Cloud Security Market Size & Overview:
To Get More Information on Cloud Security Market - Request Sample Report
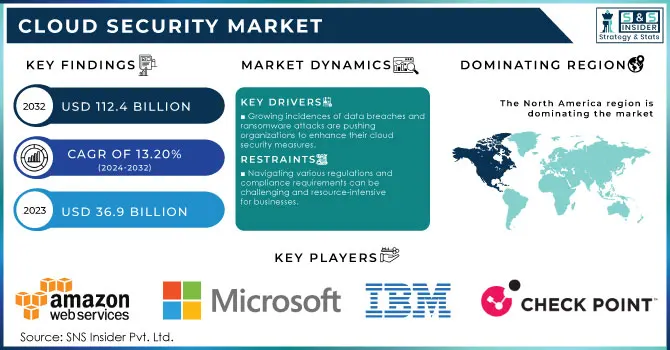
Cloud Security Market was valued at USD 36.9 billion in 2023 and is expected to reach USD 112.4 Billion by 2032, growing at a CAGR of 13.20% from 2024-2032.
The Cloud Security Market is witnessing strong growth, fueled by the migration of enterprises to cloud environments where advanced security solutions are required to secure sensitive data and meet regulatory standards. As cyber threats such as data breaches and ransomware attacks continue to emerge, businesses are placing a higher priority on cloud security. One of the prominent factors that is responsible for such market growth is an increasing implementation of hybrid and multi-cloud approach that needs unified security across various platforms. Stealthy cybercrime attacks will cost the world USD 10.5 trillion dollars damages annually by 2025 according to a recent report by Cybersecurity Ventures, urgently demandting security fortifications against such threats in cloud infrastructures. According to recent stats, 81% of organizations experienced a cloud security incident over the past year alone, showing that the need for all-encompassing security solutions is greater than ever. Meanwhile, the need to comply with increasing regulatory pressures–from the General Data Protection Regulation (GDPR) in Europe and HIPAA compliance in various states across the U.S.–is also driving organizations toward cloud security investments to avoid millions of dollars’ worth of fines and worse, reputational damage.
Additionally, including artificial intelligence (AI) and machine learning (ML) technologies in cloud security solution options is changing threat detection and response functionalities. Customers utilizing AI for cybersecurity, according to survey, AI for cybersecurity experienced a 45% quicker decline in incident response time. This showcases the efficiency of such technologies in contributing towards cloud security posture.
In addition, the adoption of Software-as-a-Service (SaaS) applications by businesses is escalating the need for identity and access management (IAM) solutionOn the whole, due to alarming cyber threats and compliance in the rapidly digitalizing environment, the Cloud Security Market is poised for massive growth.
Cloud Security Market Dynamics
-
Growing incidences of data breaches and ransomware attacks are pushing organizations to enhance their cloud security measures.
-
The shift to remote work has increased the reliance on cloud services, amplifying the need for secure access and data protection.
-
Organizations are prioritizing data protection strategies to maintain customer trust and safeguard sensitive information.
In the modern era, data protection is no longer just about compliance; organizations understand that it is equally essential to gain customer trust and protect critical information. This emphasis in relation to the Cloud Security Market highlights how investors are becoming increasingly cognizant of the risks posed by data breaches and other cyber threats. With businesses moving more towards cloud environments, they're exposed to a wider range of attacks that could expose key information such as consumer data, financial records and intellectual property.
In order to reduce these risks, companies are focusing on reliable cloud security solutions that protect data. These strategies include a series of practices from encryption and identity-and-access management (IAM) to threat detection, incident response, etc. Encryption offers data-at-rest, and in-transit security so that even if unauthorized access happens, the data will be unreadable. IAM solutions assist in maintaining user access rights guaranteeing only designated personnel can access sensitive data. Finally, AI-powered advanced threat detection tools can detect anomalies in behavior that allows organizations to respond quickly and efficiently when a potential threat arises.
In this competitive scenario customer trust is the top priority. One data breach can tarnish a brand in such a way that customers will avoid taking their business anywhere, leaving the company with little to no revenue. Organisations that prioritize databreach protection do not just comply with regulations but also improve their credibility and brand loyalty among customers. With the secure cloud environment they can make clients feel that their data is protected and build up long-term relationships.
| Strategy | Description | Benefits |
|
Encryption |
Scrambles data to protect it from unauthorized access |
Ensures confidentiality of data |
|
Identity and Access Management (IAM) |
Controls user access to sensitive information |
Reduces insider threats |
|
Threat Detection |
Monitors for unusual activity and potential breaches |
Enables rapid response to threats |
|
Incident Response |
Plans and procedures to address security incidents |
Minimizes damage from breaches |
Restraints
-
Navigating various regulations and compliance requirements can be challenging and resource-intensive for businesses.
-
Difficulty in integrating cloud security solutions with existing IT infrastructure can hinder deployment and effectiveness.
