Security Orchestration, Automation, and Response (SOAR) Market Key Insights:
To Get More Information on Security Orchestration, Automation, and Response (SOAR) Market - Request Sample Report
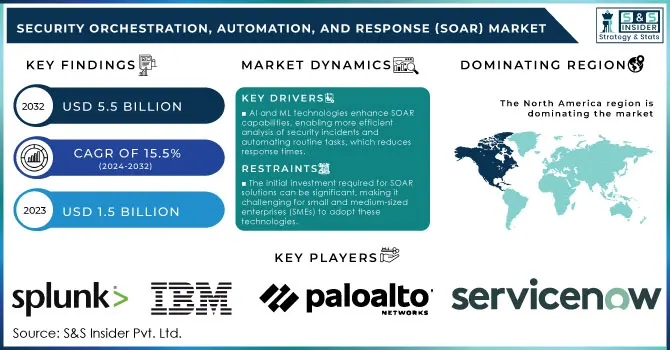
The Security Orchestration, Automation, and Response (SOAR) Market Size was valued at USD 1.5 Billion in 2023 and is expected to reach USD 5.5 Billion by 2032, growing at a CAGR of 15.5% over the forecast period 2024-2032.
The growth of the Security Orchestration, Automation, and Response (SOAR) market is probably attributable to the complicated nature of cyber threats and their ever-increasing frequency supported by some concerning statistics from various government agencies. According to the Federal Bureau of Investigation (FBI), cybercrime has surged, with reported incidents increasing by over 69% from 2020 to 2021, leading to losses exceeding $6.9 billion in the U.S. alone. The increase in cyber threats is driving organizations' adoption of sophisticated cybersecurity solutions, leading to increased investment in SOAR technologies.
Meanwhile, SOAR adoption has been further propelled by the National Cyber Security Centre (NCSC) urging organizations to enhance incident response capabilities. As the U.S. government invests heavily into new infrastructure and cybersecurity plans, more organizations understand they need some sort of automated response to deal with risks around breaches and security incidents. SOAR solutions provide better security tool integration and improved incident detection and response times while enhancing the management of security orchestration operations to protect assets. The government’s proactive approach to cybersecurity and the necessity for organizations to comply with regulatory requirements are major factors fuelling the growth of the SOAR market, establishing it as an essential component of modern cybersecurity strategies.
Market Dynamics
Drivers
-
The growing sophistication and frequency of cyberattacks have heightened the need for advanced security solutions, prompting organizations to adopt SOAR platforms for effective threat detection and response.
-
AI and ML technologies enhance SOAR capabilities, enabling more efficient analysis of security incidents and automating routine tasks, which reduces response times.
-
Organizations face pressure to respond quickly to security incidents to minimize damage, and SOAR solutions streamline and automate response workflows.
Increased cybersecurity threats faced by Organizations worldwide have been one of the prime factors driving the Security Orchestration, Automation, and Response (SOAR) market. Cybersecurity Ventures has found that the global costs of cybercrime could exceed $10.5 trillion per year by 2025, making a strong case for increased security in the current climate. The increase in cyber threats such as ransomware attacks and phishing schemes has caused organizations to look for all-in-one solutions that will help improve overall security posture. As an example, in May 2021 the Colonial Pipeline ransomware attack caused shortages of fuel along the Eastern U.S., demonstrating the disruptive impact that cyber incidents can have. Those high-profile attacks have prompted enterprises to enhance their incident response capabilities, including the use of SOAR platforms that can automate the detection of threats and orchestrate workflows tied to threat response. By integrating multiple security tools and automating repetitive tasks, SOAR solutions enable security teams to respond to incidents faster and more effectively.
In addition, IBM conducted a survey and found that organizations using automation in their security operations were able to reduce response time to incidents by 20% when compared to organizations that relied on manual processes. It illustrates the power of SOAR in combating a growing threat surface, enabling security professionals to spend more time on strategic operations and less time conducting repetitive incident response processes. Thus, with the rapid evolution of cyber threats, SOAR solutions will continue to gain traction and will become an essential element of modern cybersecurity strategy.
Restraints
-
The initial investment required for SOAR solutions can be significant, making it challenging for small and medium-sized enterprises (SMEs) to adopt these technologies.
-
Integrating SOAR solutions with existing security infrastructure and workflows can be complex and time-consuming, leading to potential resistance from IT teams.
