Deception Technology Market Report Scope & Overview:
The Deception Technology Market was valued at USD 2.0 Billion in 2023 and is expected to reach USD 6.6 Billion by 2032, growing at a CAGR of 13.72% from 2024-2032.
Get more information on Deception Technology Market - Request Sample Report
Deception technology has become a cornerstone of modern cybersecurity, providing proactive defense mechanisms to counter increasingly sophisticated cyber threats. This innovative approach uses decoys and traps that mimic legitimate network assets, enabling organizations to detect, analyze, and neutralize unauthorized intrusions in real time. By diverting attackers from critical systems and exposing their tactics, deception technology fortifies an organization’s security framework. The escalating complexity and frequency of cyberattacks have outpaced traditional security measures, driving the widespread adoption of deception solutions to enhance protection. Furthermore, stringent global data protection regulations have amplified demand, as deception technology supports compliance efforts through comprehensive monitoring and rapid breach detection.
A major growth factor in this market is the seamless integration of deception solutions into existing security infrastructures, allowing organizations to enhance their defenses without disrupting operations. These solutions are also cost-efficient, minimizing the resources needed for threat detection and response while optimizing overall security investments. Additionally, deception technology delivers advanced threat intelligence by analyzing interactions with decoys, enabling organizations to anticipate and counter future threats with greater accuracy. The rising adoption of these technologies underscores their critical role in addressing the challenges posed by increasingly sophisticated cyberattacks.
growth reflects the growing reliance on deception technology as a proactive tool to identify and neutralize cyber threats, solidifying its position as an indispensable element of modern cybersecurity strategies.
Market Dynamics
Drivers
-
Growing adoption of cloud services and IoT devices has created new vulnerabilities, driving the implementation of deception technology to protect digital assets.
As more people and organizations utilize cloud services and IoT devices in their personal lives and homes, the digital landscape has grown larger, along with the potential attack vectors for cybercriminals. While cloud environments bring in scalability & efficiency, the intricate infrastructure is highly vulnerable & tougher to secure as organizations move towards multi-cloud & hybrid nature cloud strategies. Likewise, the explosion of IoT devices has added even more endpoints to networks, with many not being particularly secure at all. This has expanded the attack surface and left significant gaps in the threat surface that legacy security solutions simply cannot fill.
To address this, deception technology has proven to be one of the most effective ways to mitigate risks, offering proactive defense mechanisms designed to suit modern infrastructures. Deception solutions can aid in the real-time detection of unauthorized access and malicious activities through decoys and traps within cloud environments and IoT networks. Such decoys simulate real assets, confusing attackers away from real ones while providing the organization the means to observe them without the danger of exposing the most critical systems. This method improves threat detection and also provides insights into how attackers operate, to help an organization improve its overall defense. Additionally, deception technology scales seamlessly to the ever-changing nature of cloud and IoT environments. This method combines the new layer with the other security frameworks existing in the organization for the required step, thus ensuring no disruption in any business activity when it protects the digital items. With the continuous increase of cloud services and IoT devices, deception technology will be more crucial than ever to protecting sensitive data and maintaining the reliability of modern digital infrastructures.
-
Integration of artificial intelligence and machine learning enhances the efficiency and accuracy of deception solutions.
-
Increased remote work environments have expanded attack surfaces, boosting the need for deception technology to secure distributed networks.
Restraints
-
A lack of cybersecurity professionals proficient in deploying and managing deception solutions restricts market growth.
The shortage of skilled cybersecurity professionals with expertise in deploying and managing deception technology presents a significant barrier to the growth of this market. Implementing effective deception solutions requires specialized knowledge to design, deploy, and maintain decoys that closely resemble legitimate network assets. Additionally, professionals must have advanced analytical skills to interpret data from decoy interactions, differentiate genuine threats from false positives, and derive actionable insights to strengthen security measures. However, the global demand for such expertise far outpaces the available supply, creating a critical talent gap that hinders the adoption of advanced security technologies like deception solutions.
