Passive Authentication Market Size & Overview:
Get more information on Passive Authentication Market - Request Sample Report
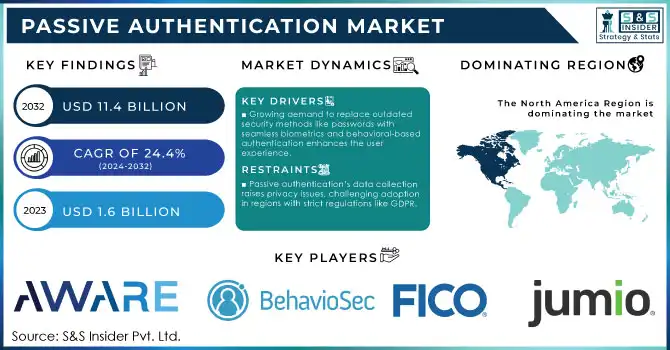
The Passive Authentication Market size was valued at USD 1.6 billion in 2023 and is expected to reach USD 11.4 billion by 2032, growing at a CAGR of 24.4% over the forecast period of 2024-2032.
Growth in the passive authentication market across the globe owing to the rise in cyber threats, identity theft, and fraud including the booming trend of online shopping and selling items. Governments are responding with stronger regulatory frameworks to ensure data security and user privacy, promoting the adoption of passive authentication solutions. With a 13% increase in identity fraud reported by U.S. authorities in 2023, passive authentication solutions have gained considerable traction across banking, healthcare, and government sectors. As both public and private sectors invest more and more heavily, market analysts expect the passive authentication market to keep on growing, driven in particular by pressure from governments for ever-greater data security.
Passive authentication eliminates the need for users to recall complex passwords, improving ease and user experience. These solutions are scalable, cost-effective, and easy to deploy because they are cloud-based, making them ideal for organizations of any size. Cyber threats have been increasing at an immense rate, and organizations now know that they need advanced security measures, so that passive authentication can protect access. Identity verification helps to comply with regulations such as GDPR and CCPA, which require strong user authentication. The use of biometric authentication, where a user is authenticated based on characteristics such as fingerprint, facial recognition, and iris scanning, is also advancing, leading to more reliable passive authentication and prompting its wider adoption. These are anticipated to lead to persistent growth opportunities within the passive authentication market, as technology advances and better solutions are made available.
Passive Authentication Market Dynamics
Drivers
-
Growing demand to replace outdated security methods like passwords with seamless biometrics and behavioral-based authentication enhances the user experience.
-
High-security industries adopt passive authentication to enhance security and meet user demands for smooth, unobtrusive verification.
-
AI-driven behaviour analysis strengthens passive authentication, providing adaptive and continuous security without user interruption.
One of the major drivers for the passive authentication market is the shift away from traditional security methods like passwords and security questions toward more advanced biometrics and behaviour-based systems. With the ever-evolving nature of cyber threats, organizations are quickly realizing that traditional authentication methods, which depend heavily on static passwords that can be easily hacked, have serious shortcomings. The recent report states that more than 80% of data breaches involve brute-force attacks or stolen passwords, which emphasizes the importance of harder-to-crack security options that are not solely dependent on passwords.
Passive authentication is a highly seamless method of identifying users based on biometric data (facial recognition, fingerprints, and voice analysis) and behavioral analytics (typing speed and mouse movement patterns) without asking the users to do anything. Though not all implementations of AI have succeeded, several examples like HSBC have successfully adopted the technology after implementing voice biometrics in its customer service centers, HSBC secured the identification of customers with a 93% accuracy rate in 30 seconds, improving security and user experience . In 2023, HSBC replaced its traditional customer support with AI. MasterCard, too, has been implementing fingerprint scans and facial recognition to better authenticate online transactions. Moreover, with 57% of consumers preferring password-less biometric verification as opposed to password authentication, there is an evident user preference for biometric schemes when looking at newer schemes alternative to traditional passwords. This shift is a long time coming, in line with industry trends to provide non-disruptive user-centric security to increase the adoption of passive authentication systems.
Restraints
-
Passive authentication’s data collection raises privacy issues, challenging adoption in regions with strict regulations like GDPR.
