Passwordless Authentication Market Size & Overview:
Get more information on Passwordless Authentication Market - Request Free Sample Report
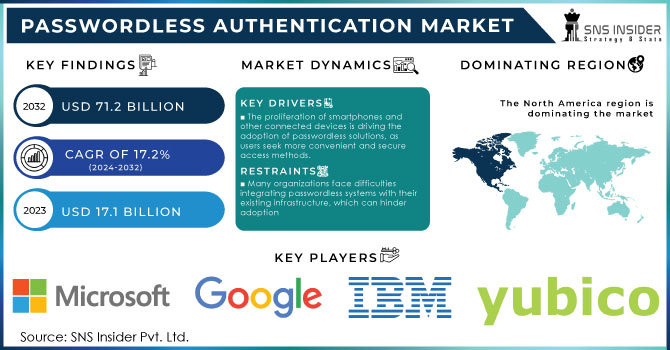
Passwordless Authentication Market size was valued at USD 17.1 billion in 2024 and is expected to grow to USD 71.2 billion by 2032 and grow at a CAGR of 17.2 % over the forecast period of 2024-2032.
Passwordless authentication market growth is driven by increasing demand for security measures. The need for enhanced safety is necessitated by the growing frequency of cyberattacks and data breaches. According to the U.S. Department of Homeland Security's 2023 report, over 70% of cyber intrusions in the past year stemmed from weak or compromised passwords, which further fueled the demand for passwordless solutions. Thus, the need for passwordless solutions has subsequently increased. Additionally, the digital identity program implemented by the European Union in mid-2023 also required all member states to implement robust identity verification. Both public and private entities across Europe are focusing on deploying passwordless systems since the systems are exempt from passwords which reduces both security breach risk and enhances user experience.
Governments globally are supporting the shift towards biometric and multi-factor authentication as part of the digital transformation. For instance, the Digital India campaign by the Indian Government will result in increased investment through 2024 where biometric verification is the primary security method for national digital identification. Passwordless solutions, such as the SK Telecom Co. passkey system introduced in August 2024, eliminate the need for traditional passwords, leading to enhanced security and user experience. The U.S. Government Accountability Office showed that data breaches for federal institutions annually increased by 15% hence increasing the ability to support the organizations of more advanced solutions like passwordless solutions. These initiatives by the governments are likely to increase the market through the forecast period. The passwordless technology trend is anticipated to surge post-Covid as there is an increased adoption of remote work environments in various organizations and enterprises that will aim at ensuring safe and scalable passwordless authentication solutions will be invested in. For example, Thales recently launched the Passwordless 360 in June 2024 which allows any company to increase security through biometrics and multi-factor authentication that support zero-trust security models and mitigate risks as a result of password breaches. VisionPoint also introduced a binding of access to authentication that provides managed federated authentication with the integration of a unified security guarantee. The leverage of the passwordless authentication market is likely to increase as more governments and governments receive funding.
| Category | Details |
|
Government Support |
- Governments worldwide are promoting the adoption of passwordless systems through policies that mandate multi-factor authentication (MFA) and biometric standards. |
|
Global Digital Transformation |
- As part of digital transformation efforts, 45% of governments are implementing passwordless solutions in public services and cybersecurity protocols. |
|
Biometric Authentication Demand |
- Biometric authentication, including facial recognition and fingerprint scanning, is seeing rapid uptake, replacing traditional passwords in 65% of new security systems. |
|
Security and Compliance |
- Government regulations such as PSD2 (EU) and CISA (U.S.) are driving demand for passwordless and MFA solutions to enhance security and comply with digital identity laws. |
|
Key Adoption Sectors |
- Sectors such as banking, healthcare, and government services are leading in adopting passwordless authentication, improving both user experience and data security. |
Passwordless Authentication Market Dynamics
Drivers
-
With around 81% of breaches attributed to weak passwords, organizations are shifting towards passwordless authentication to enhance security and reduce risks associated with credential theft.
-
The proliferation of smartphones and other connected devices is driving the adoption of passwordless solutions, as users seek more convenient and secure access methods.
-
Regulatory frameworks requiring stronger authentication measures are pushing businesses to implement passwordless technologies to comply with data protection regulations.
A major factor contributing to the growth of the passwordless authentication market is the increasing demand for enhanced security. Passwords have always been linked to security concerns, with 81% of hacking-related data breaches resulting from passwords that are weak or stolen. This statistic underscores the urgency for organizations to adopt more secure authentication methods. For example, in industries like banking, where financial security is paramount, companies are transitioning to passwordless solutions. A survey showed that over 90% of consumers reuse passwords across personal and professional accounts, making them vulnerable to credential-stuffing attacks. In response, many banks are implementing biometric solutions, such as fingerprint or facial recognition, to provide an extra layer of security. For example, Wells Fargo has adopted voice recognition technology, allowing customers to access their accounts securely without passwords.