Many organizations, particularly small and medium-sized enterprises, face challenges in finding qualified personnel capable of seamlessly integrating deception tools into existing security frameworks while maintaining optimal performance. SMEs often lack the resources to recruit or train staff with the necessary skill set, making them hesitant to adopt deception technology due to concerns about improper implementation or underutilization. Furthermore, the effectiveness of deception systems relies on continuous monitoring, updates, and adaptation to evolving cyber threats. Without adequately trained professionals, organizations may struggle to fully leverage the benefits of deception technology, diminishing its potential impact. Bridging this skills gap will require significant investment in cybersecurity education and training initiatives to build a workforce capable of meeting the growing demand for deception solutions. Addressing this challenge is crucial for unlocking the full potential of the deception technology market and strengthening global cybersecurity defenses against sophisticated threats.
-
The initial investment and maintenance expenses for deception technology solutions can be a barrier for small and medium-sized enterprises
-
Limited awareness and understanding of deception technology among businesses hinder its widespread adoption.
Segment Analysis
By Component
The solution segment dominated the market and represented a significant revenue share of 65% in 2023. This growing need for advanced cybersecurity solutions is a direct result of the rising incidences and complexity of cyber-attacks. With Advanced Persistent Threats and zero-day attacks on the rise, traditional security solutions are becoming less effective. That means defense should become more proactive and evasive. Such advanced threats can be detected and mitigated using deception technology where attackers are lured into decoys. This allows organizations to detect and respond to attacks early in their lifecycle before they can do much damage.
Organizations need a boost when it comes to deployment, customization, or optimization of deception technologies, and, as such, demand for professional services is on the rise. To maximize the effectiveness of deception solutions, these services include consulting, implementation, and training. Professional services make the deception technology fit for purpose and essential for the organization. It improves the overall security profile and protects an organization from highly sophisticated threats.
By Deployment
In 2023, Cloud Segment dominated the market and held the largest revenue share. As enterprises adopt deception technology to protect these complex environments, the increased use of multi-cloud strategies is acting as the catalyst for its adoption. The idea is to use deception tools deployed across integration layers across all the involved cloud platforms to enable an integrated security framework that provides real-time threat detection and response capabilities. This trend tackles the new security challenges that come with managing and protecting all those resources across varied cloud providers. Deception technology provides the organization with the assurance that security policies and threat detection mechanisms are uniform across all cloud environments. This rising trend minimizes consumption and mitigates risks with multi-cloud deployments to improve overall cloud security.
The integration of deception technology with legacy IT systems is gaining traction in the on-premises segment. Older infrastructure that some organizations may still use can lack cutting-edge security. The addition of deception tools also allows these organizations to develop added layers of protection without a complete overhaul of their systems. Helps identify and respond to threats specifically in legacy environments. As a result, one of the major trends is about integrating deception technology with legacy systems so that the older IT infrastructures are also shielded from the advances of cyber threats.
By Deception
In 2023, the data security segment dominated the market and accounted for the largest share of 42%. Deception technology is emerging as the next step in the detection and response of advanced threats in the data security segment. Using decoy data and fake environments, organizations can detect and redirect attempts to malicious activities on their sensitive information. This enables the detection of potential threats at an early stage and reduces the possibility of a data breach as well. Deception technology can be integrated into your threat detection framework to provide a more targeted response to sophisticated cyber-attacks. This means that organizations are more prepared to defend their data against developing and sophisticated threats.
One emerging trend in application security is the combination of deception technology and DevSecOps. Organizations are integrating deception tools in their development, security, and operations workflows to fortify application security from the ground up. Combining, ensuring everyone from development to deployment and maintenance considers security in every step of the application lifecycle. Deception technology helps organizations detect and mitigate threats early in the lifecycle and reduce supercilious vulnerabilities in the PROD Environment. By taking preventive measures to maintain security, these assurances allow applications to be more secure and minimize the risk of cyber-attacks.
