Endpoint Security Market Report Scope & Overview:
Get more information on Endpoint Security Market - Request Sample Report
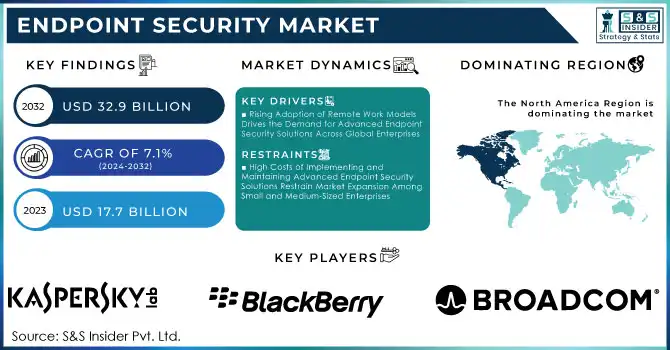
The Endpoint Security Market Size was valued at USD 17.7 billion in 2023 and is expected to reach USD 32.9 billion by 2032 and grow at a CAGR of 7.1% over the forecast period 2024-2032.
The endpoint security market is expanding rapidly due to the rising sophistication of cyber threats, the shift towards remote work, and the growing reliance on cloud-based infrastructures. Organizations are increasingly adopting advanced security measures to protect a wide range of devices, including desktops, laptops, mobile phones, and servers, from ransomware, phishing attacks, and other cyber threats. With the increasing complexity of attacks, businesses are now prioritizing endpoint security solutions that offer both threat prevention and response capabilities. Cloud-based endpoint security platforms, in particular, have become essential as they allow for real-time threat monitoring, rapid deployment of updates, and enhanced protection across distributed networks. For instance, in June 2024, Acronis announced the expansion of its endpoint security capabilities through its new Extended Detection and Response (XDR) solution designed specifically for managed service providers (MSPs). This solution integrates advanced threat detection and automated response features, enabling MSPs to better protect small and medium-sized enterprises (SMEs). By offering a more comprehensive solution that goes beyond traditional endpoint protection, Acronis allows MSPs to detect and respond to increasingly complex cyber threats faster and more effectively. This reflects the growing trend in the endpoint security market towards providing enhanced tools for service providers who are managing the security of multiple clients at scale.
Additionally in June 2024, MedCity News highlighted the increasing focus on preventative care in endpoint security strategies. Organizations are shifting from reactive measures to proactive ones, investing in solutions that prevent attacks before they occur. This preventative approach is particularly crucial in sectors such as healthcare, where protecting sensitive data is paramount. Advanced AI-driven threat detection, encryption, and multi-factor authentication are being deployed to secure endpoints and reduce the risk of breaches. This proactive stance in endpoint security highlights the shift towards more strategic investment in protecting digital assets, with companies aiming to safeguard their operations from the outset rather than responding after an incident.
Furthermore, in June 2024, Acronis further expanded its portfolio by moving beyond traditional endpoint protection with the introduction of its XDR solution, which integrates endpoint security with broader cybersecurity measures, including network protection, cloud workload defense, and incident response capabilities. This development underscores the demand for all-in-one security platforms that can protect organizations across their entire IT infrastructure. The integrated approach reflects the market’s evolution towards comprehensive security solutions, allowing businesses to address threats across multiple layers of their operations rather than focusing solely on individual endpoints. Acronis’s move to offer such a solution demonstrates how companies are responding to the need for multi-faceted protection as cyber threats continue to grow more sophisticated.
Endpoint Security Market Dynamics:
Drivers:
-
Rising Adoption of Remote Work Models Drives the Demand for Advanced Endpoint Security Solutions Across Global Enterprises
The shift toward remote work, accelerated by the pandemic and now becoming a long-term trend, has significantly increased the demand for advanced endpoint security solutions. With employees accessing company networks from various locations and devices, organizations face heightened risks of cyberattacks, including malware, ransomware, and phishing. The traditional security perimeter has expanded, necessitating more robust endpoint protection systems to safeguard sensitive corporate data. As businesses increasingly rely on cloud-based applications and remote connectivity tools, the need for solutions that provide real-time monitoring, threat detection, and response has surged. Endpoint security platforms now play a crucial role in managing and securing remote work environments, ensuring that devices outside the corporate network are fully protected. This trend is expected to drive further innovation in endpoint security technologies, particularly those offering cloud-native solutions and enhanced user authentication mechanisms.