The major restraining factor in the Security Orchestration, Automation, and Response (SOAR) market is the high complexity of integration. With varying tools and technologies in cyber security, most organizations have trouble integrating SOAR solutions into their pre-existing technology stack and workflows. Every solution may have its own type of protocols, interface, and data format which makes integration very complex. This intricate nature usually demands significant time and effort, resulting in delays in deployment and operational challenges.
Additionally, the process can be resisted by IT teams reluctant to disrupt established workflows or learn new systems. As a result, organizations might underutilize SOAR capabilities or fail to realize their full potential, which can hinder overall effectiveness in managing and responding to security incidents. Therefore, addressing integration challenges is critical for successful SOAR implementation.
Segment Analysis
By enterprise size
The large enterprise segment held the largest market share of 55% in 2023, owing to rising demand for complete security solutions among large enterprises. The National Institute of Standards and Technology (NIST) warns that cyber threats become more sophisticated with large enterprises being more likely to experience sophisticated cyber threats due to their extensive digital infrastructure and vast data repositories. Consequently, they need advanced SOAR tools to analyze and respond to these security incidents. Government reports indicate that over 70% of large enterprises experienced data breaches in the past year, highlighting the urgent need for robust cybersecurity measures. These organizations typically have specialized security teams tasked with handling highly complex security environments, making SOAR an ideal solution for streamlining security operations and automating incident response. The function of streamlining the enterprise security tools and having consolidated visibility into security events improves the incident-hunting capabilities of large enterprises and helps mitigate them faster. Scalable and customizable SOAR solutions are built to cater to the unique needs of larger organizations, which is expected to fuel growth in this segment in the coming years.
By application
In 2023, the Incident Response segment held a dominant market share of 38% as incidents require timely actions to handle threats which boosts the demand for incident response technologies. According to the Cybersecurity & Infrastructure Security Agency (CISA), organizations are increasingly prioritizing rapid response to security incidents, as delayed responses can lead to significant data breaches and financial losses. Increasingly complex cyber threats require incident response strategies that SOAR platforms can help deliver and manage. According to government reports, 85% of organizations experienced at least one cyberattack with positive effects in the last year, which indicates the need for an incident response feature. Increasing regulatory demands and growing scrutiny on data protection have forced companies to rethink their incident response strategies, making it imperative to invest in SOAR solutions. SOAR technologies consolidate security tools and processes that allow for automation to be leveraged in responding to a security incident so the damage is limited while ensuring compliance with regulatory mandates. The increasing awareness of the need for efficient incident response solutions is likely to spur more investments in the SOAR market.
By Vertical
In 2023, the IT and telecommunications segment held the largest market share at 18.1% due to the increased risk cyber threats pose to this sector and the need for higher security levels. The telecom sector is now a central focus of attacks, with U.S. cyber-attack reports rising 46% from the previous year according to the Federal Communications Commission (FCC). With this sector becoming more reliant on digital infrastructure, the need for SOAR solutions to scale up security operations has grown. According to government statistics, more than 65% of the IT and telecom sector have already implemented or are set to multi-use SOAR technologies to enhance their security processes which ultimately helps in incident response. SOAR integration also allows these businesses to reduce security operations into a single platform, automate incident response capabilities, and increase readiness against cyber threats. SOAR solutions have already established a stronghold within this vertical, and continued adoption is anticipated as organizations face regulatory mandates related to data protection and risk management.
Regional Analysis
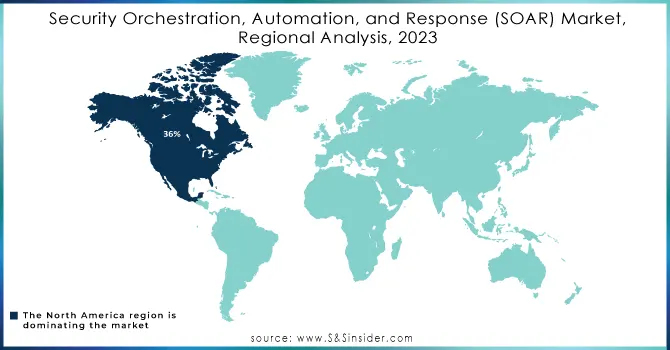
North America held the largest share of the SOAR market with 36%, in 2023 The dominance of the region is attributed to the presence of major cybersecurity companies, growing government efforts to improve existing cyber security, and a high number of reported incidents in this region. SOAR solutions are also driven by the increasing amount of money disbursed by the U.S. government to augment national cyber security, The National Cyber Security Strategy is designed to improve the incident response capabilities of critical infrastructure sectors, creating an environment that favors SOAR market development.
