Cloud Encryption Market Report Scope & Overview:
Get More Information on Cloud Encryption Market - Request Sample Report
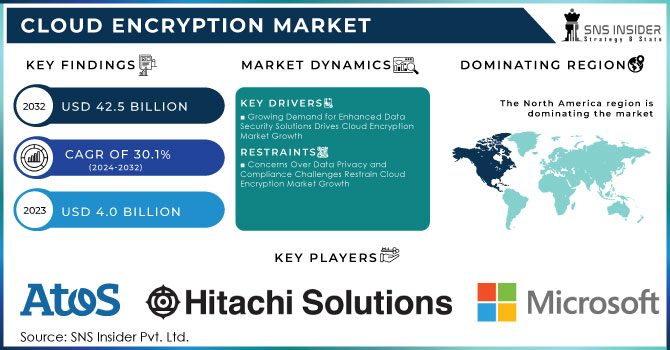
The Cloud Encryption Market Size was valued at USD 4.0 billion in 2023 and is expected to reach USD 42.5 billion by 2032 and grow at a CAGR of 30.1% over the forecast period 2024-2032.
The Cloud Encryption Market has experienced significant growth with large numbers of organizations focusing on the security of data in cloud infrastructures. This has mainly stemmed from the requirements for safeguarding sensitive information against cyber threats and meeting regulatory compliance requirements. Other key market dynamics are the increase in the volume of data produced across industries, the increasing instances of cyberattacks, and the increasing adoption of cloud services among all business entities. As companies migrate toward the cloud, security becomes the biggest concern for them: complex encryption technologies to safeguard static data as well as data under transmission must be on the top of their list. Another advancement that is opening up for them by the increasing popularity of AI/ML within the products of encryption is the prediction of threats in real time to thereby take the necessary precautions for mitigation in a way that is proactive and efficient.
The developments in cloud encryption technologies are more dynamic. For instance, in August 2024, Apple launched homomorphic encryption techniques to make secure cloud computing more efficient. The emerging technology allows for homomorphic computing-which processes encrypted data so that all the information remains private and confidential, even at times when analysis takes place. The usage of this advanced form of encryption will make it possible for organizations to execute their activities without sensitive information leaking out, thereby reducing any possibilities of breaches occurring and eventually boosting people's confidence in using cloud services. This is the major step forward in data security that can be assured, even when leveraging cloud computing capabilities.
With these advancements in the use of encryption methods, it is now key management strategies that have become critical. A report released in May 2024 stated that a good encryption approach would begin with efficient key management, reflecting its crucial role in the securing of data stored in the cloud. Dark Reading highlighted the development and encourages organizations to deploy centralized key management systems that would facilitate efficient creation, storage, and distribution of encryption keys that bolster their security posture and maintain confidential data protected from unauthorized use. The industry thinks that this development continues in its trend toward more comprehensive security frameworks that integrate the components of encryption, key management, and access controls for secure operations.
The cloud encryption market solutions have also grown as the transition of organizations to multi-cloud environments has increased. Companies call for encryption technologies that flexibly interoperate across different cloud platforms and preserve consistency in data protection against the particular cloud service provider. This has made encryption providers improve solutions that meet the compliance requirement but further add to performance and ease of use. The Cloud Encryption Market is rapidly evolving, mainly because of technological change and increased emphasis on data security, hence businesses can safely employ cloud computing while their essential information will be rightly protected.
Cloud Encryption Market Dynamics:
Drivers:
-
Growing Demand for Enhanced Data Security Solutions Drives Cloud Encryption Market Growth
As threats in cyberspace continue to be highly complex and pervasive, organizations can now attain optimum safety of data, especially in the cloud environment. The growing demand for higher data security solutions highly results in the high demand for the cloud encryption market. Businesses within several sectors increasingly realize that conventional safety measures cannot protect their sensitive information stored on the cloud. Due to this, organizations are using high-end encryption technology for the privacy and integrity of the data handled by the organization. Thus, the organizations have encrypted their data and stopped any unwarranted breaches. So as businesses produce sensitive data in massive amounts, with law compliance like GDPR, and HIPAA, the demand for encryption solutions will even rise more. This consequently pushes cloud encryption companies to devise pioneering and efficient solutions to serve the constantly rising security needs of their customers. This trend is likely to continue as the organizations get ready for digital transformation, which would involve the transition to infrastructures in the cloud, entailing a more robust form of data protection, whereby encryption shall play a pivotal role in ensuring a guarantee observing compliance and preventing unauthorized access to sensitive information.