-
Increasing Cyber Threats and Sophisticated Attacks Propel the Adoption of Endpoint Detection and Response (EDR) Solutions
The growing frequency and sophistication of cyberattacks, such as ransomware, zero-day exploits, and advanced persistent threats (APTs), have led to a sharp increase in the adoption of Endpoint Detection and Response (EDR) solutions. These solutions offer advanced threat detection, investigation, and remediation capabilities, making them essential tools for modern cybersecurity strategies. EDR platforms continuously monitor endpoint activities, providing real-time visibility into potential threats and enabling faster incident response. The increasing use of AI and machine learning in these solutions has further enhanced their ability to detect anomalous behavior and mitigate threats before they cause significant damage. As cybercriminals continue to develop more complex attack techniques, organizations are investing in EDR tools to strengthen their defenses and protect their data, driving the growth of the endpoint security market.
Restraint:
-
High Costs of Implementing and Maintaining Advanced Endpoint Security Solutions Restrain Market Expansion Among Small and Medium-Sized Enterprises
While large enterprises can afford to invest in sophisticated endpoint security platforms, small and medium-sized enterprises (SMEs) often face financial barriers when implementing advanced solutions. The high costs associated with purchasing, deploying, and maintaining comprehensive endpoint security systems can be prohibitive for smaller businesses. Additionally, the need for skilled IT staff to manage these solutions further increases operational expenses. Many SMEs may opt for more basic security measures or free solutions, which can leave them vulnerable to cyber threats. This financial restraint can slow down the adoption of advanced endpoint security technologies in the SME sector, limiting market growth. Vendors are working to address this issue by offering more cost-effective, scalable solutions for smaller businesses, but the high initial investment remains a significant restraint.
Opportunity:
-
Rising Adoption of AI and Machine Learning in Endpoint Security Creates New Growth Opportunities for Market Players
The integration of artificial intelligence (AI) and machine learning (ML) technologies into endpoint security solutions presents a significant growth opportunity for market players. AI and ML enhance the ability of security platforms to detect, analyze, and respond to threats in real-time, even as cyberattacks become more sophisticated and complex. These technologies enable solutions to automatically learn from historical data, identify patterns, and predict potential threats, reducing the reliance on manual intervention. As organizations look to improve the efficiency and accuracy of their security measures, the demand for AI-driven endpoint security solutions is expected to grow. Companies that invest in AI and ML capabilities will be well-positioned to capture this emerging market opportunity, offering advanced solutions that provide better threat detection and faster incident response times.
Challenge:
-
Balancing Security and User Privacy Presents a Significant Challenge for Endpoint Security Solution Providers
One of the key challenges in the endpoint security market is maintaining a balance between robust security measures and user privacy. While endpoint security platforms are designed to monitor and secure devices, they often require access to sensitive user data, including personal files, emails, and browsing activity. This can raise concerns among users and businesses about potential privacy infringements. Moreover, strict regulatory frameworks, such as GDPR in Europe and similar laws in other regions, place limitations on how much data can be collected and monitored without explicit user consent. Endpoint security solution providers must navigate these privacy concerns while ensuring that their products offer comprehensive protection against cyber threats. Finding the right balance between security effectiveness and privacy protection is a complex challenge, but it is crucial for maintaining user trust and regulatory compliance.
Endpoint Security Market Segmentation Overview
By Component
The Software segment dominated the endpoint security market in 2023, accounting for approximately 60% of the market share. The demand for advanced software solutions in endpoint security has grown significantly as organizations seek more robust tools to combat increasingly sophisticated cyber threats. Endpoint protection software, including Endpoint Detection and Response (EDR) and Endpoint Protection Platforms (EPP), are being widely adopted across industries due to their ability to provide real-time monitoring, threat detection, and response capabilities. Companies like Acronis, with its XDR launch in June 2024, are expanding their software offerings to meet the growing need for integrated, AI-driven security solutions, further propelling the dominance of software in this segment.
