Data Loss Prevention (DLP) Solutions Market Report Scope & Overview:
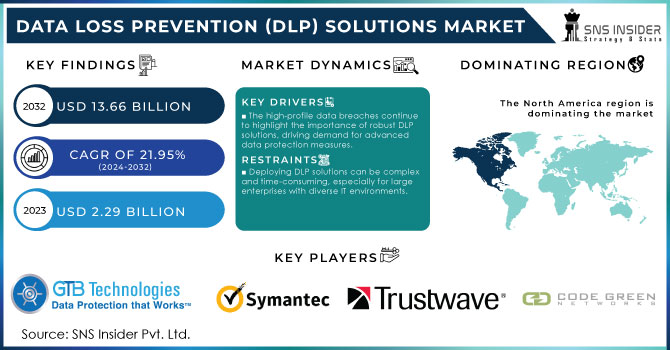
Data Loss Prevention (DLP) Solutions Market was valued at USD 2.66 billion in 2023 and is expected to reach USD 16.48 billion by 2032, growing at a CAGR of 22.52% from 2024-2032.
This report includes key insights into security incident reduction statistics, compliance and regulatory influence, spending patterns, and employee training & awareness trends. The market is witnessing robust growth as organizations increasingly prioritize data protection amid rising cyber threats and tightening regulatory frameworks. Companies are investing heavily in DLP technologies to reduce data breaches, meet evolving compliance mandates such as GDPR and HIPAA, and strengthen internal data governance. Enhanced employee training programs and growing awareness about data handling risks further support market growth. The convergence of stringent regulations and heightened security consciousness across industries is accelerating adoption, positioning DLP solutions as a strategic necessity for modern enterprises.
U.S. Data Loss Prevention (DLP) Solutions Market was valued at USD 0.73 billion in 2023 and is expected to reach USD 4.46 billion by 2032, growing at a CAGR of 22.32% from 2024-2032.
This significant growth is driven by increasing incidents of data breaches, stricter data privacy regulations such as CCPA and HIPAA, and rising awareness among enterprises regarding the importance of safeguarding sensitive information. The rapid digital transformation across industries, coupled with the widespread adoption of cloud services and remote work environments, has amplified the need for robust DLP solutions. Additionally, the growing emphasis on cybersecurity training and policy enforcement is prompting businesses to invest in comprehensive data protection strategies, fueling market expansion across the U.S
Get More Information on Data Loss Prevention (DLP) Solutions Market - Request Sample Report
Market Dynamics
Drivers
-
Growing concerns over data breaches and regulatory compliance fuel the demand for DLP solutions across industries.
Data breaches have become a significant concern for businesses globally, prompting a strong demand for Data Loss Prevention (DLP) solutions. With the increasing number of cyberattacks, businesses face an escalating risk of unauthorized access to sensitive data. Regulatory frameworks such as GDPR, CCPA, and HIPAA require organizations to implement stringent data security measures, making DLP systems crucial for maintaining compliance. Failing to comply with these regulations can result in hefty fines and reputation damage. As companies seek to prevent data loss and meet legal requirements, the market for DLP solutions has seen consistent growth. Enhanced data protection helps organizations safeguard customer trust and maintain operational integrity while minimizing the risks associated with breaches and non-compliance.
Restraints
-
Challenges in managing false positives and performance issues hamper the effectiveness of DLP solutions.
One of the key challenges faced by organizations using Data Loss Prevention (DLP) solutions is the management of false positives. DLP systems often flag legitimate data transfers as potential threats, leading to unnecessary disruptions in workflows. These false alarms require additional resources to review and resolve, causing inefficiencies and increasing the burden on IT teams. Furthermore, DLP systems can impact system performance by consuming significant resources, leading to slower operations and decreased productivity. Balancing the need for robust data protection with minimal interference in daily operations presents a difficult challenge. As DLP solutions evolve, addressing these issues of accuracy and system performance remains crucial to improving their overall effectiveness.
