Cloud Data Security Market Key Insights:
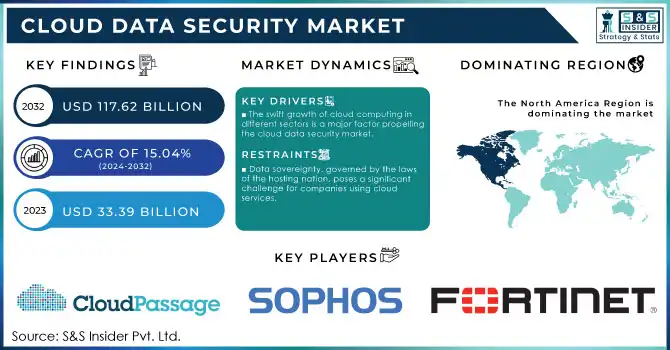
The Cloud Data Security Market size was valued at USD 33.39 Billion in 2023 and is expected to reach USD 117.62 Billion by 2032, growing at a CAGR of 15.04% over the forecast period 2024-2032.
To Get More Information on Cloud Data Security Market - Request Sample Report
The cloud data security market has seen tremendous growth recently, fueled by the widespread adoption of cloud-based services and a rising need for data protection solutions. Companies of all sizes are leveraging cloud solutions to boost efficiency, cut costs, and improve productivity. Today, 96% of businesses use public cloud services, and 84% utilize private cloud solutions, with an estimated 60% of business data now residing in the cloud. Notably, 48% of organizations store their most critical data in cloud environments. However, this shift to the cloud introduces cybersecurity risks, as cloud environments are often targeted by cybercriminals. Data breaches can lead to significant financial losses, reputational harm, and legal consequences, making cloud data security solutions crucial. For instance, in 2024, data breaches have an average projected cost of nearly USD 4 million globally. To mitigate these threats, businesses are increasingly investing in encryption technology, access management tools, data loss prevention (DLP) systems, and threat intelligence solutions to secure data across its lifecycle—from storage and processing to transmission.
Encryption is a cornerstone of cloud data security, ensuring that data remains unreadable to unauthorized users. This is especially vital for organizations handling sensitive information like financial data, healthcare records, and personally identifiable information (PII). Cloud service providers (CSPs) offer options for encryption at rest and encryption in transit, giving businesses the flexibility to adopt CSP-managed or self-managed encryption solutions—or a combination of both—to meet specific security needs.
Market Dynamics
Drivers
- The swift growth of cloud computing in different sectors is a major factor propelling the cloud data security market.
As companies continue to shift to cloud platforms, they encounter new security issues concerning the safeguarding of sensitive information. Cloud services offer scalability, adaptability, and cost-effectiveness, yet these benefits are accompanied by the dangers of unauthorized access, data breaches, and cyber threats. With the increase in cloud adoption, the need for strong cloud data security solutions also rises. Businesses need to confirm that information kept in the cloud is safe, encrypted, and adheres to regulations. The increasing reliance on cloud services for vital functions, including customer data handling, financial activities, and intellectual property storage, has rendered cloud data security a crucial element of enterprise risk management plans. This pattern is especially noticeable in areas such as finance, healthcare, government, and retail, where safeguarding data is a major concern. Additionally, the growth of remote work and the heightened adoption of cloud-based collaboration tools have expanded the attack surface, creating a demand for more thorough cloud security measures.
- The increasing occurrence and complexity of cyberattacks have driven the need for cloud data security solutions.
Cybercriminals are increasingly skilled at taking advantage of weaknesses in cloud infrastructures, aiming at both the cloud service providers and the businesses that utilize them. There were 2,365 cyberattacks in 2023, with 343,338,964 victims. Risks including ransomware, phishing attempts, and insider threats are increasingly common and more difficult to manage. The magnitude of these dangers necessitates that organizations implement a multi-faceted security strategy encompassing encryption, identity and access management, threat detection, and incident response functionalities. The growing reliance on cloud storage for confidential data has turned it into a key target for hackers, thereby increasing the need for sophisticated security solutions. Cloud providers are upgrading their security protocols to safeguard their infrastructure, while companies are purchasing external security solutions to protect data before uploading it to the cloud. The ongoing necessity to safeguard cloud data from both external and internal threats is therefore a key factor propelling the expansion of the cloud data security market.