By Deployment
The Cloud-based deployment dominated the endpoint security market in 2023, accounting for around 65% of the market share. The shift towards remote work and the growing reliance on cloud-based applications have driven the adoption of cloud-based endpoint security solutions. Cloud platforms offer flexibility, scalability, and real-time updates, making them ideal for businesses managing distributed workforces. Cloud-based solutions also allow for better integration with other cloud services, reducing the need for complex on-premise infrastructures. For example, Acronis' cloud-enabled security solutions for managed service providers (MSPs) highlight the growing demand for cloud deployment in endpoint security, ensuring seamless protection for remote users and decentralized networks.
By Solution Type
The Endpoint Detection and Response (EDR) segment dominated the endpoint security market in 2023, holding approximately 55% of the market share. The increasing sophistication of cyberattacks, such as ransomware and advanced persistent threats (APTs), has made EDR solutions essential for businesses. EDR platforms offer advanced threat detection, continuous monitoring, and faster response to potential threats, making them crucial in high-risk environments. The integration of AI and machine learning in EDR tools enhances their ability to detect unknown threats, as seen in Acronis’ XDR launch in June 2024, which demonstrates the growing focus on solutions that can proactively address complex attacks beyond traditional protection.
By End-user
The commercial segment dominated the endpoint security market in 2023 and accounted for about 70% of the market share. Businesses in sectors like BFSI, IT, and healthcare face heightened cyber threats, making endpoint security a critical investment. Companies are increasingly adopting advanced security solutions to protect sensitive data, prevent costly breaches, and comply with regulatory requirements. Commercial enterprises are also leveraging AI-driven tools to manage complex security infrastructures. For example, the healthcare industry is placing a growing emphasis on proactive endpoint security measures, as seen in the June 2024 focus on preventative care to safeguard sensitive patient data.
By End-use Industry
The IT and Telecommunications segment dominated the endpoint security market in 2023, accounting for approximately 30% of the market share. This sector’s reliance on connected devices, cloud computing, and digital infrastructure makes it a prime target for cyberattacks. As a result, IT and telecom companies invest heavily in endpoint security solutions to protect their expansive and often distributed networks. The growing demand for remote work and digital communication platforms has further increased the need for real-time threat detection and protection. For instance, Acronis' expanded security offerings, including cloud-based solutions, are critical for IT and telecom sectors that prioritize comprehensive endpoint security strategies.
Endpoint Security Market Regional Analysis
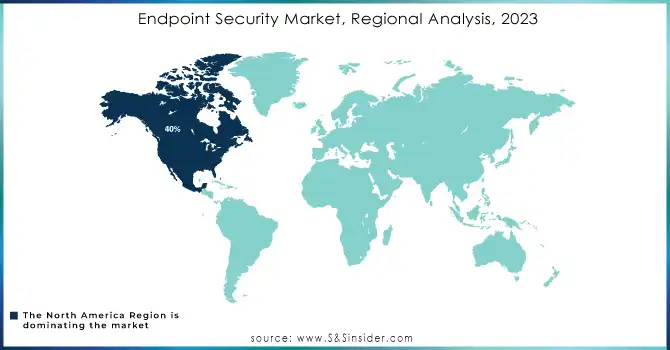
The North American region dominated the endpoint security market in 2023, accounting for approximately 40% of the market share. The region’s dominance is due to the innovative technology, strong cybersecurity infrastructure, and early adoption of advanced security solutions have contributed to its dominance. Major enterprises across sectors like BFSI, IT, and healthcare in the U.S. and Canada prioritize endpoint security to mitigate the increasing frequency of cyberattacks. Moreover, companies such as Acronis, with headquarters in Switzerland but a significant presence in North America, have been launching advanced security solutions like Extended Detection and Response (XDR) to cater to the high demand in the region. The growing need to protect remote workforces and critical digital infrastructure further propels the demand for endpoint security solutions in this region.
