Network Security Policy Management Market Size & Overview:
To Get More Information on Network Security Policy Management Market - Request Sample Report
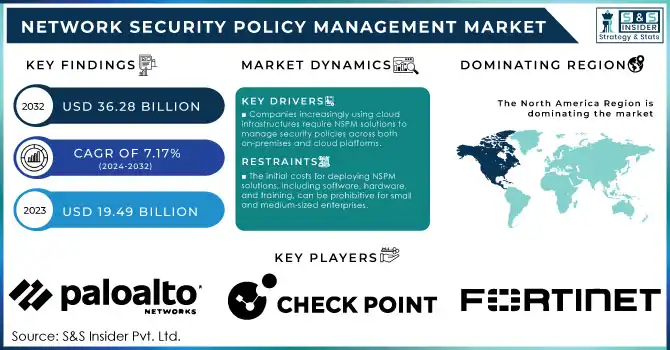
The Network Security Policy Management Market was valued at USD 19.49 billion in 2023 and is expected to reach USD 36.28 billion by 2032, growing at a CAGR of 7.17% from 2024-2032.
The Network Security Policy Management (NSPM) market is growing rapidly as demand for secure networks increases in our increasingly digital and interconnected world. As cyber threats become more sophisticated, businesses prioritize network security solutions to protect critical data and operations. NSPM solutions are essential for organizations, automating and simplifying the complex task of managing network policies across various devices and applications. In 2024, NSPM adoption has significantly risen, particularly within the banking, healthcare, and retail sectors, where compliance and data security are crucial. Industry data shows that nearly 60% of North American financial institutions have adopted advanced NSPM solutions this year to meet strict compliance standards and counter escalating cyber threats. One of the primary drivers of NSPM market growth is the widespread adoption of hybrid and multi-cloud environments. As companies increasingly rely on flexible cloud infrastructure, the need for solutions capable of managing security policies across both on-premises and cloud platforms has grown. Another factor boosting demand is the rise in remote work, initially driven by the pandemic, requiring businesses to secure remote access networks. Reports from 2024 indicate that approximately 70% of global enterprises have either implemented or plan to implement NSPM solutions to protect remote work environments.
A notable example of market growth is the early 2024 partnership between Palo Alto Networks and Google Cloud. This collaboration integrates Palo Alto’s NSPM tools with Google’s cloud platform, enabling businesses to manage policies more efficiently across multi-cloud environments. This partnership responds to a market demand for comprehensive NSPM solutions that effectively secure cloud-native applications. Recent advancements in AI and machine learning have further strengthened NSPM tools, allowing them to proactively detect and mitigate policy violations.
Global regulatory pressures are also a key factor in NSPM market growth. Stringent compliance regulations, such as GDPR in Europe and CCPA in California, are encouraging companies to adopt robust network security practices. With increased investments in network security infrastructure and the ongoing development of automated policy management, the NSPM market is poised for sustained growth in the coming years.
Network Security Policy Management Market Dynamics
Drivers
-
Companies increasingly using cloud infrastructures require NSPM solutions to manage security policies across both on-premises and cloud platforms.
-
With remote work rising, organizations need secure network access for remote employees, driving demand for NSPM solutions.
-
Enhanced AI capabilities in NSPM tools allow proactive threat detection and automated policy management, making them more appealing to organizations.
The introduction of improved AI functionality into Network Security Policy Management (NSPM) tools is changing the network security management landscape by taking the hard work out of threat detection and automating much of the policy management process. As enterprise network environments become increasingly complex due to factors such as cloud integration, hybrid infrastructures, and remote work, traditional manual network security policy management methods become inefficient and error-prone. AI-driven NSPM tools solve this problem easily by applying machine learning algorithms to measure network traffic patterns, spot risks, and even predict possible breaches of policies. For example, automated security tools can detect suspicious behavior, such as an unauthorized access attempt or an unusual data transfer, and flag it as a possible threat and instantly react to it.
Further lowering the administrative load on IT security teams, AI-driven automation in NSPM solutions. Handling security policies on many devices and applications using manual methods can be a time-consuming task that is prone to human error and hence, can also create potential vulnerabilities. AI-based NSPM tools simplify this by automating policy creation, enforcement, and modifications by triggering changes based on network state and detected threats. Such functionality is useful in fast-moving compliance environments, such as financial institutions and healthcare organizations that need to be on top of their policies and remain compliant with regulations by changing business environments. Some of the most talked-about instances of using AI for NSPM are where companies like Palo Alto Networks and Tufin automate complex policy management tasks in a multi-cloud environment using machine learning. As such, these solutions provide security teams with real-time visibility of network policies to quickly and accurately respond to possible breaches.
Restraints
-
Organizations with established security protocols may resist adopting new NSPM solutions due to concerns over disruption or unfamiliarity with the technology.
-
The initial costs for deploying NSPM solutions, including software, hardware, and training, can be prohibitive for small and medium-sized enterprises.