-
A lack of skilled cybersecurity professionals can limit the ability of organizations to effectively implement and manage cloud security measures.
However, the shortage of skilled cybersecurity professionals is posing a significant challenge in the cloud security market. With organizations moving to the cloud at an increasing rate, the need for cloud security skills has grown. The issue has arisen due to the pace of modernization with cloud application and solutions leaving the supply chain of qualified personnel lagging behind creating a talent shortage needed for effective market cloud security solution management.
There is a dire shortage of professionals who have the skills or knowledge to understand these complexities and address cloud security in an organization. The lack of qualified personnel results in weak security, exposing systems to breaches and cyberattacks. The lack of experienced personnel can deter organizations from implementing security best practices, performing regular audits, and responding timely to security incidents.
The dearth of skilled cybersecurity professionals impacting the entire ecosystem not only on implementation of security solutions in cloud but also impacting strategic planning and management competency around security hygiene. Businesses will need to turn to a third-party service provider or consultant, which can be expensive and may not represent the exact security requirements of the organization.
| Aspect | Impact of Skill Shortage |
|
Incident Response |
Delayed response to security breaches, increasing damage. |
|
Security Posture |
Weaker security measures leading to higher vulnerability. |
|
Compliance Management |
Difficulty in maintaining compliance with regulations. |
|
Cost Implications |
Increased reliance on external consultants raises costs. |
|
Employee Morale |
Overburdened existing staff leading to burnout and turnover. |
|
Innovation Stagnation |
Limited capacity to explore advanced security technologies. |
Cloud Security Market Segment Analysis
By Component
The solution segment dominated the market and represented highest revenue share in 2023, more than of 68.4%. With the changing digital environment, hackers are developing more advanced and aggressive attack methods. Hence, organisations need to prepare for a holistic cloud security offering with multiple layers of defence against threats. These solutions encompass a diverse range of tools and technologies, including but not limited to encryption, identity and access management, data loss prevention, threat intelligence, endpoint protection and security analytics. The solution segment simplifies and provides unified frameworks that mitigate complexity enabling integration with diverse IT infrastructures.
On the other hand, the services segment is expected to grow at a CAGR of 14.5% during the projected period. With the increasing number of cyber threats, enterprises are now aware that stringent security protocols must be in place. Cloud security services offer proactive threats against its vast range of cyber attacks specifically in the areas of threat intelligence, detection, and incident response. The growth of the services segment in the future will depend on its ability to be merged along with emerging technologies into a cloud security infrastructure. Such services leverage AI, behavior analytics, predictive analytics, and other innovations that analyze patterns with automation for fast incident response.
By Deployment
The private segment dominated the market and represented over 47.3% of the market share in 2023, It is primarily fueled by enterprises where those applications and workloads deemed mission-critical tend to require high availability and low latency. Access to private clouds is considered a key aspect of digital transformation strategies for many enterprises. Enterprise businesses can benefit from the advantages of cloud computing without sacrificing a great deal of control by transitioning from traditional on-premises infrastructure managed environments to private cloud-based ones. In the upcoming years, we will see collaborative security ecosystems to come into play where the different security technology and platform work together seamlessly sharing threat information.
However, the hybrid segment is likely to witness robust growth, registering a CAGR over 13.8% during the forecast period. This expansion has been driven by organizations that have begun to realize the value of strategic data management. With hybrid cloud solutions, organisations can place data wherever it makes the most economic sense based on performance, compliance and cost factors. A hybrid cloud model empowers enterprises to expand their global footprint without sacrificing either performance or reliability.
By End-Use
The IT & telecom segment dominated the market and held a market share of 16.8% in 2023. This growth stems from the sector being immersed in an ever more complex and dynamic IT environment comprising a multitude of software, networks and devices. Security solutions in the cloud are inevitable that offer how flexible and adaptive security solutions become better when faced with the fast-changing IT landscape while ensuring compliance to strict security policies. Apart from that, growth in the use of IoT devices and 5G technology implementations will expose new security risks in IT and telecom. This, in turn, will demand new cloud security measures to protect everything from varied connected devices and sensitive data associated with them to the integrity of whole IoT networks.
Meanwhile, the healthcare segment is expected to expand at a swift 15.8% CAGR during forecast period. The share of telehealth services will greatly impact the future healthcare trends in the market. As telehealth continues to be a permanent part of healthcare delivery, cloud security solutions will be essential to secure remote patient consultations. Finally, the increasing emergence of medical devices connected through the Internet of Medical Things (IoMT) adds additional layers of security risk. As a result, when it comes to the insecure nature of much of the cloud, cloud security solutions will have to evolve to protect everything from health monitors and health trackers that patients carry around with them or implant sensors, all while securing patient-generated data in many different forms.