-
Initial setup costs, especially for small businesses, can limit the adoption of passive authentication technology.
Privacy & Data Protection are the major restraints for the global passive authentication market to enable passive authentication systems to monitor and analyze user behaviour in real time, these systems must collect large volumes of personal data. This continuous data tracking can raise privacy issues, especially in regions with strict data protection regulations, such as GDPR in Europe. Such regulations mandate that organizations transparently handle and protect user data, often requiring them to obtain explicit consent from users. This also makes passive authentication more difficult to adopt because businesses need to navigate complicated legal requirements around privacy. Even worse, a leak of sensitive behavioural data which would occur in the event of a breach is also a risk that raises fears. To overcome these challenges, organizations should spend heavily on encrypting and anonymizing all the data they are working with so that no personal information itself is stored in its applications, which makes implementation much more complex and costly.
Passive Authentication Market Segment Analysis
By Component
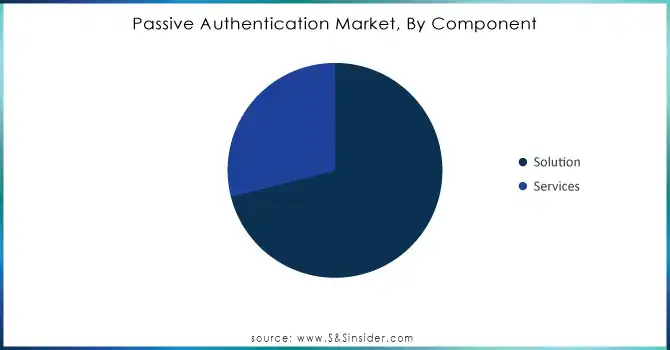
The solution segment held the largest share of 71% of revenue in the passive authentication market in 2023, owing to the ability to authenticate users without the need for active participation passive authentication solutions utilize sophisticated technologies such as biometrics and behavioural analysis to achieve seamless user authentication, making them ideal for highly secure but low user interaction environments. These solutions accommodate strict security protocols preferred by governments so organizations can stay compliant and still respect end-user privacy. In addition, improved AI and machine learning will continue to drive the development and, viability of passive authentication technologies.
Need any customization research on Passive Authentication Market - Enquiry Now
By Deployment
The cloud deployment segment held the largest revenue share 60% in 2023 due to the increasing migrations of organizations to the cloud for supporting scalability and remote access. For instance, the U.S. government has promoted cloud migration via initiatives such as FedRAMP (the Federal Risk and Authorization Management Program) which certifies cloud security for federal use. Recent trends in low cost and ease of deployment where the locations are diversified are moving towards the passive authentication which further fuels the cloud segment.
By Function
The compliance management segment accounted for 31% of revenue share as organizations are keen on complying with government regulations to avoid penalties and protect consumer data. One of the key features of passive authentication is that it helps ensure compliance by automatically monitoring and authenticating identities, which is crucial in regulated sectors like finance or healthcare. With the launch of regulations such as GDPR and CCPA the need for passive authentication became critical for businesses to retain compliant operations, thereby fuelling the need for compliance management focused solutions.
Passive Authentication Market Regional Analysis
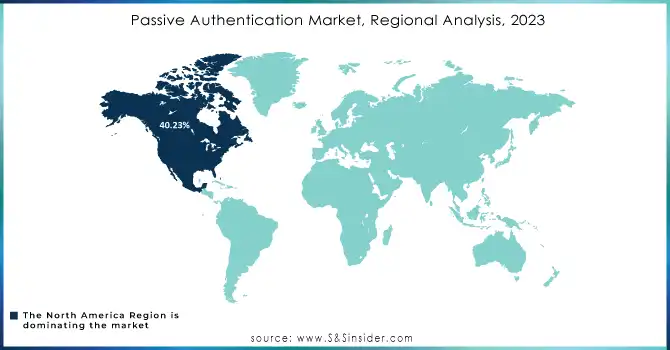
North America dominated the passive authentication market in terms of revenue in 2023, due to the strong government policies associated with cybersecurity and data privacy. This is primarily attributable to the dominance of the United States due to its strong base of technology and financial sectors, which typically focus on passive authentication solutions to protect against unauthorized access & identity theft. Policies like the U.S. Cybersecurity Framework and other federal initiatives aim to bolster digital security across critical industries, creating a fertile environment for the adoption of advanced authentication technologies.
