-time alerts each time a potential threat is identified. Cryptojacking attacks have become more advanced, and that requires smart software to detect them before they occur. With organizations further digitizing operations and migrating to cloud services, the need for scalable and automated security solutions will likely increase.
The services segment is expected to register the fastest CAGR during 2025-2032, as they are a major part to the growing complexity of cyber threats and the lack of adequate cybersecurity professionals. Enterprises are relying on managed and professional services for guidance on when deploying, managing, or patching solutions to prevent cryptojacking. Continuous monitoring of threat intelligence and incident response is an essential element in the changing threat landscape provided by these services.
By Deployment
In 2024, the cloud segment dominated the cryptojacking solution market and represented 71% of the cryptojacking solution market share, as cloud-based cryptojacker solutions are increasingly favored for their scalable, flexible, and cost-effective features. Cloud-based security solutions enable organizations to rapidly deploy security without investing in a lot of hardware and infrastructure. The growing utilization of cloud services across multiple industry verticals is further bolstering the need for cloud-based cryptojacking solutions.
a 2024 Cloud Security Report by Check Point Software Technologies revealed that 91% of organizations are now prioritizing AI to enhance their security posture, emphasizing the shift toward leveraging AI for proactive threat prevention.
The on-premises segment is expected to register the fastest CAGR during the forecast period. The growth is primarily driven by the rising demand among organizations to exert more control over their data and security settings. There are many advantages of on-premises solutions, such as greater data privacy, regulatory compliance, and customized security controls to meet organization-specific requirements. On-premises deployments are particularly popular among large enterprises with complex IT environments and strict security requirements.
By Industry
The BFSI segment led the cryptojacking solution market and held the largest revenue share in 2024, due to the large volume of financial transactions and the sensitive nature of financial data. Cryptojacking attacks in this field can lead to significant monetary losses and reputational damage to organizations, heightening the focus on robust cybersecurity protections across the board.
The healthcare industry is expected to register the fastest CAGR during 2025-2032, attributed to the rapid digitalization of medical records and the number of connected devices that are being used, which can easily be exploited. Due to cryptojacking attacks in healthcare, critical services can be disrupted, and sensitive patient data can be compromised, resulting in dire consequences. This is now leading to an increasing demand for efficient crypto smith solutions in the healthcare sector due to the need to protect patients and ensure the continuity of services.
Regional Analysis
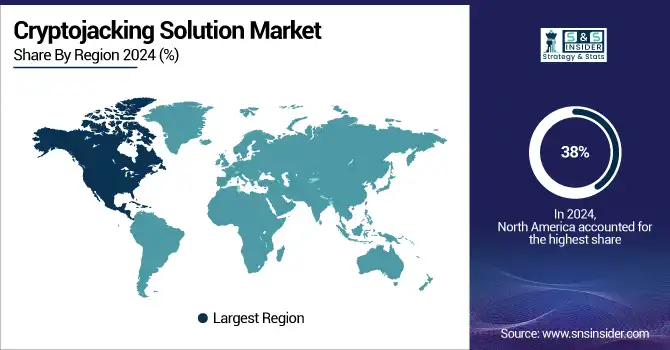
North America dominated the cryptojacking solution market and represented 38% of revenue share in 2024 due to high-end technological infrastructure, a growing number of digital technology adopters, and stringent cybersecurity regulations. The dominance of the region is largely attributed to the presence of such major cybersecurity vendors, and a strong focus on data protection. High demand cryptojacking solution from BFSI and healthcare is showing the U.S. as one of the largest suppliers.
During the forecast period, the Asia Pacific is projected to register the fastest CAGR due to continuing digitalization in the area, the ubiquity of cloud services, and the rising volume of cyber threats. China, India, Japan, and South Korea are working on developing cybersecurity infrastructure due to concerning threats to investments. Along with the above-mentioned factors, smart cities, and digital governance, are other key focuses of the region, fuelling the need for sophisticated cryptojacking.
For instance, in 2024, Singapore launched the ASEAN Regional Computer Emergency Response Team facility, committing USD 10.1 million over ten years to enhance regional cyber threat information sharing and response capabilities.
In the Asia Pacific region, China dominated the cryptojacking solution market due to its large digital economy, a huge number of internet users, and high acceptance of blockchain and cryptocurrency technology. Demand for cybersecurity policies with sharp claws from the government, along with investment in AI-powered threat detection systems, to enhance overall growth prospects. China is expected to grow at a strong pace for the cryptojacking prevention solution market, owing to the increasing number of cyberattacks and expanding digital infrastructure.
Europe is the second-largest cryptojacking solution market, due to stringent data protection legislation in the region, such as the General Data Protection Regulation and increasing cybercrime incidents in the region. Rapidly increasing expenditures on cyber defense and infrastructure are driving market growth market will continue to grow at a steady pace as digital transformation only jumps in pace across the public and private sectors.
In Europe, Germany dominated the market due to a well-established industrial structure and stringent legislative means. The growing importance of critical infrastructure protection and strong cybersecurity programs are significant growth driver. Increasing digitalization in both manufacturing and finance will make cryptojacking solutions more popular.
Get Customized Report as per Your Business Requirement - Enquiry Now
Key Players
The major cryptojacking solution market companies are Cisco, Palo Alto Networks, McAfee, Symantec, CrowdStrike, Check Point Software, Trend Micro, Sophos, Kaspersky, FireEye, and others.
Recent Developments
-
In March 2024, Sophos published its 2024 Threat Report, noting a significant increase in information-stealing malware targeting macOS systems. These malware variants are capable of collecting system data, browser information, and cryptocurrency wallets, indicating a rise in cryptojacking activities on macOS platforms.
-
In May 2024, Palo Alto Networks addressed a critical zero-day vulnerability (CVE-2024-3400) in its PAN-OS, which was exploited by the RedTail cryptomining malware. Attackers leveraged this flaw to deploy cryptocurrency miners and establish persistent backdoors on compromised firewalls.
-
In August 2024, Trend Micro released a midyear cybersecurity threat report highlighting the exploitation of CVE-2023-22527 for cryptojacking attacks. The report emphasized the use of extended detection and response (XDR) solutions to identify and mitigate such threats effectively.
| Report Attributes | Details |
|---|---|
| Market Size in 2024 | US$ 21.4 Billion |
| Market Size by 2032 | US$ 74.1 Billion |
| CAGR | CAGR of 16.79 % From 2024 to 2032 |
| Base Year | 2024 |
| Forecast Period | 2024-2032 |
| Historical Data | 2021-2023 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Component (Solution, Services) • By Deployment (Cloud-Based, On-Premises) • By Industry (BFSI, Retail, Government and Public Sector, Manufacturing, Healthcare, Education, Energy and Utilities, Others) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Germany, France, UK, Italy, Spain, Poland, Turkey, Rest of Europe), Asia Pacific (China, India, Japan, South Korea, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (UAE, Saudi Arabia, Qatar, South Africa, Rest of Middle East & Africa), Latin America (Brazil, Argentina, Rest of Latin America) |
| Company Profiles | Cisco, Palo Alto Networks, McAfee, Symantec, CrowdStrike, Check Point Software, Trend Micro, Sophos, Kaspersky, FireEye and others in report |