-
Rapid Adoption of Cloud Computing Across Industries Fuels Cloud Encryption Market Expansion
The widespread acceptance of cloud computing by various types of organizations is one of the major drivers for the growth of the cloud encryption market. Organizations are shifting their operations and data to cloud services due to the cost-effectiveness, scalability, and better collaboration that cloud computing provides. However, with the shifting of their business operations to the cloud, these organizations face issues related to data security and privacy, which challenge them to encrypt their sensitive information. With cloud technologies being adopted in industries such as healthcare, finance, and e-commerce that are strictly regulated to prevent data breaches, effective encryption methods have emerged as the prime necessity. Moreover, with a large number of employees working remotely, organizations are shifting their services into the cloud at an unprecedented pace, thus further increasing demand for encryption products. By reacting to the trend in this way, cloud encryption providers offer solutions tailored to the industry needs hence enhancing the overall security of the cloud environment. With more people relying more and more on cloud computing, the cloud encryption market positions itself for one large expansion thrust by the imperative of secure data management in the digital age.
Restraint:
-
Concerns Over Data Privacy and Compliance Challenges Restrain Cloud Encryption Market Growth
Despite the promising market growth prospect for cloud encryption, data privacy and compliance challenges are major constraints. Organizations have to deal with numerous diverse regulatory frameworks and standards that govern data protection. The puzzle surrounding the ownership and jurisdiction of data in cloud services often provides birth to such concerns about sensitive information security. Challenges to Businesses will also have some issues that may impact their adherence to a few of the regulations mentioned here, such as GDPR, CCPA, and HIPAA, which require them to handle data in a very strict manner but still be transparent. This makes it hard for organizations to fully move into cloud encryption solutions since they might not be willing to risk sensitive data to a third-party cloud provider without complete assurance of privacy and compliance. Thus, a lack of clarity over regulation compliance may deter further expansion of the market because it slows up the decision-making processes and makes it more complicated to deploy encryption solutions. So, to make apprehensions minimal, proper communication and integrated security practices will have to clear such concerns.
Opportunity:
-
Increased Focus on Remote Work Creates Opportunities for Cloud Encryption Providers
Recent global events have accelerated a shift to remote work that has become a huge opportunity for cloud encryption providers. Organizations had to adapt to flexible work arrangements and come to rely more on tools and platforms in the cloud to enable communication, collaboration, and data storage. Cloud technology as such requires stronger security measures to safeguard sensitive information being accessed by remote employees. Businesses use cloud encryption services especially when workers access corporate assets from various locations and devices to ensure the integrity and confidentiality of data. These features make it possible for cloud encryption businesses to bring innovation and offer products that fit the different needs of remote workers by tailoring security needs. This demand also presents opportunities for developing converged solutions that leverage encryption in the context of identity and access management. With data security an imperative for organizations in enabling remote work, cloud encryption providers can seize on this demand by offering complete, intuitive solutions that assist organizations in protecting their data effectively while enabling productivity in a remote work environment.
Challenge:
-
Integration of Advanced Technologies in Cloud Encryption Solutions Presents Challenges
The cloud encryption market will grow bright, but the incorporation of advanced technologies within the framework of encryption solutions poses great challenges to that smooth growth. While organizations look for an opportunity to use AI and ML capabilities to provide enhancement to encryption solutions, they also face the challenge of adopting these technologies. The integration of AI and ML algorithms into the existing encryption framework poses such complex technical challenges it demands a significant investment in infrastructure along with skilled and experienced professionals. This can pose a challenge in maintaining the updating and relevance of the encryption solution as the rapid technological advancements usher in the emergence of new threats and vulnerabilities that pop up now and then. At the same time, it is essential not to let the interplay of these technologies adversely impact encryption solutions' performance or usability. The right balance between security advancements and user experiences challenges cloud encryption providers. So, navigating these will be key for providers that would want to provide innovative and effective encryption solutions to meet the needs of evolving security for organizations in an increasingly digital landscape.
