Identity and Access Management Market Size:
Get more information on Identity and Access Management Market - Request Sample Report
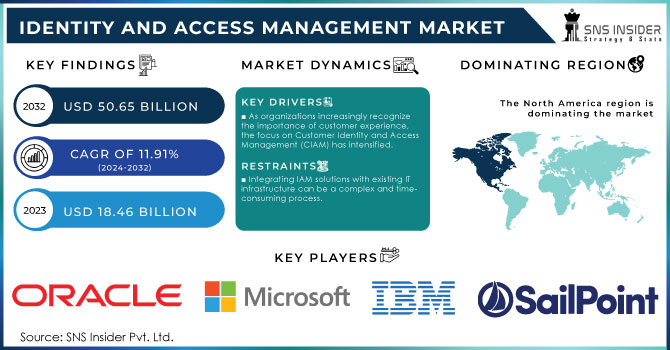
The Identity and Access Management Market was valued at USD 18.46 Billion in 2023 and is expected to reach USD 50.65 Billion by 2032, growing at a CAGR of 11.91% over the forecast period 2024-2032.
As businesses increasingly rely on digital platforms and cloud-based services, the importance of robust identity and access management (IAM) solutions has surged. They enable organizations to enforce policies governing user access, authenticate users, and provide role-based access controls to ensure that employees can only access the information necessary for their roles. As more organizations migrate their operations to the cloud, IAM solutions are critical for managing access to cloud applications and services. Approximately 60% of medium-sized companies experienced hacks that compromised employees' credentials, with incidents of social engineering, like phishing, affecting nearly half of these firms. The cost of data breaches is significant, averaging around USD 4.24 million, and with 74% of breaches originating from the misuse of privileged credentials, the need for robust security practices is clear. Alarmingly, over 80% of data breaches are linked to stolen, weak, or default passwords. In response to these threats, 91% of companies prioritize implementing password-less multi-factor authentication (MFA) to thwart credential theft and phishing attempts. Cloud-based IAM systems allow for centralized management of user identities across multiple platforms, which is essential for ensuring secure access to cloud resources. 53% of IT directors plan to upgrade their cloud security in 2024, making it a leading investment priority. However, only 38% of organizations feel they are effectively securing their cloud resources, with 26% acknowledging this as a major weakness. Data confidentiality emerges as a paramount concern, with 45% of IT directors identifying it as their primary objective for the upcoming year. This sentiment is echoed by 94% of CISOs and IT professionals who believe stronger protections are necessary beyond what Microsoft 365 and Google Workspace offer.
In the healthcare sector, for example, IAM solutions are crucial for managing access to sensitive patient information and ensuring compliance with regulations such as the Health Insurance Portability and Accountability Act (HIPAA). By implementing IAM technologies, healthcare organizations can protect patient data from unauthorized access, reduce the risk of data breaches, and streamline the authentication process for healthcare professionals. This not only enhances security but also improves operational efficiency by automating user provisioning and de-provisioning processes.
Market Dynamics
Drivers
-
As organizations increasingly recognize the importance of customer experience, the focus on Customer Identity and Access Management (CIAM) has intensified.
Since organizations need to allow their employees to work from remote locations and to ensure that they can access corporate resources securely, the demand for IAM solutions has increased significantly. Remote work is often associated with the use of personal devices to interact with company applications and data sources and this process can become an entry point for cybercriminals to attack organizations’ systems. IAM solutions help organizations manage user identity across multiple devices. This ensures that only authorized personnel can handle valuable information, irrespective of the device through which the data is accessed. Consequently, strong authentication measures, such as MFA, can be employed to protect access to resources through a given IAM solution, which, in turn, can be used to manage permissions at a super granular level. Finally, as a growing number of organizations decide to stick with remote work, ensuring a great user experience is likely to become a priority. IAM solutions should improve user experience by making it simple for employees to access platforms they manage through single sign-on. In conclusion, the growing focus on CIAM presents a significant opportunity for the IAM market. As organizations seek to balance security and user experience, the demand for robust CIAM solutions will continue to rise, further fueling market expansion.
-
The increasing shift toward cloud computing has transformed how organizations manage their IT infrastructure and applications.
Cloud-based Identity and access management solutions are adopted by many organizations due to their flexibility, scalability, and cost efficiency in support of the organization’s digital transformation efforts. These cloud IAM solutions offer secure access to cloud applications and services, allowing organizations to continue enforcing user identity and access controls across different cloud platforms. There are also cloud IAM solutions that can easily integrate with the organization’s existing applications and systems to support the different types of local and cloud-based resources to access. In addition, these cloud IAM solutions usually come with more extensive security features that include the ability to perform AI-driven analytics and machine learning to enable timely detection and response to unusual user activities in cloud applications. These advanced security features reduce the potential security risks of accessing cloud applications.
Restraints
-
Integrating IAM solutions with existing IT infrastructure can be a complex and time-consuming process.
