Artificial Intelligence In Cybersecurity Market Report Scope & Overview:
The Artificial Intelligence In Cybersecurity Market Size was valued at USD 24.44 Billion in 2025E and is expected to reach USD 111.56 Billion by 2033 and grow at a CAGR of 20.93% over the forecast period 2026-2033.
The growth of the Artificial Intelligence in Cybersecurity market is primarily driven by the increasing sophistication and frequency of cyberattacks across industries. With organizations facing complex threats such as ransomware, phishing, and zero-day attacks, traditional security solutions often fall short in real-time threat detection and mitigation. AI-powered cybersecurity solutions leverage machine learning, natural language processing, and behavioral analytics to identify anomalies, predict attacks, and automate responses, enabling faster and more accurate threat detection. According to study, AI-powered systems can reduce threat detection time by up to 70–80% compared to traditional systems.
Market Size and Forecast:
-
Market Size in 2025: USD 27.44 Billion
-
Market Size by 2033: USD 111.56 Billion
-
CAGR: 20.93% from 2026 to 2033
-
Base Year: 2025
-
Forecast Period: 2026–2033
-
Historical Data: 2022–2024

Get more information on Artificial Intelligence (AI) in Cybersecurity Market - Request Sample Report
Key Artificial Intelligence In Cybersecurity Market Trends
-
Rising cyberattack sophistication drives global adoption of AI cybersecurity solutions.
-
Cloud, IoT, and remote work expand AI security requirements.
-
AI-powered anomaly detection and behavioral analytics enhance threat prediction accuracy.
-
Automated responses reduce attack impact, downtime, and manual security interventions.
-
Scalable AI solutions ensure compliance, fraud prevention, and proactive threat intelligence.
-
AI adoption improves detection rates while lowering false-positive security alerts.
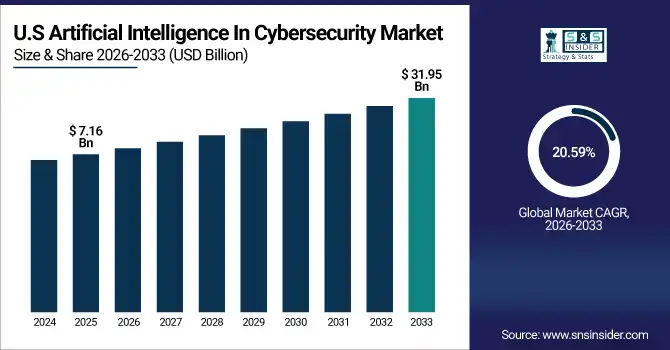
The U.S. Artificial Intelligence In Cybersecurity Market size was USD 7.16 Billion in 2025E and is expected to reach USD 31.95 Billion by 2033, growing at a CAGR of 20.59% over the forecast period of 2026-2033, driven by widespread smartphone and console adoption, advanced broadband and 5G networks, and strong engagement in esports and multiplayer games.
Artificial Intelligence In Cybersecurity Market Growth Drivers:
-
AI Shields Enterprises Against Increasingly Sophisticated and Evolving Cyberattacks Worldwide
The growing complexity and frequency of cyberattacks is a major driver for the AI in cybersecurity market. Traditional security systems often rely on signature-based detection methods, which can fail to identify zero-day threats, ransomware, and advanced persistent threats (APTs). AI-powered cybersecurity solutions, leveraging machine learning, behavioral analytics, and natural language processing, can analyze massive volumes of data in real-time to detect anomalies, predict potential attacks, and respond automatically. Organizations adopting cloud computing, IoT devices, and remote work models face larger attack surfaces, making AI-driven, adaptive security solutions essential. According to industry reports.
AI can reduce threat detection time by up to 70–80%, improve detection accuracy to 85–95%.
Artificial Intelligence In Cybersecurity Market Restraints:
-
High Costs And Complexity Limit Widespread Adoption Of AI Security
Despite its benefits, the high cost and technical complexity of deploying AI-driven cybersecurity solutions can restrain market growth. Implementing AI systems requires significant investment in infrastructure, high-performance computing, data storage, and skilled personnel capable of managing, training, and fine-tuning AI models. Many small and medium-sized enterprises (SMEs) find the upfront cost prohibitive, which can delay adoption. Additionally, integrating AI with legacy security tools and existing IT infrastructure can be challenging, requiring customized solutions and ongoing maintenance. These factors can slow market penetration, especially in developing regions where cybersecurity budgets are limited.