Regional Analysis
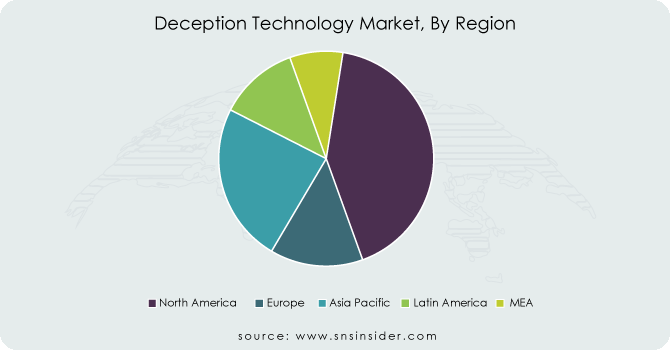
In 2023, North America led the market, contributing to 37%, revenue share. bolstering incident response abilities. Deception tools are hidden in the organization's environment having the power to enhance real-time detection analysis and response to security incidents. It is achieved by deploying decoy assets and tracking the interaction which helps them to recognize malicious activities and eliminate threats before they lead to something worse. By taking proactive measures, the impact of security breaches can be minimized and operations can be continued without disruption. Deception technology will play a key role in efficiently managing incidents during and after outbreaks or attacks, fueling the adaption of this trend in incident response capabilities across North America.
Asia Pacific is expected to register the fastest CAGR during the forecast period. Rapid digital advancements and increasing connectivity in the Asia-Pacific have led to rising cyber threats and security issues. Since advanced cyber-attacks, which include ransomware, phishing, and even nation-states have become a constant threat, deception technology is being embraced to bolster protection. Organizations can lure and distract attackers by deploying decoy assets and decoy ecosystems and can also gain valuable insights into attacker behavior. This disciplined approach helps to fortify the cybersecurity posture in APAC while ensuring that businesses are equipped at all times to safeguard critical data, intellectual property, and infrastructure from forever-evolving threats.
Need any customization research on Deception Technology Market - Enquiry Now
Key Players
The major key players are
-
Attivo Networks
-
TrapX Security
-
Smokescreen Technologies
-
Guardicore
-
ForeScout Technologies
-
Illusive Networks
-
Acalvio Technologies
-
Darktrace
-
LogRhythm
-
Cymmetria
-
Micro Focus
-
SonicWall
-
Proofpoint
Recent Developments
-
February 2024: Attivo Networks introduced a new version of its Deception Platform, featuring enhanced integration capabilities with existing security infrastructures.
-
March 2024: TrapX Security launched a cloud-based deception solution aimed at simplifying deployment and scalability for enterprises.
-
April 2024: Guardicore expanded its deception technology suite to include advanced threat intelligence features, providing deeper insights into attacker behaviors.
| Report Attributes | Details |
|---|---|
| Market Size in 2023 | USD 2.0 Billion |
| Market Size by 2032 | USD 6.6 Billion |
| CAGR | CAGR of 13.72% From 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Component (Solution, Service) • By Deception (Data Security, Application Security, Endpoint Security, Network Security) • By Deployment (On premise, Cloud) • By Organization Size (Small and Medium Enterprises, Large Enterprises) • By Vertical (BFSI, Energy and Utilities, Government, Healthcare, IT and Telecom, Manufacturing, Retail, Others) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles | Attivo Networks, TrapX Security, Smokescreen Technologies, Guardicore, ForeScout Technologies, Illusive Networks, Acalvio Technologies, Darktrace, LogRhythm, Cymmetria, Micro Focus, SonicWall,Proofpoint |
| Key Drivers | • Integration of artificial intelligence and machine learning enhances the efficiency and accuracy of deception solutions. • Increased remote work environments have expanded attack surfaces, boosting the need for deception technology to secure distributed networks. |
| RESTRAINTS | • The initial investment and maintenance expenses for deception technology solutions can be a barrier for small and medium-sized enterprises •Limited awareness and understanding of deception technology among businesses hinder its widespread adoption. |