-
Integrating NSPM tools with existing, varied network systems can be challenging, potentially limiting widespread adoption in multi-vendor environments.
The integration of Network Security Policy Management (NSPM) tools into the existing network infrastructure is one of the biggest challenges for many organizations, especially in a multi-vendor scenario. Due to fragmented IT ecosystems more and more companies are using a variety of solutions from different vendors, introducing challenges like interoperability issues while deploying NSPM tools in the same environments. While these tools strive to centralize security policy management across multiple devices, applications, and networks, the integration with various systems can be both lengthy and challenging if disparate components do not operate seamlessly together. For example, NSPM tools can find it difficult to synchronize multiple firewalls, routers, switches, and other security appliances from multiple vendors under one management umbrella. Such limited interoperability, however, can lead to inconsistent policy enforcement and security holes, or create administrative headaches. Hence, legacy systems or custom integrations taking place at the same time make this integration process very cumbersome and expensive to deploy.
Additionally, multi-vendor solutions are not static. The pace of these changes forces organizations into never-ending cycles of adaptation that NSPM solutions should be designed to enable, however many solutions are not built for this rapid cadence. This means organizations may struggle to make certain their NSPM solutions enjoy compatibility with all the latest styles of technology knowing that they can conduct fantastic safety insurance policy management throughout evolving surroundings. As a result, the complexity of integrating NSPM tools in complex, multi-vendor networks are one of the market restraining factors, especially for large, decentralized organizations. NSPM providers are working on more flexible and adaptable solutions that can be easily integrated with varied network configurations and third-party security products to solve this problem.
Network Security Policy Management Market Segment Analysis
By Component
The solutions segment leads the market with a revenue share of 69.25% in 2023. owing to the growing need for network security technologies which are more advanced. Across the industry, organizations spend heavily on NSPM tools to simplify policy management, automate processes, minimize complexity, and improve security. This growth is driven by the increasing demand for solutions that provide management for complex network infrastructures, particularly in hybrid and multi-cloud environments. Also, the growing adoption of AI-powered features integrated solutions & compatibility with cloud platforms is anticipated to boost the solutions market. Cyber threats are still evolving, and this gives rise to better solutions that allow the segment to keep growing in light of more proactive security from automation, AI, and machine learning.
The services segment is expected to grow at the highest CAGR of 8.24%, Driven by the increasing complexity in the implementation and maintenance of NSPM solutions. Several organizations need specialized knowledge to incorporate NSPM tools within their network systems, resulting in a greater need for professional services. With digital transformation initiatives underway, businesses are stepping up their security efforts, driving demand for expert consulting, customization, and managed services. Due to the increase in the adoption of hybrid IT environments in business and the demand to outsource security management, the services segment will grow at a rapid pace. And, as security challenges continue to evolve, businesses are expected to tap into external expertise to deal with the threat landscape, making this segment grow.
By Organization Size
In 2023, large enterprises have a major share of 72.25% in the NSPM market because of their large and complex network infrastructures. These organizations need strong NSPM solutions to help them manage large volumes of data, applications, and devices across numerous sites and clouds. That means large enterprises are mainly driven to adopt NSPM due to the continuous rise of cyber threats, and the urge to comply with regulatory requirements. With these businesses transitioning digitally and moving to hybrid or multi-cloud environments, the need for scalable NSPM solutions that integrate to ones such as hybrid cloud becomes essential. The rise of this sector is likely to stay in its function, driven by a constant flow of funding for high-security technologies.
The SME sector is the fastest-growing segment with CAGR of 7.57% in the NSPM market since most of these small & medium enterprises business entities prefer to adopt similar digital, cloud-enabled solutions. As cyber threats become more advanced, many SMEs are recognizing the need for robust network security policies to safeguard sensitive information and ensure compliance with regulations. This demand for middle-of-the-road slopes up cost-effective, scalable NSPM solutions, is driven by increasing cloud adoption and trending remote work. Pairing these solutions with cloud-native security and automated policy management will further bolster the demand for NSPM tools across the globe as SMEs strive to strengthen their security posture. Considering the future of the SME segment, the story is a lot better, with rising investments in digital security technologies.