Many organizations have diverse environments that include legacy systems, cloud applications, and various identity repositories, making seamless integration a significant challenge. This complexity can lead to extended implementation timelines and increased costs, as organizations may need to allocate additional resources to ensure successful integration. Additionally, organizations may face difficulties in maintaining consistency across different systems and applications, further complicating the IAM deployment process. Moreover, the lack of standardization in IAM solutions can lead to compatibility issues, as different vendors may use varying protocols and technologies. This can create additional hurdles for organizations seeking to implement a unified IAM strategy across their IT ecosystem. As a result, the complexity of integration may discourage organizations from adopting IAM solutions or lead them to opt for less comprehensive alternatives. This reluctance can hinder market growth and limit the effectiveness of IAM initiatives in enhancing security and compliance.
Market Segmentation
By Type
Workforce IAM dominated the market with more than 55% market share in 2023. It allows businesses to manage the access of employees to applications, systems, and data according to their roles and duties. Through the utilization of Workforce IAM solutions, companies can ensure that employees have the right access levels by enforcing policies like Single Sign-On (SSO), multi-factor authentication (MFA), and role-based access control (RBAC), thus reducing security threats. Okta and Microsoft provide organizations with strong Workforce IAM applications, allowing them to efficiently and securely handle user identities.
The consumer IAM is projected to become the fastest-growing segment during 2024-2032. CIAM solutions improve the customer's experience by allowing for secure authentication and authorization procedures, as well as gathering and evaluating user data for customized services. Auth0 and ForgeRock are among the companies that offer CIAM applications to assist businesses in effectively managing customer identities and providing easy-to-use authentication experiences.
By Offerings
The solutions segment dominated the market in 2023 with a 42% market share and is expected to have the fastest CAGR during 2024-2032. IAM solutions encompass various technologies and tools designed to manage user identities, access rights, and authentication processes across an organization’s digital landscape. This segment includes advanced technologies such as single sign-on (SSO), multi-factor authentication (MFA), and identity governance. The growing need for robust security measures due to increasing cyber threats and regulatory compliance drives demand for these solutions. Companies like Okta and SailPoint provide comprehensive IAM solutions that help organizations secure user access while streamlining user experiences and maintaining compliance with industry standards.
By Deployment Mode
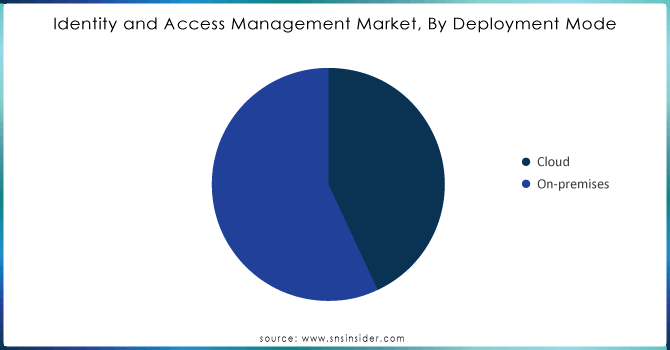
The on-premises segment led the market with over 56% market share in 2023. This deployment method includes setting up IAM solutions within a company's internal infrastructure and providing increased oversight of sensitive data and access management procedures. Organizations that place importance on data sovereignty, adherence to regulations, and personalized security measures typically favor this deployment approach. IBM Security Identity Governance and Intelligence and SailPoint IdentityNow are well-known on-premises IAM applications that offer strong solutions for identity governance, access control, and compliance management.
The cloud is expected to become the fastest-growing market during 2024-2032, due to its flexibility, scalability, and cost-effectiveness. Cloud-based IAM solutions enable organizations to centrally manage user identities and access controls, leading to simpler integration with different applications and services. In addition, the cloud model offers automatic updates and improved security measures to meet changing regulations. Prominent examples in this category are Okta Identity Cloud and Microsoft Azure Active Directory. They provide all-encompassing IAM solutions with features like single sign-on (SSO), multifactor authentication (MFA), and user provisioning.
Do you need any custom research on Identity and Access Management Market - Enquiry Now
Regional Analysis
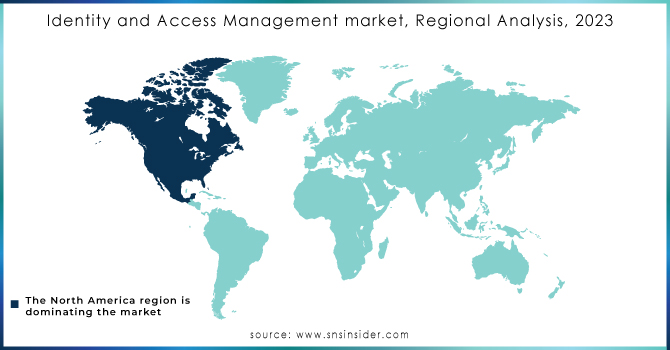
North America held a 38% market share in 2023, making it the leading region in the market. The dominance is greatly influenced by the participation of major companies such as IBM, Microsoft, and Oracle, along with state-of-the-art technological infrastructure. Organizations in different industries in the region are more and more implementing IAM solutions to improve security, simplify operations, and meet strict regulatory demands. Enterprise businesses frequently use tools such as Microsoft's Azure Active Directory and IBM Security Verify for secure management of access and identity governance.