Opportunities
-
Increasing demand for cloud-based DLP solutions presents significant growth opportunities in the market.
The rapid adoption of cloud computing presents significant opportunities for the growth of Data Loss Prevention (DLP) solutions. As more organizations migrate their data and applications to the cloud, the need to protect sensitive information stored and shared across cloud environments becomes increasingly important. Cloud-based DLP solutions offer scalability and flexibility, enabling businesses to secure their data without the need for heavy on-premise infrastructure. These solutions can easily integrate with various cloud platforms such as AWS, Microsoft Azure, and Google Cloud, offering real-time monitoring and protection. The growing reliance on cloud storage, combined with rising cybersecurity threats, positions cloud-based DLP systems as a critical tool for ensuring data security in modern enterprise environments, driving strong market expansion.
Challenges
-
Evolving cyber threats and sophisticated attack techniques make it difficult to keep DLP solutions up to date.
The rapid evolution of cyber threats presents a significant challenge for Data Loss Prevention (DLP) solutions. Hackers continuously develop more sophisticated attack techniques, including advanced malware, phishing, and insider threats, which are harder for traditional DLP systems to detect and prevent. As cybercriminals adapt their methods, DLP solutions must evolve to keep pace with new vulnerabilities and emerging threats. This constant need for updates and enhancements can place a strain on organizations' security teams, who must stay vigilant and responsive. Keeping DLP systems up to date with the latest threat intelligence requires ongoing investment in technology and expertise. As cyber threats become more complex, maintaining the effectiveness of DLP solutions remains a significant challenge.
Segment Analysis
By Deployment
The Cloud-based segment dominated the Data Loss Prevention (DLP) Solutions Market in 2023 with the highest revenue share of about 55%. This dominance can be attributed to the increasing adoption of cloud-based services by organizations for data storage and management. Cloud DLP solutions offer scalability, cost efficiency, and remote accessibility, which are crucial in preventing data loss across multiple devices and locations. Additionally, the rise in cloud-based applications, coupled with enhanced security features, has propelled the growth of cloud-based DLP solutions.
The On-premises segment is expected to grow at the fastest CAGR of about 23.52% from 2024-2032. This growth is driven by organizations’ desire to maintain greater control over their data security and infrastructure. On-premises DLP solutions provide a higher level of customization, control, and data privacy, particularly for industries with strict regulatory compliance requirements. As data protection concerns intensify and businesses aim to secure sensitive information, the on-premises segment is anticipated to see rapid expansion.
By Enterprise Size
The Large Enterprise segment dominated the Data Loss Prevention (DLP) Solutions Market in 2023 with the highest revenue share of about 59%. This is due to the greater need for large organizations to safeguard vast amounts of sensitive data across multiple departments and locations. Large enterprises have the financial resources and infrastructure to invest in comprehensive DLP solutions, enabling them to address the increasing threat landscape. Additionally, their complex networks and higher data volume contribute to the market share dominance.
The Small and Medium Enterprise (SMEs) segment is expected to grow at the fastest CAGR of about 23.59% from 2024-2032. SMEs are increasingly adopting DLP solutions as they realize the importance of protecting sensitive data against cyber threats and breaches. With the rise in digitalization and cloud-based solutions, SMEs are becoming more aware of data security risks and the need for cost-effective DLP solutions. The growing adoption of cloud-based DLP and increased cybersecurity awareness will drive rapid growth in the SMEs segment.
By End-use
The BFSI segment dominated the Data Loss Prevention (DLP) Solutions Market in 2023 with the highest revenue share of about 23%. The BFSI sector deals with large volumes of sensitive data, including financial transactions, customer details, and regulatory compliance information. As such, it requires robust DLP solutions to mitigate the risk of data breaches and financial fraud. The high value of sensitive data in this sector, coupled with stringent regulations, makes BFSI the leading industry for DLP solutions.