Network Security Policy Management Market Regional Analysis
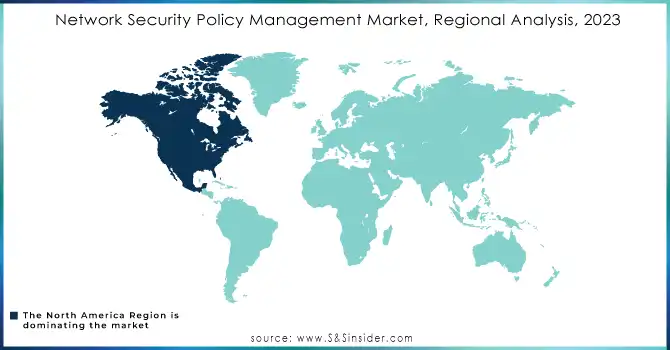
North America accounts for the largest share of the Network Security Policy Management (NSPM) market in 2023, due to the presence of well-established IT infrastructure and high adoption of network security solutions in the region. Major NSPM vendors such as Palo Alto Networks and Fortinet, along with firm cybersecurity regulations—particularly in the finance and healthcare sectors—are key factors that guide growth. Further, the increasing cyber threats against critical sectors present a major opportunity for NSPM solutions across North America. With the increasing adoption of cloud and hybrid IT environments, enterprises of all sizes are investing in NSPM to secure their distributed networks. The growth in this region is expected to continue rising owing to seismic investment into Security solutions leveraging AI to build proactive detection of threats and policy automation.
The NSPM market in Asia-Pacific is growing with the highest CAGR as rapid digital transformation, coupled with growing cybersecurity awareness among enterprises in emerging economies, such as India and Southeast Asia, is driving the growth of the NSPM market. With enterprises in this region increasingly adopting cloud services and remote work arrangements, the demand for next-generation NSPM solutions that protect hybrid and multi-cloud environments is likely to rise. These increasing threats have led to the enhancement of cybersecurity frameworks for governments in the Asia-Pacific region which is also enabling demand for compliant and scalable NSPM tools. Investments in IT infrastructure are expanding while the focus is shifting toward making the system cyber-safe, which will benefit the robust expansion of the NSPM market space in Asia-Pacific, complemented by the adoption of AI-based and ML-based technologies to facilitate automated policy management.
Do You Need any Customization Research on Network Security Policy Management Market - Enquire Now
Key Player
-
Cisco Systems - Cisco Secure Network Analytics
-
Palo Alto Networks - Panorama
-
Check Point Software Technologies - CloudGuard Network Security
-
Fortinet - FortiManager
-
Tufin - Tufin Orchestration Suite
-
AlgoSec - AlgoSec Security Management Suite
-
FireMon - FireMon Policy Planner
-
McAfee - McAfee Policy Auditor
-
Juniper Networks - Junos Space Security Director
-
Skybox Security - Skybox Security Suite
-
Trend Micro - Trend Micro Network Security
-
Symantec (Broadcom) - Symantec Control Compliance Suite
-
Forcepoint - Forcepoint Network Security
-
IBM - IBM QRadar Network Security
-
Huawei - Huawei CloudFabric Security Solution
-
Sophos - Sophos XG Firewall
-
VMware - VMware NSX
-
Micro Focus - ArcSight ESM
-
F5 Networks - F5 BIG-IP Policy Enforcement Manager
-
Barracuda Networks - Barracuda CloudGen Firewall
Recent Developments
-
March 2024 - Palo Alto Networks announced a strategic partnership with Microsoft to integrate its NSPM solutions with Azure’s security services, providing real-time, unified policy management across cloud and on-premises networks.
-
May 2024 - AlgoSec introduced enhanced risk assessment features in its NSPM solutions, allowing organizations to proactively identify and mitigate potential vulnerabilities in complex, multi-vendor networks.
-
July 2024 - FireMon released a cloud-native NSPM tool specifically targeting small and medium-sized enterprises (SMEs) to support streamlined policy management in multi-cloud setups.
| Report Attributes | Details |
| Market Size in 2023 | US$ 19.49 Bn |
| Market Size by 2032 | US$ 36.28 Bn |
| CAGR | CAGR of 7.17% from 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Product Type (Change Management, Network Compliance Policy, Vulnerability Assessment, Network Policy Management) • By Component (Solution, Services) • By Organization Size (Medium Size Enterprise, Large Scale Enterprise) • By End-use (IT and Telecom, Energy and Utilities, Retail, Manufacturing, Healthcare) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles | Cisco Systems, Palo Alto Networks, Check Point Software Technologies, Fortinet, Tufin, AlgoSec, FireMon, McAfee, Juniper Networks, Skybox Security, Trend Micro, Symantec, Forcepoint, IBM, Huawei, Sophos, VMware, Micro Focus, F5 Networks, Barracuda Networks |
| Key Drivers | • Companies increasingly using cloud infrastructures require NSPM solutions to manage security policies across both on-premises and cloud platforms. • With remote work rising, organizations need secure network access for remote employees, driving demand for NSPM solutions. • Enhanced AI capabilities in NSPM tools allow proactive threat detection and automated policy management, making them more appealing to organizations. |
| Market Restraints | • Organizations with established security protocols may resist adopting new NSPM solutions due to concerns over disruption or unfamiliarity with the technology. • The initial costs for deploying NSPM solutions, including software, hardware, and training, can be prohibitive for small and medium-sized enterprises. • Integrating NSPM tools with existing, varied network systems can be challenging, potentially limiting widespread adoption in multi-vendor environments. |

