ENCRYPTION SOFTWARE MARKET KEY INSIGHTS:
The Encryption Software Market Size was valued at USD 15.86 Billion in 2023 and is expected to reach USD 62.69 Billion by 2032 and grow at a CAGR of 16.6% over the forecast period 2024-2032.
To Get More Information on Encryption Software Market - Request Sample Report
The Encryption Software Market has experienced a dramatic rise in the last couple of years, mainly on account of the increase in cybersecurity threats, regulatory compliance needs, digital transformation across industries, and the growing trend of cloud computing. With the growing demand for security in a data-driven world, wherein data breaches and cyberattacks are increasing in frequency and expense, encryption software has been one of the most imperative elements. It encodes data to protect sensitive information from unauthorized access. With increasing emphasis on the privacy of data and secure networks by companies and government agencies, demand for encryption solutions in industries is on the increase.
According to 2023 report, the average data breach cost organizations a staggering USD 4.45 million, which is a 15% increase over three years. Of course, about 50% of organizations that faced breaches were against increasing their cybersecurity spending and hence encryption becomes a viable, economical, and highly effective defense measure. With such high breach costs and financial risks of unprotected data, encryption solutions are now essential for organizations that have to find cost-effective means of preventive measures in cyber security. Around 83 percent of organizations express that data encryption is a first-line measure to ensure the safety of sensitive information, both due to regulation compliance requirements and data protection. Furthermore, 45% of breaches are small businesses, indicating the need for scalable and accessible encryption software cutting across sectors. Based on these trends, the market for encryption software is poised to grow as breaches become increasingly frequent, recovery costs are prohibitively high, and regulatory pressures mount, all in a bid to strengthen data protection in the context of cybersecurity frameworks.
MARKET DYNAMICS
KEY DRIVERS:
- Escalating Data Breach Costs Drive Demand for Encryption Software as Essential Defense Against Cyber Threats
The rising cost and continuous exploitation of sensitive data make it a business need to have encryption software. Encryption is a preventive mechanism that ensures that when the data is accessed with bad intentions, it remains secure. This financial factor propels organizations to invest in encryption to reduce the potential cost of a breach.
One of the main drivers of increased demand for encryption software has been rising costs in data breaches. In 2023, the average total cost incurred by a data breach rose to USD 4.45 million and the average cost per compromised record was USD 161. These costs indicate that organizations need to implement effective encryption solutions within their entities. With the dynamic nature of cyber threats, it takes about 287 days on average to detect and respond to breaches. This usually results in companies experiencing even more financial loss from breaches, hence encouraging them to adopt preventive measures such as encryption over sensitive data. Also, the rate of data breaches is alarming; this year it has risen by 7% compared to last year. Today, the need for effective cybersecurity has reached its peak with over 70% of organizations experiencing a data breach within the last year.
- Stringent Data Privacy Regulations Propel the Adoption of Encryption Software in a Data-Driven World
Europe's GDPR, California's CCPA, as well as others in Asia and Latin America, are compelling other global regulations to ensure data protection is the very best, such as encryption. Companies can suffer greatly through penalties and reputations can take a hit from not observing the regulation. This Drove companies to make use of encryption software for sensitive data protection and regulation. The demand for such encryption solutions is supported by this regulatory environment, and also mainly arises in sectors characterized by a huge volume of personal data such as financial, healthcare, and e-commerce.
As of 2024, the financial sanctions for noncompliance could reach 4% of the annual worldwide turnover or €20 million, whichever is more extreme. This drastic reality set organizations to focus on how to protect their data, and thus encryption is already an integral part of security strategy in any organization. The new legislation is to be enacted in 2024 across multiple jurisdictions, including states such as Texas and Florida. As companies navigate this complex compliance landscape, the need for encryption solutions is expected to increase.
RESTRAIN:
- Complexity of Implementation Hinders Widespread Adoption of Encryption Software
For a large number of organizations, it proves challenging to incorporate encryption solutions into the prevailing systems and workflows. Specialized skills and knowledge might not be readily available within the organization, thus leading to such complexity. For example, implementing encryption sometimes requires radical changes in the IT infrastructure, and managing encryption keys securely adds complexity. The 2024 ISC2 Cybersecurity Workforce Study estimated that there is a strong need for about 4.8 million cybersecurity professionals to keep organizations secure and that a gap in the skills landscape is increasing. A significant 90% of the respondents reported that they had experienced skills shortages within their teams, which complicates the deployment and management of encryption solutions. This shortage means that people can't find personnel with the specialized skills needed for the effective integration and maintenance of encryption systems.