Another significant factor contributing to the growth of passwordless authentication is the increasing work-from-home trend combined with the increasing use of different digital devices. This form of employment increases one’s dependence on digital devices and the number of different security measures required because of that. Password-led systems have become insufficient for this and are being outperformed by more secure passwordless solutions. This shift is beneficial to customers because it decreases the tension between the vast number of applications and their respective passwords. Additionally, the shift toward remote work has further amplified the need for secure access solutions. As employees increasingly rely on various devices, passwordless authentication reduces the friction of managing multiple passwords while enhancing overall security. This trend is not only beneficial for user experience but also aligns with regulatory pressures that mandate stronger authentication measures to protect sensitive data.
Restraints
-
Many organizations face difficulties integrating passwordless systems with their existing infrastructure, which can hinder adoption
-
Some users may be resistant to adopting new authentication methods due to familiarity with traditional password systems, impacting the transition to passwordless solutions
-
The initial investment required for deploying passwordless authentication solutions can be significant, especially for smaller businesses, limiting widespread adoption
The significant restraint for the adoption of passwordless authentication lies in the integration challenges for organizations. While the modern alternatives to password systems serve to enhance the security measures in place in an organization, and the benefits of using passwordless systems are evident, companies still face significant obstacles to incorporating those tools into the current organizational environment. Passwordless systems such as key fobs or biometric fingerprint readers, require substantial changes in the existing infrastructure, which often implies extra cost and resources. Because many organizations use legacy systems that do not work well with the newer technologies, integration becomes a challenging task that takes time, as well as disrupts the operations of the company. Besides, existing conditions should be compatible with the new systems, which involve a lot of testing and validation. The above challenges indicate that the integration obstacles comprise a significant barrier to the broader implementation of passwordless systems, despite the increasing demand for security measures and the emergence of more user-friendly technologies.
Passwordless Authentication Market Segment analysis
By Component
In 2023, the hardware segment led the market in passwordless authentication, accounted 60% of global revenue share. This huge share is contributed to by the rapid increase in the adoption of biometric devices like fingerprint scanners, iris scanners, and facial recognition systems. These devices boast some of the strongest security attributes and are therefore very heavily favoured in both enterprise and government application spheres. For example, in 2023, the U.S. Department of Defense (DoD) deployed fingerprint authentication hardware across agencies to enhance the security of its protocols, which further fueled demand in the segment. Hardware has been very important for providing secure, tamper-resistant access, particularly in critical infrastructure sectors where data security is paramount.
The services segment is likely to witness robust growth during the forecast period in response to the rising demand for integrating software with maintenance and support services. According to ENISA of the European Union Agency for Cybersecurity, a 20% increase in the deployment of passwordless authentication across the EU in 2023 indicated the emergence of an increased demand for professional services, including installation, configuration, and real-time support. Total comprehensive services are widely recognized by governments and organizations for the efficient implementation and operation of passwordless authentication systems. As the solution is becoming increasingly complex and widespread, growth in the services segment is expected to be vast, providing continuous support and specific solutions according to the changing security needs of various industries.
By Product Type
The fingerprint authentication sector led in the passwordless authentication market in 2023, with the highest revenue share. The popularity of fingerprint authentication systems is attributed to their ease of use, low cost, and flexible use across various common consumer gadgets. The U.S. Federal Trade Commission’s 2023 Consumer Authentication Survey stated that over 80% of smartphone users employed fingerprint recognition as the most common method for securing their data. The rapid adoption of mobile devices has also increased the demand for fingerprint authentication technologies, as laptops and access control systems also integrate the technology.
Furthermore, the adoption of biometrics has reached the government level. The United Kingdom Home Office released its cybersecurity report in 2023, which declared that over 60% of public service sectors employed fingerprint biometrics to accomplish identity proofing for any public tasks or services. The increasing functionality of fingerprint technology across the finance, healthcare, law enforcement, and other sectors is driving the expansion of the fingerprint authentication segment. As biometric systems become more reliable and secure, their adoption is expected to continue rising, particularly in sectors requiring stringent identity verification processes.
By Authentication Type
In 2023, the single-factor authentication segment dominated the passwordless authentication market in 2023. Single-factor authentication (SFA) remains highly in demand as it is easy to implement and cost-effectiveness. Many organizations, especially in developing markets, still widely use this method for daily activities that do not need high-end security measures. According to Government statistics indicate that SFA was used in over 55% of passwordless authentication systems implemented across small and medium-sized enterprises (SMEs) in 2023, SFA is primarily used in areas where multi-factor authentication (MFA) adoption is slow due to budgeting constraints.
However, cybersecurity professionals and regulators have been gaining ground against SFA by looking to transition to MFA for security reasons. It is urged that there be enhanced MFA adoption within the U.S. marketplace with the expectation that NIST has indicated MFA-based systems will take away the majority market share currently dominated by SFA. Although SFA leads the market currently, MFA's role in improving security through layered defences is expected to gain significant traction in the forecast period.