Artificial Intelligence In Cybersecurity Market Opportunities:
-
Automated Threat Intelligence Offers Scalable, Efficient, And Proactive Security Solutions
The rising demand for automated threat intelligence and security operations presents a major opportunity for market growth. AI systems can continuously collect, analyze, and correlate threat data from multiple sources, providing actionable insights for organizations to proactively prevent attacks. Automation reduces manual workload, accelerates incident response, and minimizes human error. Industries such as BFSI, healthcare, and retail, which face high regulatory and compliance requirements, are increasingly adopting AI for automated monitoring, identity verification, and fraud prevention. The market opportunity also extends to cloud-native AI security platforms, where AI can manage distributed endpoints in real-time, offering scalable and cost-efficient solutions to growing cyber threats.
Percentage of enterprises using AI to collect and correlate threat data: ~40–50% globally..
Artificial Intelligence In Cybersecurity Market Segmentation Analysis:
-
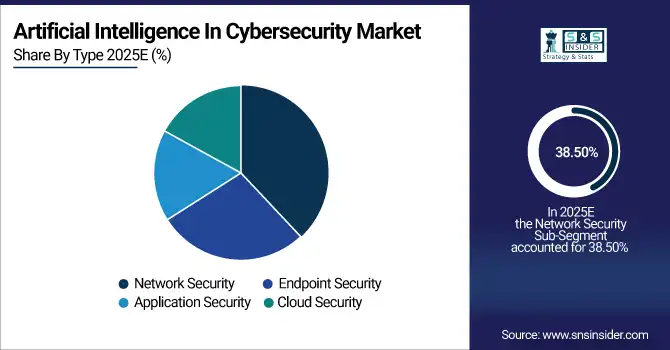
By Type: In 2025, Network Security led the market with share 38.50%, while Cloud Security are the fastest-growing segment with a CAGR 36.40%.
-
By Offering: In 2025, Software the market 58.06%, while Services fastest-growing segment with a CAGR 26.04%.
-
By Technology: In 2025, Machine Learning led the market with share 65.20%, while Natural Language Processing (NLP) the fastest-growing segment with a CAGR 31.30%.
-
By Vertical: In 2025, Enterprise led the market with share 24.30%, while Healthcare is the fastest-growing segment with a CAGR 35.02%.
-
By Application: In 2025, Fraud Detection/Anti-Fraud led the market with share 35.02%, while Unified Threat Management is the fastest-growing segment with a CAGR 16.80%.
By Type, Network Security Leads Market While Cloud Security Fastest Growth
In the Artificial Intelligence in Cybersecurity market, Network Security continues to dominate, accounting for the largest market share due to its critical role in protecting enterprise networks from sophisticated threats such as malware, ransomware, and phishing attacks. Enterprises prioritize securing network infrastructure to prevent data breaches and ensure regulatory compliance, making network-focused AI solutions highly sought after. Meanwhile, Cloud Security is the fastest-growing segment, driven by the rapid adoption of cloud computing, hybrid IT environments, and remote work. AI-powered cloud security solutions offer real-time threat detection, automated response, and scalable protection for distributed applications and endpoints, fuelling robust market growth.
By Offering, Software Leads Market While Services Fastest Growth
In the Artificial Intelligence in Cybersecurity market, Software leads the offering segment, holding the largest share due to its widespread adoption across enterprises for threat detection, monitoring, and security management. Software solutions provide flexibility, rapid deployment, and continuous updates, enabling organizations to proactively manage evolving cyber threats. On the other hand, Services represent the fastest-growing segment, fueled by increasing demand for managed security services, consulting, integration, and AI-driven support. Organizations, particularly SMEs and enterprises with limited in-house cybersecurity expertise, are leveraging AI-based services to enhance operational efficiency, reduce response times, and strengthen overall security posture, driving significant market growth.
By Technology, Machine Learning Leads Market While Natural Language Processing (NLP) Fastest Growth
In the Artificial Intelligence in Cybersecurity market, Machine Learning dominates the technology segment, capturing the largest share due to its ability to analyze vast volumes of data, detect anomalies, and predict potential cyber threats with high accuracy. Machine learning algorithms empower enterprises to implement real-time threat detection and automated responses, significantly reducing risks and operational overhead. Meanwhile, Natural Language Processing (NLP) is the fastest-growing technology segment, driven by the rising need to analyze unstructured data from emails, logs, and social engineering attacks. NLP enables advanced threat intelligence, contextual analysis, and proactive risk mitigation, fueling rapid adoption across industries.
By Vertical, Enterprise Leads Market While Healthcare Fastest Growth
In the Artificial Intelligence in Cybersecurity market, the Enterprise vertical holds the largest market share, driven by the need to protect extensive IT infrastructure, sensitive corporate data, and intellectual property across multiple locations. Large enterprises prioritize AI-powered security solutions for real-time threat detection, automated response, and compliance with regulatory requirements. Meanwhile, the Healthcare segment is the fastest-growing vertical due to increasing cyber threats targeting patient data, electronic health records, and medical devices. AI solutions in healthcare help monitor network activity, detect anomalies, and prevent data breaches, enabling organizations to enhance patient data security while ensuring operational continuity.