Additional issues include cut in the budget for information security and hiring freeze. Such restrictive scenarios limit the organization's leverage to invest in the adequate tools and training needed to deploy encryption. As a result, most organizations are against the complete adoption of these encryption technologies due to such perceived risks of performance and operational complexity. Such factors reflect encryption software market is hindered due to the unavailability of skilled professionals and funding in this area despite the growing need for data protection in the regulatory landscape demanding robust security measures.
KEY SEGMENTATION ANALYSIS
BY DEPLOYMENT TYPE
The on-premise segment of the encryption software market held a dominant revenue share of 64% in 2023, The organizations seeking data control and security are the key drivers in this industry. Most large enterprises require on-premises solutions whereby they have complete control of their proprietary data, especially in regulatory sectors such as finance and healthcare. Some of these newly developed products include CipherTrust Data Security Platform which was recently developed by Thales among others to increase security for any data. Further, it is indicated that 82% of the entities feel on-premise solutions with encryption are necessary and a means to achieve proper compliance as well as protect consumers' data. As cyber threats are continually growing, their dependency on on-premises encryption solutions will augment and thereby emphasize the very role the segment has in the bigger picture of the encryption software marketplace.
The cloud-based segment of the encryption software market is projected to grow at the largest CAGR of 18.30% during the forecasted period, The rising adoption of cloud computing and the requirement for secure data management solutions drive it. Organizations are increasingly opting for cloud-based encryption solutions because they are scalable, cost-effective, and easy to deploy. For instance, Microsoft has enhanced its Azure platform with advanced encryption features that enable businesses to protect sensitive data stored in the cloud efficiently.
BY APPLICATION TYPE
The Disk Encryption segment held a substantial revenue share of 31% in 2023, due to the growing need to protect sensitive data stored in local drives and other portable devices. Disk encryption offers that robust security since data unless correct authentication credentials are provided, remains inaccessible and thus incapable of unauthorized access when devices are lost or stolen. Major players in the space, like Symantec and McAfee, released updated versions of their disk encryption solutions that boast advanced algorithms and more user-friendly interfaces, allowing for easier management across multiple devices by organizations.
The Cloud Encryption segment is poised for significant growth, with a projected CAGR of 19.42% during the forecasted period. Further, increased dependence on cloud services and the rapidly growing need for secure data management solutions continue to foster this growth. There is an increasing demand for cloud encryption technologies, with more and more growing businesses shifting operations to the cloud.
REGIONAL ANALYSIS
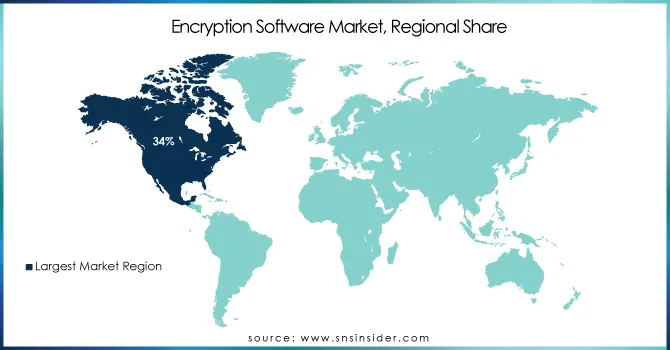
In 2023, North America dominated the encryption software market, accounting for over 34% of the total market share. This strong position can be attributed to several key factors. This region has very high advancement in IT infrastructure along with advanced digitalization within different sectors, which leads to the substantially increased focus on the matter of data security and privacy. For instance, within four years, by 2023, more than 80% of companies will deploy AI, so immediately an urgent need for sensitive data encryption within the AI system itself arises.