Asia-Pacific is projected to grow at the fastest CAGR during 2024-2032, due to fast digital transformation and higher cybersecurity investments. Countries such as India, China, and Japan are at the forefront, as businesses are becoming aware of the significance of IAM in safeguarding sensitive information and adhering to regulatory standards. For example, enterprises in APAC are increasingly embracing Okta's Identity Cloud to simplify user access and enhance security measures, establishing it as a prominent player in this fast-growing market.
Key Players
The major key players in the Identity and Access Management Market are:
-
Microsoft (Azure Active Directory, Microsoft Identity Manager)
-
IBM (IBM Security Identity Governance and Intelligence, IBM Security Access Manager)
-
Oracle (Oracle Identity Cloud Service, Oracle Access Management)
-
SailPoint (SailPoint IdentityIQ, SailPoint Predictive Identity)
-
Okta (Okta Identity Cloud, Okta Workforce Identity)
-
Ping Identity (PingOne, PingFederate)
-
Duo Security (Duo Beyond, Duo Access)
-
CyberArk (CyberArk Privileged Access Security, CyberArk Identity)
-
ForgeRock (ForgeRock Identity Platform, ForgeRock Identity Gateway)
-
RSA Security (RSA SecurID Access, RSA Identity Governance and Lifecycle)
-
Auth0 (Auth0 Identity Platform, Auth0 Multifactor Authentication)
-
OneLogin (OneLogin Unified Access Management, OneLogin Identity Management)
-
LifeLock (LifeLock Identity Theft Protection, LifeLock Identity Monitoring)
-
Thales (Thales CipherTrust Data Security Platform, Thales SafeNet Trusted Access)
-
NetIQ (NetIQ Identity Manager, NetIQ Access Manager)
-
Centrify (Centrify Identity-Centric PAM, Centrify Cloud Service)
-
ID.me (ID.me Identity Verification, ID.me Digital Identity)
-
F5 Networks (F5 BIG-IP APM, F5 Access Policy Manager)
-
Micro Focus (Micro Focus Identity Governance, Micro Focus NetIQ Access Manager)
Manufacturers of devices for identity & access management market:
-
HID Global
-
Suprema Inc.
-
NEC Corporation
-
Thales Group
-
IDEMIA
-
ZKTeco
Recent Development
-
In September 2023, OneLogin introduced a new Identity Cloud solution that combines Single Sign-On (SSO), Multi-Factor Authentication (MFA), and advanced user behavior analytics.
-
In February 2024, Okta announced enhancements to its Identity Governance offering. This new feature set focuses on automating identity lifecycle management and ensuring compliance through advanced reporting and access reviews, which significantly streamline identity governance processes.
-
In January 2024, IBM released an update to its Security Verify platform, which integrates identity management with AI to provide real-time risk assessment and adaptive access controls.
-
In December 2023, Ping Identity launched a new password-less authentication feature as part of its Identity Security platform. This capability aims to reduce password-related risks while improving user convenience by allowing users to authenticate via biometrics or one-time passcodes
| Report Attributes | Details |
|---|---|
| Market Size in 2023 | USD 18.46 Billion |
| Market Size by 2032 | USD 50.65 Billion |
| CAGR | CAGR of 11.91% From 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Type (Workforce IAM, Consumer IAM) • By Offerings (Solution, Services) • By Solution (Data Directory, Identity Lifecycle Management, Authentication, Verification, Access Management and Authorization, Audit, Compliance, and Governance) • By Service (Integration and Deployment, Support and Maintenance, Consulting) • By Deployment Mode (Cloud, On-premises) • By Vertical (BFSI, Travel, Tourism and Hospitality, Healthcare, Retail and E-commerce, Education, Telecommunication and IT, Government and Defense, Others) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles | Microsoft, IBM, Oracle, SailPoint, Okta, Ping Identity, Duo Security, CyberArk, ForgeRock, RSA Security, Auth0, OneLogin, LifeLock, Thales, NetIQ, Centrify, ID.me, F5 Networks, Micro Focus |
| Key Drivers | • As organizations increasingly recognize the importance of customer experience, the focus on Customer Identity and Access Management (CIAM) has intensified. • The increasing shift toward cloud computing has transformed how organizations manage their IT infrastructure and applications. |
| RESTRAINTS | • Integrating IAM solutions with existing IT infrastructure can be a complex and time-consuming process. |