Restraints
- Data sovereignty, which refers to the principle that data is governed by the laws and regulations of the nation where it is held, poses a considerable challenge for companies utilizing cloud services.
Various nations possess diverse rules regarding data protection and privacy, which may lead to challenges for organizations functioning globally. For instance, the European Union’s GDPR enforces rigorous regulations on data storage and handling, whereas nations such as the United States implement their own laws regarding data security. When data is kept in a cloud setting, it can be distributed across various jurisdictions, complicating compliance with local laws for organizations. This complexity may restrict the selection of cloud providers for certain businesses, especially those in heavily regulated sectors such as healthcare, finance, and government. Organizations need to manage these legal and regulatory hurdles to guarantee that their data is stored securely and adheres to all relevant laws, which can notably limit the adoption of cloud data security solutions.
Key Segmentation Analysis
By Offering
The solution dominated the market, holding a 69% market share in 2023. Solutions can include encryption technologies, identity and access management (IAM) systems, data loss prevention (DLP), and cloud firewall services. For example, McAfee Cloud Security provides integrated protection against data breaches, while Palo Alto Networks Prisma Cloud focuses on securing cloud infrastructures through continuous monitoring and vulnerability management.
The services segment is expected to experience the fastest CAGR during 2024-2032. As organizations seek specialized expertise and resources to manage and mitigate cloud security risks, the demand for professional services continues to grow. Companies like IBM Security and Accenture offer cloud security consulting, incident response, and risk management services to help businesses enhance their security posture. IBM's Cloud Security Services integrate cloud security assessments, vulnerability management, and compliance consulting to ensure seamless protection across cloud platforms.
By Type
The fully managed segment dominated with more than 55% market share in 2023. A fully managed security solution involves outsourcing all aspects of data security to a third-party provider. It eliminates the complexities of managing infrastructure and reduces the burden of maintaining in-house teams. For example, IBM and Palo Alto Networks offer fully managed security solutions, providing end-to-end cloud security services that help organizations safeguard data from breaches and cyber threats
The co-managed is expected to grow at a faster rate during 2024-2032, driven by businesses that prefer to retain some control over their security while benefiting from third-party expertise. With co-managed services, the organization shares the responsibility for security with the provider. For instance, companies like Check Point Software Technologies and Microsoft offer co-managed solutions, helping organizations manage cloud data security with shared responsibilities and giving businesses a balance of autonomy and expertise.
Regional Analysis
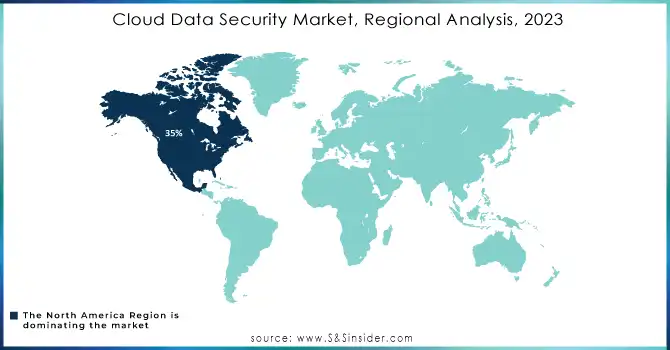
In 2023, North America dominated the cloud data security market with a 35% market share, fueled by the significant presence of key players and robust demand for cutting-edge cybersecurity solutions. The United States, specifically, hosts leading cloud data security firms such as McAfee, Symantec, and Palo Alto Networks, providing extensive cloud security solutions for both businesses and government entities. These firms offer services like threat analysis, data encryption, and secure access measures to protect sensitive information in cloud settings.
Asia-Pacific is anticipated to become the fastest-growing market from 2024 to 2032, driven by swift digital transformation and heightened cloud computing adoption in various industries. Nations such as China, India, Japan, and South Korea are experiencing substantial increases in cloud service adoption, especially within industries like e-commerce, banking, and manufacturing. As companies in APAC grow their online presence, the demand for strong data security against cyber risks increases. Firms such as Trend Micro (Japan) and Zscaler (India) are significantly investing in creating cloud-focused security solutions designed for the local market.
