Cybersecurity In Critical Infrastructure Market Report Scope & Overview:
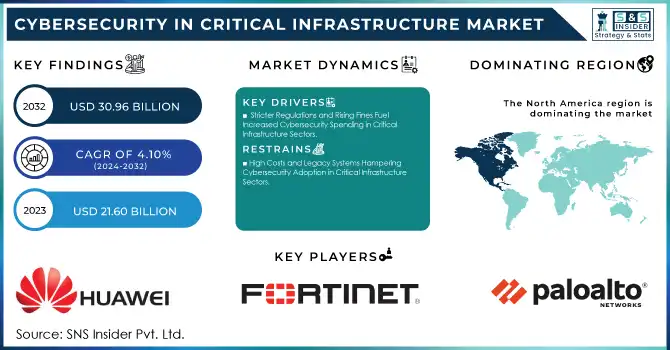
The Cybersecurity in Critical Infrastructure Market was valued at USD 21.60 billion in 2023 and is expected to reach USD 30.96 Billion by 2032, growing at a CAGR of 4.10 % over the forecast period 2024-2032.
To get more information on Cybersecurity in Critical Infrastructure Market - Request Free Sample Report
The growth of Cybersecurity in the Critical Infrastructure Market is largely due to the rising occurrence of sophisticated cyber threats on critical infrastructure such as energy, transportation, telecommunications, and government. In an age where industries and organizations are more interconnected than ever, the vulnerabilities within critical infrastructure systems have widened making them ideal targets for cyber threats. This has led to an increased need for strong cybersecurity systems to protect the most vital assets from bad actors, including data loss, ransomware, and advanced persistent threats (APTs). In addition, states or countries are investing heavily in cybersecurity, combining these elements with an increase in state-sponsored cyber warfare and hacking groups, to protect their national security interests. In 2024, more than 420 million cyberattacks were detected on critical infrastructure, an average of 13 attacks per second, recorded in a year, found within the services of more than 80 countries. Ransomware incidents were reported by 24% of organizations, compared to 20% in previous years. Also, cyber activities by states, such as Chinese hackers targeting U.S. critical infrastructure, have increased, indicating an increased national security threat and an organic threat to critical systems.
The adoption of more disruptive technologies including IoT, AI, and cloud in critical infrastructure where solutions are designed to not only make operations more efficient but also generate new security risks is another large driver of growth. With the increasing demand for real-time threat intelligence, advanced threat detection, and automated incident response, organizations are adopting advanced cybersecurity tools such as encryption, network access control, and firewalls. In addition, regulations and compliance have an influence on the market, as organizations are being forced to implement cybersecurity through their infrastructure. Together, with the growing threat landscape, advances in technology, and changes in regulatory environments, these drivers keep subjects of the cybersecurity market in critical infrastructure on the rise. Human error was responsible for 88% of breaches against cybersecurity in 2024. Through August, there has been an almost 70 percent increase in cyberattacks on U.S. utilities, with an average of 1,162 attacks per month. Data breach average cost reached a record high of USD 4.88 million.
Cybersecurity in Critical Infrastructure Market Dynamics
KEY DRIVERS:
-
Stricter Regulations and Rising Fines Fuel Increased Cybersecurity Spending in Critical Infrastructure Sectors
The increasing regulatory pressure and compliance on the Cybersecurity in Critical Infrastructure Market is one of the major driving forces in the market. In many countries around the globe, regulations to protect critical infrastructure from cyber threats are becoming stricter. Take, for example, some regulations such as the NIST Cybersecurity Framework in the US as well as the EU's Network and Information Systems (NIS) Directive that mandate stricter cybersecurity measures on organizations. They require certain levels of security, audits, and reporting, driving industries like energy, banking, healthcare, and transportation to pour vast amounts of money into cybersecurity solutions. Failure to comply with these regulations can lead to heavy fines, damage to reputation, and interruptions to operations, significantly increasing the demand for reliable cybersecurity frameworks. With the tightening regulatory landscape, organizations have realized the need for deploying these advanced security solutions to help them stay compliant and steer clear of financial and legal consequences related to breaches. The overall global non-compliance fines for cybersecurity regulations were USD 800 million in 2024 with 25 EU member states adopting the NIS2 Directive. The NIST Cybersecurity Framework was adopted by around 40% of critical infrastructure organizations in the U.S., and 75% of regulated organizations were required to go through mandatory cybersecurity audits. Bottom line USD 20 billion for cybersecurity spending in energy, healthcare, banking, and transportation; USD 3 billion in penalties for critical infrastructure breaches.