Cloud Encryption Market Segmentation Overview
By Component
The Solutions segment dominated the cloud encryption market in 2023, which accounted for a revenue share of about 65% in the Cloud Encryption Market. The main reason behind this is the sheer increase in the demand for robust security solutions that protect sensitive data within cloud environments. Organizations are investing in advanced encryption solutions to have data confidentiality and to maintain compliance with regulatory requirements. For instance, companies like Thales and IBM have designed broad solutions for cloud encryption which permit companies to imperceptibly encrypt data across different applications of cloud. They are, therefore very significant in the current world since they have been outlined to be among the best means which can help prevent cyber threats as well as maintain integrity in data contained in clouds.
By Organization Size
Large Enterprises dominated the Cloud Encryption Market, accounting for about 70% in 2023. Such domination is solely because of the voluminous amounts of data created and processed by large organizations, which calls for advanced encryption solutions that can ensure the protection of sensitive information. Organizations like finance and healthcare biggies, such as JPMorgan Chase and UnitedHealth Group, are investing hugely in cloud encryption technologies for the sake of very strong regulations and to protect customer data. This will help them implement wholesome security frameworks that involve powerful encryption methods. This is driving demand for cloud encryption solutions that are designed for larger organizations.
By Service Model
In 2023, the Software-as-a-Service (SaaS) segment dominated the Cloud Encryption Market with a market share of about 50%. This growth has been due to the increased dependence on SaaS applications for business functions, which require elaborate data security measures. Companies such as Salesforce and Microsoft offer encrypted versions of their SaaS products so that customers' data is handled and stored safely in the cloud. With the growing organization migration towards SaaS platforms because of its agility and cost-effectiveness, the need for robustly encrypted solutions integrated into these services has increased appreciably, consecutively establishing the market leadership of this segment.
By End-use Vertical
The BFSI industry dominated the Cloud Encryption Market in 2023 and accounted for a revenue share of approximately 35%. The growing demand to encrypt and comply with regulations in the BFSI sector has fueled the need for cloud encryption technologies. For instance, Bank of America and Citibank employ cloud encryption technology to safeguard customer data from cyber threats while complying with demanding regulations as depicted by PCI DSS. Given the critical nature of data security in this sector together with soaring volumes of digital transactions, cloud encryption becomes inevitable, making it a core part of their IT strategy and thus increasing share of the segment in the market.
Cloud Encryption Market Regional Analysis
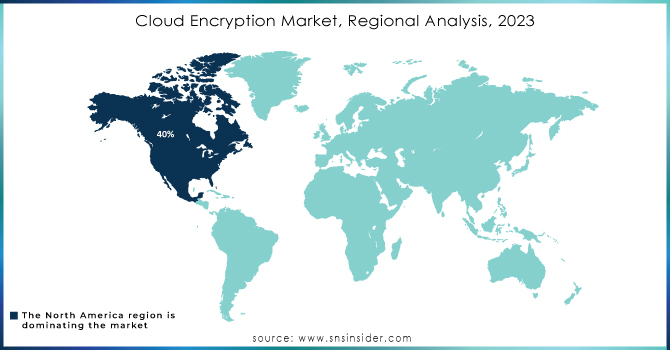
In 2023, the North America region dominated the Cloud Encryption Market, accounting for an approximate market share of about 40%. This is because the most significant players in the cloud service and technology arenas are headquartered in this region, including notable players such as Amazon Web Services (AWS), Microsoft, and Google Cloud. These firms are leading the charge in terms of designing and introducing sophisticated encryption solutions so that their customers may experience improved data security. Further, strict regulatory norms, such as GDPR and HIPAA, are compelling North American companies to maintain stringent encryption practices for the handling of confidential information. The increasing enterprise awareness of cybersecurity threats and large investments in cloud technologies have further cemented North America's position in the cloud encryption market.