Do You Need any Customization Research on Cloud Data Security Market - Inquire Now
Key Players
The major key players in the Cloud Data Security Market are:
-
Cloud Passage Inc. (Halo, Halo for AWS)
-
Intel Corporation (Intel Security, Intel vPro)
-
Sophos Ltd. (Sophos Cloud Optix, Sophos XG Firewall)
-
Fortinet, Inc. (FortiGate, FortiCloud)
-
IBM Corporation (IBM Cloud Security, IBM QRadar)
-
Cisco Systems, Inc. (Cisco Umbrella, Cisco Cloudlock)
-
Symantec Corporation (Symantec Data Loss Prevention, Symantec Cloud Security)
-
Trend Micro, Inc. (Trend Micro Cloud One, Trend Micro Deep Security)
-
Panda Security (Panda Adaptive Defense, Panda Cloud Office Protection)
-
CA Technologies, Inc. (CA Privileged Access Manager, CA Security Event Manager)
-
McAfee (McAfee MVISION Cloud, McAfee Cloud Workload Security)
-
Microsoft (Microsoft Defender for Identity, Microsoft Azure Security Center)
-
Vormetric (a Thales company) (Vormetric Data Security Platform, Vormetric Transparent Encryption)
-
Check Point Software Technologies (CloudGuard, Check Point Threat Emulation)
-
Forcepoint (Forcepoint Data Loss Prevention, Forcepoint Cloud Security)
-
Palo Alto Networks (Prisma Cloud, Cortex XSOAR)
-
Zscaler (Zscaler Internet Access, Zscaler Private Access)
-
Okta (Okta Identity Cloud, Okta Adaptive MFA)
-
Rapid7 (InsightCloudSec, InsightIDR)
-
Imperva (Cloud WAF, Imperva Data Security)
Suppliers providing software or components to these key players:
-
Red Hat (Red Hat OpenShift)
-
Oracle (Oracle Cloud Infrastructure, Oracle Security Service)
-
F5 Networks (BIG-IP, Silverline)
-
A10 Networks (Thunder ADC, A10 Harmony)
-
Amazon Web Services (AWS) (AWS Key Management Service, AWS CloudTrail)
-
Google Cloud (Google Cloud Identity, Google Cloud Data Loss Prevention)
-
Qualys (Qualys Cloud Platform, Qualys Web Application Scanning)
-
CyberArk (CyberArk Identity, CyberArk Privileged Access Security)
-
CrowdStrike (CrowdStrike Falcon, CrowdStrike Cloud Security)
-
Cloudflare (Cloudflare Gateway, Cloudflare Web Application Firewall)
Recent Developments
-
August 6, 2024: Fortinet acquired Next DLP, a leader in enterprise data security. This acquisition is set to enhance Fortinet's data loss prevention (DLP) capabilities and integrate them into its unified Secure Access Service Edge (SASE) solution, reinforcing its security across endpoints and cloud environments.
-
October 30, 2024: AWS has introduced new security group sharing features that simplify the management of your security groups. With shared VPC, it is now possible to share security groups with participant accounts within that shared VPC through Shared Security Groups.
-
September 2024: Tata Consultancy Services (TCS) has revealed the expansion of its collaboration with Google Cloud to introduce two innovative AI-driven cybersecurity solutions designed to enhance enterprise cyber resilience.
| Report Attributes | Details |
|---|---|
| Market Size in 2023 | USD 33.39 Billion |
| Market Size by 2032 | USD 117.62 Billion |
| CAGR | CAGR of 15.04% From 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Offering (Solution, Services) • By Type (Fully Managed, Co-Managed) • By Deployment (Private, Hybrid, Public) • By Organization Size (SMEs, Large Enterprises) • By End User (BFSI, Retail and eCommerce, Government and Defense, Healthcare and Life Sciences, IT and ITeS, Telecom, Others) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles | Cloud Passage Inc., Intel Corporation, Sophos Ltd., Fortinet, Inc., IBM Corporation, Cisco Systems, Inc., Symantec Corporation, Trend Micro, Inc., Panda Security, CA Technologies, Inc., McAfee, Microsoft, Vormetric (a Thales company), Check Point Software Technologies, Forcepoint, Palo Alto Networks, Zscaler, Okta, Rapid7, Imperva, AWS, TCS |
| Key Drivers | • The swift growth of cloud computing in different sectors is a major factor propelling the cloud data security market. • The increasing occurrence and complexity of cyberattacks have driven the need for cloud data security solutions. |
| RESTRAINTS | • Data sovereignty, which refers to the principle that data is governed by the laws and regulations of the nation where it is held, poses a considerable challenge for companies utilizing cloud services. |