Moreover, Asia-Pacific emerged as the fastest-growing region in the endpoint security market in 2023, with an estimated CAGR of around 12%. The rapid digitalization across industries, increasing internet penetration, and the rising adoption of remote work models have accelerated the demand for endpoint security solutions in countries like China, India, and Japan. The region is also experiencing a surge in cyberattacks, prompting governments and enterprises to invest in advanced security solutions. For instance, companies in sectors like IT, telecommunications, and BFSI are driving the demand for real-time threat detection and response solutions. The growing presence of global security firms in Asia-Pacific, coupled with rising investments in AI-driven endpoint security tools, is further fueling this market's expansion in the region.
Need any customization research on Endpoint Security Market - Enquiry Now
Key Players in Endpoint Security Market
-
AO Kaspersky Lab (Kaspersky Endpoint Security, Kaspersky Security Cloud)
-
BlackBerry Limited (BlackBerry Protect, BlackBerry Dynamics)
-
Broadcom (Symantec Endpoint Protection, Symantec Endpoint Detection and Response)
-
Check Point Software Technologies Ltd. (Check Point Endpoint Security, Check Point SandBlast Agent)
-
Cisco Systems Inc. (Cisco AMP for Endpoints, Cisco Secure Endpoint)
-
Comodo Security Solutions, Inc. (Comodo Advanced Endpoint Protection, Comodo Endpoint Security Manager)
-
CrowdStrike (CrowdStrike Falcon Prevent, CrowdStrike Falcon Insight)
-
CurrentWare (CurrentWare Endpoint Security, CurrentWare BrowseControl)
-
Cybereason, Inc. (Cybereason Endpoint Detection and Response, Cybereason Malop)
-
Druva Inc. (Druva inSync, Druva Phoenix)
-
Fidelis Cybersecurity (Fidelis Endpoint, Fidelis Deception)
-
FireEye, Inc. (FireEye Endpoint Security, FireEye Helix)
-
Forcepoint LLC (Forcepoint Endpoint Security, Forcepoint Threat Protection)
-
McAfee, LLC (McAfee Endpoint Security, McAfee MVISION Endpoint)
-
Microsoft Corporation (Microsoft Defender for Endpoint, Microsoft 365 Defender)
-
Palo Alto Networks (Cortex XDR, Palo Alto Networks Traps)
-
SentinelOne (SentinelOne Singularity, SentinelOne Ranger)
-
Sophos Group plc (Sophos Intercept X, Sophos Central)
-
Symantec Corporation (Symantec Endpoint Security, Symantec Advanced Threat Protection)
-
Trend Micro Incorporated (Trend Micro Apex One, Trend Micro OfficeScan)
Security Software Vendors in the Endpoint Security Market
-
CrowdStrike
-
McAfee
-
Symantec (Broadcom)
-
Check Point Software Technologies
-
Trend Micro
Managed Security Service Providers (MSSPs) in the Endpoint Security Market
-
Secureworks
-
Trustwave
-
IBM Security Services
-
AT&T Cybersecurity
-
Verizon Business
| Report Attributes | Details |
|---|---|
| Market Size in 2023 | US$ 17.7 Billion |
| Market Size by 2032 | US$ 32.9 Billion |
| CAGR | CAGR of 7.1% From 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | •By Component (Software, Services) •By Deployment (Cloud, On-Premises) •By Solution Type (Endpoint Protection Platform, Endpoint Detection and Response) •By End-user (Commercial, Consumer) •By End-use Industry (BFSI, IT and Telecommunications, Retail, Healthcare, Government & Public Sector, Transportation, Others) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe [Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles | Broadcom, CrowdStrike, Check Point Software Technologies Ltd., BlackBerry Limited, Comodo Security Solutions, Inc., AO Kaspersky Lab, SentinelOne, Trend Micro Incorporated, McAfee, LLC, Microsoft Corporation, Cisco Systems Inc., FireEye, Inc., CurrentWare, Cybereason, Inc., Druva Inc., Fidelis Cybersecurity, Forcepoint LLC and other key players |
| Key Drivers | • Rising Adoption of Remote Work Models Drives the Demand for Advanced Endpoint Security Solutions Across Global Enterprises • Increasing Cyber Threats and Sophisticated Attacks Propel the Adoption of Endpoint Detection and Response (EDR) Solutions |
| RESTRAINTS | • High Costs of Implementing and Maintaining Advanced Endpoint Security Solutions Restrain Market Expansion Among Small and Medium-Sized Enterprises |