Moreover, the Asia-Pacific emerged as the fastest growing region in the cloud encryption market, with an estimated CAGR of about 20%. This mainly comes from the rapid digital transformation happening across varied industries in countries such as India, China, and Australia. Increasing demand for effective encryption solutions is feeding the growth in the IT infrastructure space and also fuelling the adoption of cloud services with a blossoming startup ecosystem. This is the reason why there's an increasing trend of APAC businesses investing in cloud encryption technologies as they get to realize both the importance of data protection as well as compliance with the relevant regulatory environment. Companies like Alibaba Cloud and Tencent are dominating the market of advanced encryption services tailored towards the needs of regional businesses for their distinctive security needs, which are growing in this area.
Need any customization research on Cloud Encryption Market - Enquiry Now
Key Players in Cloud Encryption Market
-
Atos (Atos Cloud Encryption, Atos Secure Cloud)
-
Cisco Systems, Inc (Cisco Cloudlock, Cisco Encrypted Traffic Analytics)
-
Dell Technologies (Dell Data Protection Cloud, Dell EMC Cloud Tiering Appliance)
-
Hewlett Packard Enterprise (HPE Cloud Volumes, HPE Secure Compute)
-
Hitachi Solutions, Ltd (Hitachi Content Platform, Hitachi Data Instance Governance)
-
IBM (IBM Cloud Data Encryption, IBM Guardium Data Protection)
-
Micro Focus International plc (Micro Focus Voltage SecureData, Micro Focus Secure Content Management)
-
Microsoft (Azure Information Protection, Microsoft BitLocker)
-
Netskope Inc. (Netskope Cloud Security, Netskope Encryption)
-
Skyhigh Security (Skyhigh Cloud Security Platform, Skyhigh Data Protection)
-
Sophos Group plc (Sophos Cloud Optix, Sophos SafeGuard)
-
Thales Group (Thales CipherTrust Data Security Platform, Thales Cloud Encryption Gateway)
-
TWD Industries (TWD Data Encryption Services, TWD Secure Cloud Services)
-
WinMagic (WinMagic SecureDoc, WinMagic Cloud Encryption)
-
McAfee (McAfee MVISION Cloud, McAfee Complete Data Protection)
-
Amazon Web Services (AWS) (AWS Key Management Service, AWS CloudHSM)
-
Google Cloud (Google Cloud Data Loss Prevention, Google Cloud Key Management)
-
Box (Box KeySafe, Box Encryption Services)
-
Vormetric (part of Thales) (Vormetric Data Security Platform, Vormetric Transparent Encryption)
-
CipherCloud (CipherCloud Data Protection, CipherCloud Secure Data Exchange)
Cloud Service Providers in the Cloud Encryption Market
-
Amazon Web Services (AWS)
-
Microsoft Azure
-
Google Cloud Platform
Cybersecurity Firms for Cloud Encryption Market
-
Palo Alto Networks
-
Fortinet
-
Check Point Software Technologies
| Report Attributes | Details |
|---|---|
| Market Size in 2023 | US$ 4.0 Billion |
| Market Size by 2032 | US$ 42.5 Billion |
| CAGR | CAGR of 30.1% From 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Component (Solutions, Services {Professional Service [Support and Maintenance, Training and Education, Planning and Consulting], Managed services} • By Organization Size (Large Enterprises, Small and Medium-sized Enterprises (SMEs)) • By Service Model (Infrastructure-as-a-Service, Software-as-a-Service, Platform-as-a-Service) • By End-use Vertical (BFSI, Healthcare, Government and Public Utilities, Telecommunication and IT, Retail, Aerospace and Defense, Others) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe [Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles | Thales Group, Hitachi Solutions, Ltd, Hewlett Packard Enterprise, Sophos Group plc, IBM, Skyhigh Security, Netskope Inc., Microsoft, Micro Focus International plc, Dell Technologies, Cisco Systems, Inc, TWD Industries, Atos, WinMagic and other key players |
| Key Drivers | • Growing Demand for Enhanced Data Security Solutions Drives Cloud Encryption Market Growth • Rapid Adoption of Cloud Computing Across Industries Fuels Cloud Encryption Market Expansion |
| RESTRAINTS | • Concerns Over Data Privacy and Compliance Challenges Restrain Cloud Encryption Market Growth |