-
Rising Digital Transformation and Cyberattacks Drive Demand for Advanced Cybersecurity in Critical Infrastructure
The other major factor is the increasing dependence on digital transformation in the core industries. As the Internet of Things, cloud computing, and smart grids technology continues to take hold at breakneck speed, some of our most critical infrastructure sectors are now both interconnected as well as interdependent, relying on digital systems to perform essential functions. Though these technologies can provide operational efficiency and cost savings, they also equip enterprises with new vulnerabilities. Merging old systems with the newest tech can result in vulnerabilities that cybercriminals can exploit. Across sectors in energy, utilities, and transportation, for example, the movement towards more digital transformation and the increasing complexity of cyberattacks has brought cybersecurity to the forefront of organizational needs. With critical infrastructure on the rise as a digital asset, the industry will call for real-time monitoring, threat intelligence, and specialized cybersecurity measures to protect sensitive information and maintain the smooth operation of essential services. Increased reliance on digital transformation further drives demand in the market for cybersecurity solutions that use advanced technology. Cyberattacks on critical infrastructure rose by 45% in 2024, with the energy, utilities, and transportation sectors in particular being persistent targets. 100% of energy and utility companies started their digital transformation journey, but only 20% had finished it. Fierce Wireless reported more than 30% of IoT devices in critical infrastructure had vulnerabilities, and USD 7 billion dollars spent on cybersecurity solutions across the critical infrastructure segments. Over the course of the year, 60% of energy and utility companies implemented real-time monitoring and threat intelligence solutions.
RESTRAIN:
-
High Costs and Legacy Systems Hampering Cybersecurity Adoption in Critical Infrastructure Sectors
A major factor hindering the Cybersecurity in Critical Infrastructure Market is the huge cost associated with cybersecurity solutions and its implementation. Given that effective cybersecurity requires special hardware, software, and personnel, these tools can be costly, especially to resource-challenged governments, corporations, and other institutions. As a result, many lack the necessary resources for recommended cybersecurity infrastructure, exposing them to a heightened risk of compromise. There are so many critical infrastructure sectors that are dependent on legacy systems that are not capable of addressing current cybersecurity threats. This makes it extremely challenging and tedious to bring new cyber tech into these legacy systems without bringing down the house. Furthermore, the lack of qualified professionals in the field creates an impediment, and organizations are having a hard time ensuring that they have the needed manpower to manage and protect their infrastructure which is becoming increasingly vulnerable to threatening cyber activities.
Cybersecurity in Critical Infrastructure Market Segment Analysis
BY TYPE
The Cybersecurity in Critical Infrastructure Market is dominated by Encryption with a share of 34.7% in 2023, due to its increasing necessity in data protection across critical sectors. Encryption is one of the most common security measures to protect sensitive data against unauthorized access, particularly in the finance, government, healthcare, and energy sectors, and security breaches can result in dire implications. Cyberattacks keep mutating and growing in sophistication, driving the demand for encryption of data while in motion as well as when it is stored. Additionally, encryption continues to be the primary line of defense as the variety and volume of sensitive data continues to grow both in data generation and when transmitted, also contributing to its market dominance in 2023.
Threat Intelligence will grow the fastest in terms of CAGR from 2024-2032 because of the increasing sophistication and volume of cyberattacks against critical infrastructure. With adversaries adopting extremely sophisticated methods, organizations will want sudden and contextual recognition to be able to see an attack, prevent it, and respond to it. Threat intelligence solutions offer insights into new threats, exploits, and methodologies that empower your organization to proactively plan. As AI and machine learning are increasingly used to predict and rapidly respond to threats, threat intelligence solutions will see significant growth soon. In addition, advanced threat intelligence is necessary to protect the infrastructure of industries commonly attacked by state-sponsored and criminal cyber actors including energy, telecommunications, and transportation and this will further stimulate the growth of this market in the coming years.