The Manufacturing segment is expected to grow at the fastest CAGR of about 25.57% from 2024-2032. Manufacturing companies are increasingly leveraging digital technologies and connected devices in their operations, creating new vulnerabilities for data breaches and intellectual property theft. As manufacturing processes become more digitized, the need for robust DLP solutions to protect proprietary information and operational data grows. This sector's rapid digital transformation is a major driver for the fast growth of DLP solutions in the manufacturing industry.
By Software
The Data Center/Storage-based DLP segment dominated the Data Loss Prevention (DLP) Solutions Market in 2023 with the highest revenue share of about 48%. This dominance can be attributed to the centralization of data storage in data centers, which requires strong DLP mechanisms to secure sensitive data. As organizations store massive amounts of data in centralized locations, the demand for data loss prevention in these environments is critical to safeguarding valuable information from breaches and unauthorized access, driving the dominance of data center-based solutions.
The Endpoint DLP segment is expected to grow at the fastest CAGR of about 23.66% from 2024-2032. As the number of endpoint devices, such as laptops, smartphones, and tablets, increases, organizations are focusing more on securing these devices from data breaches. Endpoint DLP solutions help prevent data loss from endpoints, which are often the weakest link in an organization's security chain. The growing trend of remote work, along with the increasing number of mobile and IoT devices, will drive the demand for endpoint DLP solutions.
By Services
The Consulting Services segment dominated the Data Loss Prevention (DLP) Solutions Market in 2023 with the highest revenue share of about 40%. Consulting services are essential for businesses to assess their security needs and implement DLP solutions effectively. As organizations seek to align DLP strategies with their security goals, consulting services help design customized solutions and ensure compliance with industry regulations. The expertise provided by consultants in planning, deployment, and monitoring drives the continued dominance of consulting services in the DLP market.
The Managed Security Services segment is expected to grow at the fastest CAGR of about 24.14% from 2024-2032. As cyber threats become more sophisticated, organizations are increasingly relying on third-party managed security services to monitor and protect their networks. These services provide round-the-clock support and help businesses implement and manage their DLP solutions more effectively. The growing complexity of security threats, along with the shortage of skilled cybersecurity professionals, is driving the fast growth of managed security services in the DLP market.
By Application
The Encryption segment dominated the Data Loss Prevention (DLP) Solutions Market in 2023 with the highest revenue share of about 28%. Encryption is one of the most effective methods for securing sensitive data from unauthorized access. As data privacy regulations such as GDPR and CCPA become more stringent, businesses are adopting encryption technologies to ensure compliance and safeguard customer data. The increasing number of cyber threats and the importance of data confidentiality further cement encryption as a key component in DLP solutions.
The Policy, Standards, and Procedures segment is expected to grow at the fastest CAGR of about 26.28% from 2024-2032. With the rise of data protection regulations and the need for organizations to implement comprehensive data security strategies, policies and procedures are becoming critical in mitigating data loss risks. The growing emphasis on data governance, along with the need for businesses to stay compliant with evolving regulations, is driving the demand for DLP solutions focused on policies, standards, and procedural frameworks.
Regional Analysis
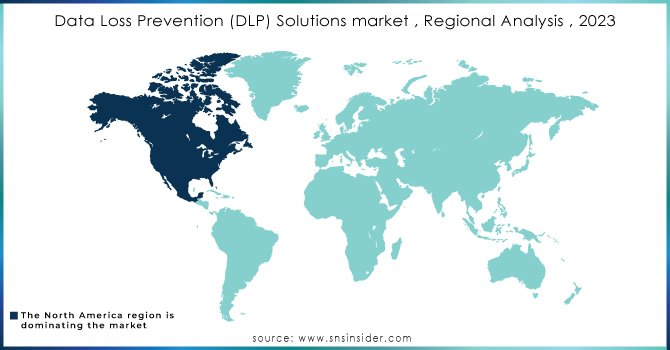
North America dominated the Data Loss Prevention (DLP) Solutions Market in 2023 with the highest revenue share of about 38%. The region’s dominance is primarily due to the presence of major technology companies, robust cybersecurity infrastructure, and stringent regulatory frameworks such as GDPR and CCPA. High levels of digitalization across industries, combined with increasing cyber threats and a strong focus on data privacy, have driven the adoption of DLP solutions in North America, making it the largest market for data protection technologies.