On the other hand, Asia-Pacific is expected to grow with the fastest CAGR during 2024-2032 due to rapid digital transformation initiatives in India, China, and Japan. As these economies increasingly embrace digitization, the surge in cyber threats has driven demand for end-to-end cybersecurity solutions (SOAR). In the Asia-Pacific region, cybercrime has grown by more than 50% in recent years, according to government statistics, and as a result, organizations are increasingly turning to sophisticated protective solutions. This region will witness lucrative growth in the SOAR market due to increasing awareness regarding automated incident response and orchestration tools among enterprises.
Do You Need any Customization Research on Security Orchestration, Automation, and Response (SOAR) Market - Inquire Now
Recent Developments
-
In March 2024, Cybersecurity Initiatives by the U.S. Government, the Biden Administration published related strategies to increase resiliency in federal agencies and its recommendation for usage of SOAR technologies for automated responses & incident management. The initiative focuses on increasing investment of up to $500 million for enhanced cybersecurity in multiple sectors.
-
D3 Security unveiled Smart SOAR in April 2023, a powerful new tier of its security orchestration, automation, and response (SOAR) solution focused on serving Managed Security Service Providers (MSSPs) and Managed Detection and Response (MDR) providers. Smart SOAR, on the other hand, automates threat evaluation and security incident resolution to simplify operations for these service providers.
-
Palo Alto Networks launched a new module called Identity Threat Detection and Response (ITDR) in Mar 2023. It allows customers to intake behavioral data and user identity and uses modern technologies like AI to detect And respond to (attacks) in no time. The ITDR module helps reduce operational complexity and improves incident response by incorporating identity analytics into a single Security Operations Center (SOC) platform
Key Players
Service Providers / Manufacturers:
-
Splunk (Splunk Phantom, Splunk SOAR)
-
IBM (IBM Resilient, IBM QRadar SOAR)
-
Palo Alto Networks (Cortex XSOAR, Cortex XDR)
-
ServiceNow (Security Operations, Incident Management)
-
Rapid7 (InsightConnect, Rapid7 SOAR)
-
Swimlane (Swimlane Platform, Swimlane SOAR)
-
Fortinet (FortiSOAR, FortiEDR)
-
McAfee (McAfee MVISION SOAR, McAfee Enterprise Security Manager)
-
LogRhythm (LogRhythm SOAR, LogRhythm SIEM)
-
Sumo Logic (Sumo Logic SOAR, Sumo Logic Cloud SIEM)
Users of SOAR Services / Products
-
Bank of America
-
Cisco
-
Walmart
-
Accenture
-
Dell Technologies
-
The Home Depot
-
Citi
-
AT&T
-
Johnson & Johnson
-
Pfizer
| Report Attributes | Details |
|---|---|
| Market Size in 2023 | USD 1.5 Billion |
| Market Size by 2032 | USD 5.5 Billion |
| CAGR | CAGR of 15.5% From 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Component (Solution, Services) • By Deployment Mode (On-Premises, Cloud) • By Organization Size (Large Enterprises, Small and Medium-sized Enterprises) • By Application (Threat Intelligence, Network Forensics, Incident Response, Compliance, Others) • By Vertical (BFSI, IT & Telecom, Retail & E-commerce, Healthcare, Manufacturing, Government, Education, Others) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles | Splunk, IBM, Palo Alto Networks, ServiceNow, Rapid7, Swimlane, Fortinet, McAfee, LogRhythm, Sumo Logic |
| Key Drivers | • The growing sophistication and frequency of cyberattacks have heightened the need for advanced security solutions, prompting organizations to adopt SOAR platforms for effective threat detection and response. • AI and ML technologies enhance SOAR capabilities, enabling more efficient analysis of security incidents and automating routine tasks, which reduces response times. |
| RESTRAINTS | • The initial investment required for SOAR solutions can be significant, making it challenging for small and medium-sized enterprises (SMEs) to adopt these technologies. |