BY APPLICATION
The Government and defense sector dominated the market with 32.4% of the total market share in 2023. Cyber espionage, state-sponsored threats, hacking targeting operations, and stealing information against government and defense agencies are among the prime targets. That is why these industries invest so heavily in high-level cybersecurity to secure military systems, intelligence data, critical national infrastructure, and communication networks. An increasing number of cyberattacks along with various geopolitical tensions across the globe has resulted in governments prioritizing cyber security which in turn helps them in maintaining a huge market share.
The Banking, Financial Services, and Insurance (BFSI) sector is anticipated to hold the highest CAGR (2024-2032) with the surge in financial transaction volume, the increase in digitization of financial services, and the growing threat of financial cybercrime. Due to its nature of dealing with extremely sensitive customer information such as personal identification information and financial assets, the BFSI sector is one of the main targets of cybercriminals. As online banking, mobile payment systems, and digital currencies gain ground, the demand for well-designed cybersecurity solutions that eliminate data breaches, fraud, and financial theft is crucial. Moreover, rising regulatory pressure such as the General Data Protection Regulation (GDPR) & Payment Card Industry Data Security Standard (PCI DSS) is also creating a demand for better security products and services within the BFSI sector owing to which, it is growing rapidly in the cybersecurity market.
REGIONAL ANALYSIS
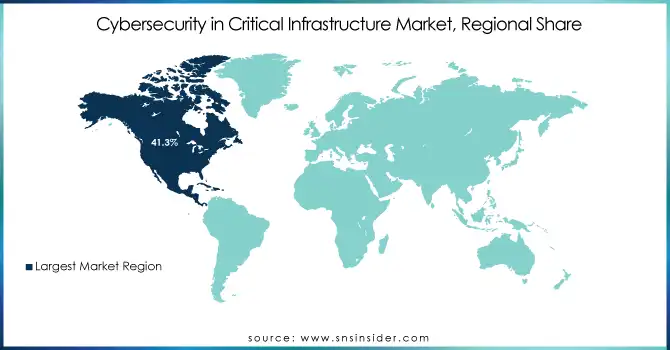
North America held a market share of 41.3% in 2023 for Cybersecurity in the Critical Infrastructure Market owing to a developed IT environment, high business investment in digital technologies, strong implementation of critical infrastructure in the region, and investment in cyber security solutions. Many high-importance sectors located there such as energy, defense, telco, and BFSI are under frequent cyberattacks. Regionally important cybersecurity vendors Palo Alto Networks, Cisco, and Fortinet also cement leadership in North America. Such as the Colonial Pipeline ransomware attack in 2021 which illustrated flaws in the critical infrastructure sectors and resulted in billions of dollars being invested in expanding cybersecurity to protect energy pipelines and other critical systems in the U.S. and Canada.
Asia Pacific is anticipated to register the highest growth (CAGR from 2024 to 2032) owing to the high rate of digital transformation and urbanization in the region along with rising adoption of IoT and smart infrastructure across the spheres. China, India, Japan, and South Korea are just a handful of the countries in this region that are witnessing a massive uptick in cyberattacks on their critical infrastructure areas such as energy grids, transportation networks, and financial services. A case in point, India’s power grid was targeted in the year 2020, reportedly attributed to state-backed professional threats, snowballing the demand for sophisticated cybersecurity in the region. Furthermore, various government initiatives like India National Cyber Security Strategy 2021, & China Cybersecurity Law are prompting investment in cybersecurity tools that support the market growth. Asia Pacific is the next big thing for cyber security innovations and adoption driven by an increasing threat landscape and favorable regulations.