Asia Pacific is expected to grow at the fastest CAGR of about 24.92% from 2024-2032. This rapid growth is attributed to the increasing digital transformation across various sectors, such as BFSI, healthcare, and manufacturing, in emerging economies. The growing need for data protection amidst rising cyber threats and expanding e-commerce platforms is fueling the demand for DLP solutions. Additionally, the shift toward cloud computing and mobile technology in the region is further driving the adoption of advanced DLP systems.
Get Customized Report as per Your Business Requirement - Request For Customized Report
Key Players
-
BlackBerry (BlackBerry Protect, BlackBerry Guard)
-
Broadcom, Inc. (Symantec Data Loss Prevention, CloudSOC)
-
CheckPoint (Data Loss Prevention Software Blade, SmartEvent)
-
Cisco Systems, Inc. (Cisco Cloudlock, Cisco Umbrella DLP)
-
Citrix Systems (Citrix Analytics for Security, Citrix Secure Workspace Access)
-
CrowdStrike (Falcon Device Control, Falcon Data Protection)
-
Digital Guardian Inc. (Digital Guardian Endpoint DLP, Digital Guardian Network DLP)
-
IBM (IBM Security Guardium, IBM Security Discover and Classify)
-
Mcafee LLC (McAfee Total Protection for DLP, McAfee ePolicy Orchestrator)
-
Microsoft (Microsoft Purview Data Loss Prevention, Microsoft Defender for Cloud Apps)
-
proofprint (Proofpoint Enterprise DLP, Proofpoint Email DLP)
-
SAP SE (SAP Enterprise Threat Detection, SAP Data Custodian)
-
Sophos Ltd. (Sophos Endpoint DLP, Sophos Email DLP)
-
Trend Micro (Trend Micro Integrated DLP, Trend Micro Cloud App Security)
-
VMware, Inc. (VMware Workspace ONE Intelligence, VMware Carbon Black Cloud)
-
Palo Alto Networks (Enterprise DLP, Prisma Access)
-
GTB Technologies (Inspector DLP, Endpoint Protector)
-
InfoWatch (InfoWatch Traffic Monitor, InfoWatch Endpoint Security)
-
Fortra (Digital Guardian by Fortra, Clearswift Adaptive DLP)
Recent Developments:
-
In September 2023, Check Point Software Technologies acquired Atmosec, a SaaS security startup specializing in identifying and disconnecting malicious SaaS applications, preventing risky third-party communications, and rectifying misconfigurations.
-
In May 2023, IBM acquired Polar Security, a leader in data security posture management (DSPM), to enhance cloud data protection by automating the discovery, monitoring, and securing of sensitive data across cloud and SaaS applications.
| Report Attributes | Details |
|---|---|
| Market Size in 2023 | US$ 2.66 Billion |
| Market Size by 2032 | US$ 16.48 Billion |
| CAGR | CAGR of 22.52% From 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Software (Network DLP, Endpoint DLP, Data Center/Storage based DLP) • By Services (Managed Security Services, Consulting Services, Others) • By Deployment (On-premises, Cloud-based) • By Enterprise Size (Small and Medium Enterprise (SMEs), Large Enterprise) • By Application (Encryption, Centralized Management, Policy Standards and Procedures, Web and Email Protection, Cloud Storage, Incident Response and Workflow Management) • By End-use (BFSI, IT and Telecommunication, Retail and Logistics, Healthcare, Manufacturing, Government, Others) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles | BlackBerry, Broadcom, Inc., CheckPoint, Cisco Systems, Inc., Citrix Systems, CrowdStrike, Digital Guardian Inc., IBM, Mcafee LLC, Microsoft, proofprint, SAP SE, Sophos Ltd., Trend Micro, VMware, Inc., Palo Alto Networks, GTB Technologies, InfoWatch, Fortra |