The passive authentication market in the U.S. is projected to grow significantly over the coming years. U.S. consumers prioritize smooth and quick online interactions, especially for services like banking, shopping, and other digital platforms. With passive authentication, people no longer need to memorize complex passwords or have to use MFA every time, so access is instant and easy, improving the user experience considerably. Moreover, mobile wallet adoption is increasing in America and passive authentication works seamlessly with these mobile payment systems to easily and securely process transactions for users. This seamless integration of passive authentication with mobile payment options not only supports security but also meets the demand for a streamlined digital experience in daily financial activities.
Meanwhile, the Asia-Pacific region emerged as the fastest-growing market, driven by high growth rates in countries such as China and India. The increasing volume is driven by investments in digital infrastructure, together with government programs to drive digital adoption both in the public and the private sectors. For example, India’s Digital India initiative and China’s focus on Smart City development have accelerated the adoption of digital services, leading to a higher volume of online transactions and mobile banking. This digital explosion has also resulted in a greater demand for secure, seamless authentication solutions to counterbalance the rising risk of cyber threats and fraud.
Recent Developments in the Passive Authentication Market
- NEC Corporation of America released NeoFace® Reveal Version 5, the next-generation forensic face recognition technology, in March 2024. It specifically targets government agencies and law enforcement as well as civil applications by organizations as it has introduced this advanced software that is expected to revolutionize criminal investigations and fraud prevention. The NeoFace® Reveal version 5 enhances identity verification accuracy and efficiency enabling authorities to detect fraud and reduce the burden of investigative processes.
Key Players
Service Providers / Manufacturers:
-
Aware Inc. (Biometrics Solutions for Financial Services)
-
BehavioSec (Behavioral Authentication for Financial Institutions)
-
Cisco Systems, Inc. (Network Security and Identity Verification)
-
FICO (Fraud Prevention Solutions for Banks and Retailers)
-
International Business Machines Corporation (IBM) (AI-powered Fraud Detection for Enterprises)
-
Jumio (Identity Verification for E-commerce and Financial Services)
-
NEC Corporation of America (Smart City Authentication Solutions)
-
OneSpan (Digital Identity and Authentication for Banks)
-
Source (Data Security for Digital Transactions)
-
Thales (Data Encryption and Identity Verification for Government and Defense)
Key Users of Passive Authentication Products/Services:
-
JPMorgan Chase
-
HSBC
-
PayPal
-
Uber
-
Walmart
-
Citibank
-
American Express
-
Amazon
-
Microsoft
-
Apple
| Report Attributes | Details |
|---|---|
| Market Size in 2023 | USD 1.6 billion |
| Market Size by 2032 | USD 11.4 billion |
| CAGR | CAGR 24.4% from 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Component (Solution, Services) • By Organization Size (SMEs, Large Enterprises) • By Function (Compliance Management, Marketing Management, Risk Management, Others) • By Deployment (Cloud, On-premises) • By Vertical (BFSI, Government, IT & Telecommunications, Retail and Consumer Goods, Healthcare, Media and Entertainment, Others) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles | Aware Inc, BehavioSec, Cisco Systems, Inc., FICO Company, International Business Machines Corporation, Jumio, NEC Corporation of America, OneSpan, Source, Thales |
| Key Drivers | • Growing demand to replace outdated security methods like passwords with seamless biometrics and behavioral-based authentication enhances the user experience. • High-security industries adopt passive authentication to enhance security and meet user demands for smooth, unobtrusive verification. • AI-driven behavior analysis strengthens passive authentication, providing adaptive and continuous security without user interruption. |
| Market Restraints | • Passive authentication’s data collection raises privacy issues, challenging adoption in regions with strict regulations like GDPR. • Initial setup costs, especially for small businesses, can limit the adoption of passive authentication technology. |