Regional Analysis
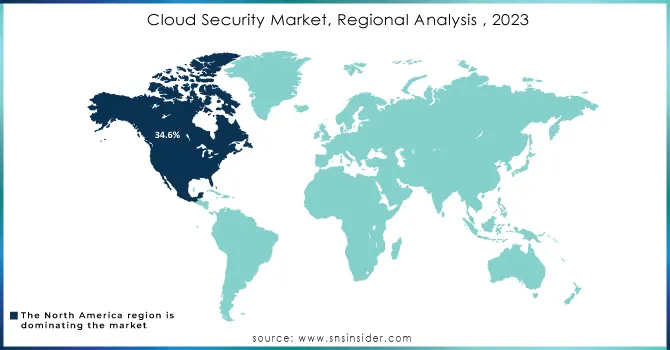
North America dominated the market and represented over largest revenue share of 34.6% share, Growing awareness of cybersecurity threats in the region has led to organizations become increasingly proactive toward implementing robust security measures. In particular, the USA not only has great economic power but is also among the world leaders in science and technology (and entrepreneurship), banking, medicine/healthcare. As the need to safeguard important assets and stand firm with cyber hygiene has become more acute, cloud security solutions have gained unprecedented relevance. This is due to the fact that North America has an innovation and risk taking friendly culture, making it a great place for companies to adopt advanced cloud security.
On the other hand, the Asia Pacific (APAC) region is expected to grow at the highest CAGR of 15.3%. This growth is mainly due to the fact that there has always been a sizeable volume of cross-border activity undertaken by enterprises. Cloud security services provide a complete and modular solution for security irrespective of geographical regions, helping an organization to navigate these complexities.
Do You Need any Customization Research on Cloud Security Market - Enquire Now
Key players
The major key players with their services
-
Amazon Web Services (AWS) - AWS Shield
-
Microsoft - Microsoft Defender for Cloud
-
Google Cloud Platform - Google Cloud Armor
-
IBM - IBM Cloud Security
-
Palo Alto Networks - Prisma Cloud
-
Cisco - Cisco Cloudlock
-
Check Point Software Technologies - CloudGuard
-
Fortinet - FortiGate Cloud
-
McAfee - McAfee MVISION Cloud
-
NortonLifeLock - Norton Cloud Backup
-
Zscaler - Zscaler Internet Access
-
CrowdStrike - CrowdStrike Falcon
-
Cloudflare - Cloudflare Security Solutions
-
Splunk - Splunk Cloud
-
Proofpoint - Proofpoint Email Protection
-
Trend Micro - Trend Micro Cloud One
-
SonicWall - SonicWall Cloud App Security
-
CyberArk - CyberArk Cloud Entitlement Manager
-
Barracuda Networks - Barracuda Cloud Security Guardian
-
Qualys - Qualys Cloud Platform
B2B User
-
Netflix
-
Adobe
-
Spotify
-
American Express
-
Goldman Sachs
-
Bank of America
-
Nasdaq
-
Siemens
-
Toyota
-
GoDaddy
-
Lyft
-
Rakuten
-
Udemy
-
Sony
-
FIS
-
Panasonic
-
RIT (Rochester Institute of Technology)
-
The Home Depot
-
Ticketmaster
-
Vodafone
Recent Developments
February 2024 – Check Point Software Technologies launched the Infinity AI Copilot platform, an innovative solution aimed at improving the efficiency of cloud technologies for IT teams through the application of AI.
October 2023 – Palo Alto Networks revealed its acquisition of Dig Security, a startup specializing in cloud data security, for USD 400 million. This move is intended to incorporate Dig’s data security posture management (DSPM) technology into the Prisma Cloud platform.
| Report Attributes | Details |
| Market Size in 2023 | USD 36.9 billion |
| Market Size by 2032 | USD 112.4 Billion |
| CAGR | CAGR of 13.20% from 2024-2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Component (Solution, Services) • By Deployment (Private, Hybrid, Public) • By Organization Size (Large Enterprises, Small & Medium Enterprises) • By End - Use (BFSI, Retail & E-commerce, IT & Telecom, Healthcare, Manufacturing, Government, Aerospace & Defense, Energy & Utilities, Transportation & Logistics, Others) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia Rest of Latin America) |
| Company Profiles |
Amazon Web Services (AWS), Microsoft, Google Cloud Platform, IBM, Palo Alto Networks, Cisco, Check Point Software Technologies, Fortinet McAfee, NortonLifeLock |
| Key Drivers |
•Growing incidences of data breaches and ransomware attacks are pushing organizations to enhance their cloud security measures |
| Market Restraints | •Navigating various regulations and compliance requirements can be challenging and resource-intensive for businesses •Difficulty in integrating cloud security solutions with existing IT infrastructure can hinder deployment and effectiveness •A lack of skilled cybersecurity professionals can limit the ability of organizations to effectively implement and manage cloud security measures. |