In 2023, the Asia Pacific region emerged as the fastest-growing segment of the encryption software market, boasting a robust CAGR of approximately 19.2% during the forecast period. The number of cyberattacks has increased and the various governments in the region are strict about data protection. For these reasons, the rapid growth is happening. As reported by IDC in November 2023, "Asia Pacific encryption software market has seen tremendous growth based on increasing emphasis on data privacy and security". Also, companies are likely to spend more on digital technology, which is expected to grow at four times the economic rate in 2024. This environment is encouraging a greater need for encryption solutions to protect sensitive data against rising cyber threats and stringent regulatory requirements.'
Do You Need any Customization Research on Encryption Software Market - Inquire Now
Key Players
Some of the major players in the Encryption Software Market are:
-
Bloombase (Bloombase Encryption, Bloombase Key Management)
-
Cisco Systems, Inc. (Cisco IronPort Email Security Appliance, Cisco Umbrella)
-
Check Point Software Technologies Ltd. (Check Point Endpoint Security, Check Point CloudGuard)
-
Dell Inc. (Dell Data Protection Encryption, Dell SecureWorks)
-
IBM Corporation (IBM Security Guardium, IBM Security Verify)
-
McAfee, LLC (McAfee Endpoint Security, McAfee Data Loss Prevention)
-
Microsoft (Microsoft BitLocker Drive Encryption, Microsoft Azure Information Protection)
-
Oracle (Oracle Database Vault, Oracle Data Security Pack)
-
Sophos Ltd. (Sophos SafeGuard Encryption, Sophos Central Endpoint Advanced)
-
Broadcom (Symantec Endpoint Security Complete, Symantec Data Loss Prevention)
-
Trend Micro Incorporated (Trend Micro OfficeScan, Trend Micro Cloud One - Workload Security)
-
WinMagic (WinMagic SecureDoc, WinMagic SecureAnywhere)
-
Fortinet (FortiClient, FortiGate)
-
Palo Alto Networks (Prisma Access, Prisma Cloud)
-
Symantec (Symantec Endpoint Security Complete, Symantec Data Loss Prevention)
-
Thales (Thales Cryptographic Hardware Modules, Thales Cloud Protection and Licensing)
-
Entrust Datacard (Entrust Data Protection, Entrust Certificate Authority)
-
Gemalto (Gemalto SafeNet Data Protection, Gemalto Luna Hardware Security Modules)
-
CyberArk (CyberArk Privileged Access Management, CyberArk Identity Security)
-
Zscaler (Zscaler Zero Trust Exchange, Zscaler Internet Access)
RECENT TRENDS
-
In July 2024, Accenture and SandboxAQ are expanding their collaboration to meet the acute need for enterprise data encryption designed to protect against breaches of today's sensitive information, as well as the potential AI and quantum attacks tomorrow. Accenture is working with organizations to safeguard their confidential data and build the strength of their encryption technology portfolio with SandboxAQ.
-
In May 2024, A critical weakness in the GitHub Enterprise Server was discovered that bypassed authentication protections. This weakness was tracked as CVE-2024-4985, with a maximum CVSS score of 10.0.
| Report Attributes | Details |
|---|---|
| Market Size in 2023 | US$ 15.86 Billion |
| Market Size by 2032 | US$ 62.69 Billion |
| CAGR | CAGR of 16.6 % From 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Deployment Type (On-premise, Cloud-based) • By Application Type (Disk Encryption, File/Folder Encryption, Database Encryption, Web Communication Encryption, Network Traffic Encryption, Cloud Encryption, Others) • By End-use (BFSI, IT & Telecom, Retail, G&PA, Healthcare, Defense & Aerospace, Education, Manufacturing) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles | Bloombase, Cisco Systems, Inc., Check Point Software Technologies Ltd., Dell Inc., IBM Corporation, McAfee, LLC, Microsoft, Oracle, Sophos Ltd., Broadcom, Trend Micro Incorporated, WinMagic, Fortinet, Palo Alto Networks, Symantec, Thales, Entrust Datacard, Gemalto, CyberArk, Zscaler |
| Key Drivers | • Escalating Data Breach Costs Drive Demand for Encryption Software as Essential Defense Against Cyber Threats • Stringent Data Privacy Regulations Propel the Adoption of Encryption Software in a Data-Driven World |
| Restraints | • Complexity of Implementation Hinders Widespread Adoption of Encryption Software |