By Application, Fraud Detection/Anti-Fraud Leads Market While Unified Threat Management Fastest Growth
In the Artificial Intelligence in Cybersecurity market, Fraud Detection/Anti-Fraud leads the application segment, driven by the increasing need to identify and prevent financial fraud, identity theft, and unauthorized transactions across industries such as BFSI, retail, and e-commerce. AI-powered fraud detection solutions leverage machine learning and behavioral analytics to detect anomalies, reduce false positives, and enable real-time intervention, securing critical assets. Meanwhile, Unified Threat Management (UTM) is the fastest-growing application, fueled by the demand for integrated, multi-layered security solutions that combine firewall, intrusion detection, antivirus, and threat intelligence in a single platform, providing comprehensive protection for distributed networks and endpoints efficiently.
Artificial Intelligence In Cybersecurity Market Regional Analysis:
North America Artificial Intelligence In Cybersecurity Market Insights:
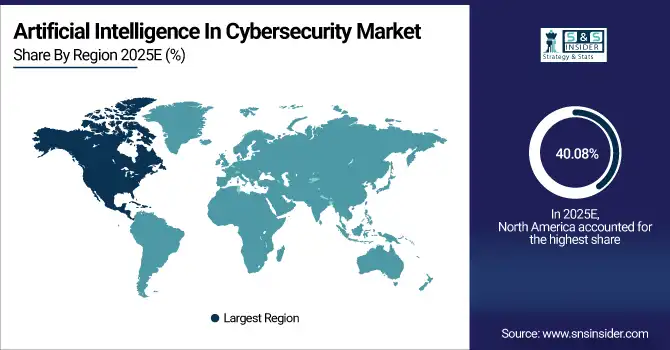
North America accounted for the largest share 40.08%of the Artificial Intelligence In Cybersecurity Market in 2025, driven by the presence of major cybersecurity vendors, high digital adoption, and stringent data protection regulations like CCPA and HIPAA. Enterprises across BFSI, healthcare, IT, and government sectors are increasingly deploying AI-powered security solutions to detect sophisticated threats, including ransomware, phishing, and insider attacks. The region benefits from advanced infrastructure, significant cybersecurity investments, and early adoption of cloud, IoT, and remote work technologies, which expand attack surfaces. AI solutions offering real-time threat intelligence, automated incident response, and behavioral analytics are rapidly adopted, fueling robust market growth in North America.
Get Customized Report as per Your Business Requirement - Enquiry Now
U.S. Dominates Artificial Intelligence In Cybersecurity Market with Advanced Technological Adoption
The U.S. leads the AI in Cybersecurity market due to early adoption of AI-driven threat detection, cloud security, and machine learning solutions, supported by strong cybersecurity infrastructure, regulatory compliance, and significant investments across industries.
Asia-Pacific Artificial Intelligence In Cybersecurity Market Insights
In 2025, Asia-Pacific is the fastest-growing Artificial Intelligence In Cybersecurity Market with a CAGR 22.31%, driven by rapid digital transformation, increasing internet penetration, and the growing adoption of cloud computing, IoT, and mobile technologies. Countries such as China, Japan, India, and Australia are investing heavily in AI-powered cybersecurity solutions to address rising cyber threats, including ransomware, phishing, and advanced persistent attacks. The expansion of BFSI, healthcare, and e-commerce sectors further fuels demand for real-time threat detection, automated responses, and AI-driven threat intelligence. Government initiatives promoting cybersecurity and digital safety also accelerate market growth across the region.
China and India Propel Rapid Growth in Artificial Intelligence In Cybersecurity Market
China and India drive AI cybersecurity market growth through rapid digital adoption, increasing cloud and IoT deployment, rising cyber threats, and government initiatives, leading to higher investments in AI-powered threat detection and automated security solutions.
Europe Artificial Intelligence In Cybersecurity Market Insights
Europe holds a significant share in the Artificial Intelligence in Cybersecurity market, driven by stringent data protection regulations and high awareness of cybersecurity risks across enterprises. Organizations are increasingly investing in AI-based solutions for threat detection, incident response, and fraud prevention across BFSI, healthcare, and government sectors. The growing adoption of cloud computing, IoT, and digital transformation initiatives further boosts demand for AI-driven security platforms. Advanced AI technologies, including machine learning and behavioral analytics, are being integrated into existing security infrastructure, enabling real-time monitoring, predictive threat intelligence, and automated response, strengthening cybersecurity across the region.
Germany and U.K. Lead Artificial Intelligence In Cybersecurity Market Expansion Across Europe
Germany and the U.K. drive AI cybersecurity growth in Europe through advanced technological adoption, regulatory compliance, and enterprise investments, accelerating deployment of AI-powered threat detection, automated responses, and predictive security solutions across multiple industry sectors.