Regional Analysis
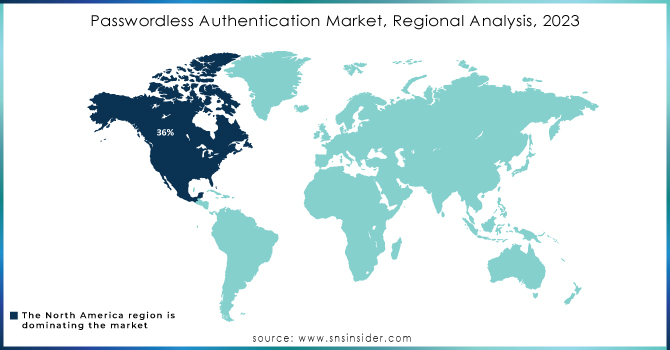
In 2023, North America led in the passwordless authentication market, having the highest market share 36%. Their dominance over the market was attributed to the strong regulatory environment and technological infrastructure established in the region. The performance is attributed to the U.S. cybersecurity improvements in the public and private sectors. In 2023, the U.S. held 45% of the global market share. Passwordless authentication has been widely adopted in financial institutions, healthcare facilities, and government offices. The shift to innovative technology was further catalyzed by the introduction of the Zero Trust Strategy by the U.S. government, which requires all federal departments and sub-agencies to implement passwordless authentication.
During the forecast period, the Asia-Pacific region is anticipated to experience the highest CAGR. The expected performance is due to the ongoing massive digital adoption in China, India, and Japan, which are experiencing fast-growing economies. In India, the government introduced the biometric Aadhaar identification system, whereby the program comes with a fingerprint and iris recognition application. The technology has enabled the citizens to widely use passwordless authentication systems, which held 15% of the regional share by 2023. The Ministry of Electronics and Information Technology noted that the deployment of the technology is expected to grow by 25% per annum in the coming years. The modernization of the infrastructure is supported by the various government organizations that are working towards improvements in the personal data protection standard as recommended globally.
Need any customization research on Passwordless Authentication Market - Enquiry Now
Key Players
Key Service Providers/Manufacturers:
-
Microsoft (Windows Hello, Azure AD Passwordless)
-
Google (Google Authenticator, FIDO2-based Login)
-
Okta (Okta Identity Engine, Okta Verify)
-
IBM (IBM Security Verify, IBM Cloud Identity)
-
Yubico (YubiKey 5 Series, YubiHSM)
-
HID Global (ActivID, HID DigitalPersona)
-
Ping Identity (PingOne, PingID)
-
Auth0 (Auth0 Identity Platform, Auth0 Passwordless)
-
Thales Group (SafeNet Trusted Access, Thales Luna HSM)
-
OneSpan (Cronto, Digipass)
Key Users:
-
Bank of America
-
JP Morgan Chase
-
Amazon
-
Facebook
-
Walmart
-
Airbnb
-
CitiGroup
-
Salesforce
-
PayPal
-
American Express
Recent News and Developments
- Hawcx Inc. launched its advanced passwordless authentication platform in April of 2024, balancing security and convenience for enterprises and customers end-users, heralding a new era in digital authentication.
- The U.S. Department of Homeland Security announced a Passwordless biometric authentication system rolled out across the U.S. in June of 2023, with the U.S. Department of Homeland Security initiating the nationwide implementation across all of its border agencies.
| Report Attributes | Details |
| Market Size in 2023 | USD 17.1 billion |
| Market Size by 2031 | USD 71.2 billion |
| CAGR | CAGR of 17.2% From 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Component (Hardware, Software, Services) • By Portability (Fixed, Mobile) • By Product Type (Fingerprint Authentication, Palm Recognition, Iris Recognition, Face Recognition, Voice Recognition, Smart Card, Others) • By Authentication Type (Single-factor Authentication, Multi-factor Authentication) • By End-user (IT & Telecom, Retail, Transportation & Logistics, Aerospace & Defence, BFSI, Healthcare, Government, Others) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]). Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia Rest of Latin America) |
| Company Profiles |
Microsoft, Google, Okta, IBM, Yubico, HID Global, Ping Identity, Auth0, Thales Group, OneSpan |
| Key Drivers | •With around 81% of breaches attributed to weak passwords, organizations are shifting towards passwordless authentication to enhance security and reduce risks associated with credential theft •The proliferation of smartphones and other connected devices is driving the adoption of passwordless solutions, as users seek more convenient and secure access methods. •Regulatory frameworks requiring stronger authentication measures are pushing businesses to implement passwordless technologies to comply with data protection regulations |
| Market Restraints | •Many organizations face difficulties integrating passwordless systems with their existing infrastructure, which can hinder adoption •Some users may be resistant to adopting new authentication methods due to familiarity with traditional password systems, impacting the transition to passwordless solutions •The initial investment required for deploying passwordless authentication solutions can be significant, especially for smaller businesses, limiting widespread adoption |