Get Customized Report as per Your Business Requirement - Enquiry Now
Key players
Some of the major players in the Cybersecurity in Critical Infrastructure Market are:
-
Palo Alto Networks (Next-Generation Firewall, Prisma Cloud)
-
Fortinet (FortiGate Firewall, FortiSIEM)
-
Cisco Systems, Inc. (Cisco Firepower, Cisco Umbrella)
-
Check Point Software Technologies Ltd. (Check Point Quantum Security Gateway, Check Point CloudGuard)
-
IBM Corporation (IBM QRadar, IBM Guardium)
-
Trend Micro, Inc. (Trend Micro Deep Security, Trend Micro Apex One)
-
Huawei (Huawei USG Series Firewalls, Huawei AntiDDoS)
-
Norton LifeLock (Norton 360, Norton Secure VPN)
-
RSA Security LLC (RSA NetWitness Platform, RSA SecurID)
-
FireEye, Inc. (FireEye Network Security, FireEye Endpoint Security)
-
BAE Systems (BAE Systems Cyber Threat Detection, BAE Systems Data Protection Solutions)
-
General Dynamics Corporation (GD Mission Systems Cyber Defense Solutions, TACLANE Encryptors)
-
McAfee, Inc. (McAfee Total Protection, McAfee MVISION Endpoint)
-
Honeywell International Inc. (Honeywell Industrial Cybersecurity Solutions, Honeywell Secure Media Exchange)
-
Thales Group (Thales CipherTrust Data Security Platform, Thales SafeNet Trusted Access)
-
Airbus SE (Airbus CyberSecurity Keelback Net, Airbus CyberRange)
-
Sophos (Sophos Intercept X, Sophos XG Firewall)
-
CrowdStrike (CrowdStrike Falcon Platform, CrowdStrike Threat Graph)
-
CyberArk (CyberArk Privileged Access Manager, CyberArk Endpoint Privilege Manager)
-
Akamai Technologies (Akamai Kona Site Defender, Akamai Prolexic Routed)
Some of the Raw Material Suppliers for Cybersecurity in Critical Infrastructure companies:
-
Intel Corporation
-
Advanced Micro Devices (AMD)
-
Micron Technology
-
Seagate Technology
-
Western Digital
-
Foxconn Technology Group
-
Qualcomm
-
Broadcom Inc.
-
Samsung Electronics
-
Taiwan Semiconductor Manufacturing Company (TSMC)
RECENT TRENDS
-
In October 2024, Palo Alto Networks launched new OT security solutions, including guided virtual patching, ruggedized firewalls, and secure remote access tools, to combat growing cyber threats in industrial operations.
-
In August 2024, IBM launched a generative AI-powered Cybersecurity Assistant for its Threat Detection and Response Services, leveraging the Watsonx platform to enhance threat investigation and response.
-
In October 2024, RSA and Swissbit partnered to launch the RSA iShield Key 2 series, next-gen hardware authenticators with FIPS 140-3 certification, to enhance cybersecurity for government agencies. The devices aim to meet federal mandates and support phishing-resistant MFA and Zero Trust Architecture.
| Report Attributes | Details |
|---|---|
| Market Size in 2023 | USD 21.60 Billion |
| Market Size by 2032 | USD 30.96 Billion |
| CAGR | CAGR of 4.10% From 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Type (Encryption, Network Access Control & Firewalls, Threat Intelligence, Other) • By Application (BFSI, Government and Defense, Transport & Logistics, Energy & Power, Commercial Sector, Telecommunications) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles | Palo Alto Networks, Fortinet, Cisco Systems, Inc., Check Point Software Technologies Ltd., IBM Corporation, Trend Micro, Inc., Huawei, NortonLifeLock, RSA Security LLC, FireEye, Inc., BAE Systems, General Dynamics Corporation, McAfee, Inc., Honeywell International Inc., Thales Group, Airbus SE, Sophos, CrowdStrike, CyberArk, Akamai Technologies. |
| Key Drivers | • Stricter Regulations and Rising Fines Fuel Increased Cybersecurity Spending in Critical Infrastructure Sectors • Rising Digital Transformation and Cyberattacks Drive Demand for Advanced Cybersecurity in Critical Infrastructure |
| RESTRAINTS | • High Costs and Legacy Systems Hampering Cybersecurity Adoption in Critical Infrastructure Sectors |