Latin America (LATAM) and Middle East & Africa (MEA) Artificial Intelligence In Cybersecurity Market Insights
The Artificial Intelligence in Cybersecurity market in Latin America (LATAM) and Middle East & Africa (MEA) is witnessing steady growth, driven by increasing digitalization, rising cyber threats, and growing adoption of cloud computing, IoT, and mobile technologies across enterprises. Organizations across BFSI, healthcare, and government sectors are investing in AI-powered cybersecurity solutions for real-time threat detection, automated response, and fraud prevention. Rising awareness about data privacy, coupled with government initiatives promoting cybersecurity infrastructure, fuels market adoption. AI technologies such as machine learning, behavioral analytics, and threat intelligence are being leveraged to enhance security, reduce manual intervention, and strengthen overall network protection.
Artificial Intelligence In Cybersecurity Market Competitive Landscape
IBM Security leverages AI and machine learning to enhance threat detection, data protection, and incident response across industries. Solutions like QRadar and Guardium use predictive analytics and automated workflows, helping enterprises identify vulnerabilities, reduce breaches, and strengthen compliance, positioning IBM as a trusted leader in AI-powered cybersecurity solutions worldwide.
- In August 2025, IBM's 2025 Data Breach Report revealed vulnerabilities in AI systems, emphasizing the need for improved access controls and governance to protect sensitive data.
Microsoft integrates AI into its cybersecurity offerings, including Microsoft 365 Copilot and Azure Sentinel, providing intelligent threat detection, risk management, and automated security operations. Its cloud-based AI solutions empower organizations to protect sensitive data, secure endpoints, and manage hybrid environments efficiently, driving adoption across enterprise and government sectors.
- In February 2025, Microsoft partnered with the U.S. General Services Administration to provide AI and cloud tools, including Microsoft 365 Copilot and Azure, to federal agencies, aiming to accelerate AI adoption and enhance cybersecurity.
Palo Alto Networks is a market leader in AI-driven cybersecurity, offering solutions like Cortex and Prisma that integrate machine learning for real-time threat detection, automated response, and cloud security. Its platforms help enterprises safeguard networks, endpoints, and cloud environments, enabling scalable, proactive protection against evolving cyber threats globally.
- In February 2025, Palo Alto Networks introduced Cortex Cloud, a unified AI-driven platform designed to automate workflows, reduce risks, and prevent threats in real time
Artificial Intelligence In Cybersecurity Market Key Players:
Some of the Artificial Intelligence In Cybersecurity Market Companies
- Palo Alto Networks
- CrowdStrike
- Microsoft
- IBM Security
- Cisco Systems
- Fortinet
- Check Point Software
- Trend Micro
- Splunk
- SentinelOne
- Darktrace
- Vectra AI
- Cybereason
- Rapid7
- Trellix (FireEye/McAfee Enterprise)
- Sophos
- Elastic
- LogRhythm
- Deep Instinct
- Exabeam
| Report Attributes | Details |
| Market Size in 2025 | USD 24.44 Billion |
| Market Size by 2033 | USD 111.56 Billion |
| CAGR | CAGR of 20.93% From 2026 to 2033 |
| Base Year | 2025 |
| Forecast Period | 2026-2033 |
| Historical Data | 2022-2024 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Type (Network Security, Endpoint Security, Application Security, Cloud Security) • By Offering (Hardware, Software, Services) • By Technology (Machine Learning, Natural Language Processing (NLP), Context-aware Computing) • By Vertical (BFSI, Retail, Government & Defense, Manufacturing, Enterprise, Healthcare, Automotive & Transportation, Others) • By Application (Identity and Access Management, Risk and Compliance Management, Data Loss Prevention, Unified Threat Management, Fraud Detection/Anti-Fraud, Threat Intelligence, Others) |
| Regional Analysis/Coverage | North America (US, Canada), Europe (Germany, UK, France, Italy, Spain, Russia, Poland, Rest of Europe), Asia Pacific (China, India, Japan, South Korea, Australia, ASEAN Countries, Rest of Asia Pacific), Middle East & Africa (UAE, Saudi Arabia, Qatar, South Africa, Rest of Middle East & Africa), Latin America (Brazil, Argentina, Mexico, Colombia, Rest of Latin America). |
| Company Profiles | Palo Alto Networks, CrowdStrike, Microsoft, IBM Security, Cisco Systems, Fortinet, Check Point Software, Trend Micro, Splunk, SentinelOne, Darktrace, Vectra AI, Cybereason, Rapid7, Trellix (FireEye/McAfee Enterprise), Sophos, Elastic, LogRhythm, Deep Instinct, Exabeam., and Others. |

