FIDO Authentication Market Report Scope & Overview:
Get more information on FIDO Authentication Market - Request Sample Report
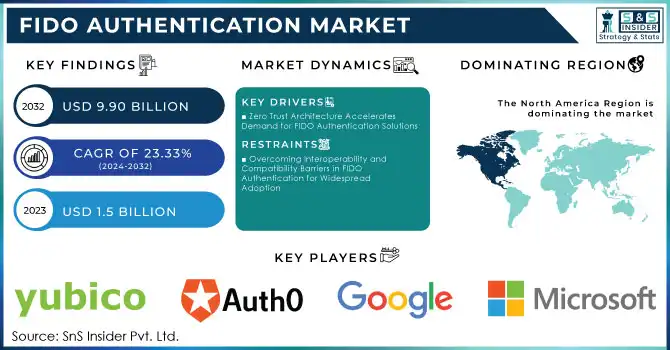
The FIDO Authentication Market Size was USD 1.5 billion in 2023 and is expected to Reach USD 9.90 billion by 2032 and grow at a CAGR of 23.33% over the forecast period of 2024-2032.
The FIDO authentication market is witnessing significant growth due to escalating cybersecurity threats, including phishing, data breaches, and identity theft, compounded by the increasing sophistication of AI-driven cyberattacks. As businesses and consumers seek secure, passwordless authentication solutions to mitigate the vulnerabilities of traditional password systems, FIDO, particularly the FIDO2 standard, is gaining momentum. FIDO offers robust encryption, phishing-resistant features, and seamless user experiences, making it a preferred choice for organizations shifting toward Zero Trust Architecture (ZTA). According to the FIDO Alliance’s 2023 Online Authentication Barometer, over 50% of users are increasingly aware of the security risks associated with password-only systems, with AI-driven tools like FraudGPT amplifying these threats. While passwords remain dominant, with consumers manually entering them approximately 1,280 times annually, there is a notable shift towards biometrics, with 33% of financial services consumers opting for biometrics over passwords.
This preference for biometric authentication has grown by 5% compared to the previous year. Despite this shift, traditional password usage is still prevalent across various sectors, with 37% of consumers using passwords for work accounts and 25% for streaming services. However, poor authentication experiences are leading to frustration, with 59% of consumers abandoning online services and 43% canceling purchases in the past 60 days. Additionally, 70% of people have had to reset passwords in the last two months, underscoring the inconvenience of password dependence. As awareness of alternatives like passkeys grows, rising from 39% in 2022 to 52% in 2023, FIDO adoption is also expanding in key sectors such as finance, healthcare, and telecommunications. The market is expected to continue growing as companies prioritize stronger, passwordless authentication to secure sensitive data in response to the evolving landscape of digital security.
FIDO Authentication Market Dynamics
Drivers
-
Zero Trust Architecture Accelerates Demand for FIDO Authentication Solutions
The adoption of Zero Trust Architecture (ZTA) is emerging as a significant driver for the FIDO authentication market. ZTA’s "never trust, always verify" principle ensures continuous authentication and validation of users, devices, and applications, addressing vulnerabilities in traditional perimeter-based security models. U.S. federal agencies, guided by initiatives like Executive Order 14028 and OMB M-22-09, are leading the transition toward ZTA, which emphasizes robust Identity Credential and Access Management (ICAM) practices. These practices include continuous monitoring, role-based access controls, and adaptive authentication, all aligned with the strong cryptographic standards of FIDO protocols. The Federal Zero Trust Data Security Guide highlights the importance of FIDO’s passwordless solutions in mitigating risks like phishing and deepfakes, which are increasingly sophisticated due to synthetic identities. Efforts by agencies such as the Department of Defense to incorporate FIDO-enabled identity verification and secure data tagging underline its value in tactical cybersecurity. With the rise in cyberattacks and costly breaches, organizations across sectors—including enterprise and government-are prioritizing ZTA. This directly correlates with the growth of the FIDO authentication market, as FIDO’s technologies are integral to ZTA’s security frameworks.
Restraints
-
Overcoming Interoperability and Compatibility Barriers in FIDO Authentication for Widespread Adoption
Interoperability and compatibility challenges are significant constraints in the FIDO authentication market, hindering its broader adoption. Many organizations struggle to integrate FIDO standards with their existing legacy systems, platforms, and outdated infrastructures. One of the primary obstacles is the incompatibility of older hardware and software with newer FIDO protocols, such as FIDO2, WebAuthn, and CTAP. These challenges often require costly upgrades or replacements of security hardware like biometric readers, security keys, and compatible devices, which can be unaffordable for small and medium-sized enterprises (SMEs). The lack of standardized implementation practices further exacerbates the issue, as organizations often must invest in custom solutions to integrate FIDO with their existing workflows. FIDO's promise of enhanced security features like attestation is often limited by compatibility issues with e-commerce platforms and mobile operating systems that are not designed to support modern passwordless technologies. Integrating FIDO2 with existing web payment systems, which need to comply with WebAuthn and EMVCo standards, complicates deployment even further. The lack of interoperability solutions and fragmented ecosystems prevent global scalability and widespread adoption of FIDO technologies. To address these barriers, there is a need for greater cross-industry collaboration to improve compatibility and reduce the costs of integration. Overcoming these challenges is essential for unlocking the full potential of passwordless authentication and driving the future growth of the FIDO authentication market.
FIDO Authentication Market Segment Analysis
By Component
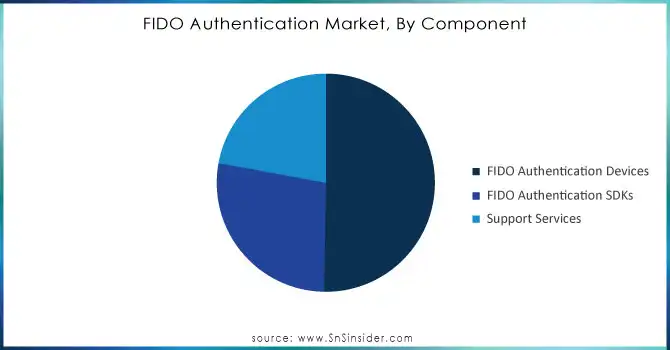
In 2023, the FIDO Authentication Devices segment dominated the FIDO authentication market, capturing around 51% of the revenue share. This growth is driven by the increasing demand for hardware-based security solutions across sectors like banking, healthcare, government, and enterprise IT. FIDO devices, including biometric readers, hardware tokens, and USB security keys, offer superior protection against cybersecurity threats like data breaches and identity theft. The rise of biometric technologies and regulatory compliance requirements, such as GDPR and PSD2, further bolster adoption. Additionally, the seamless user experience provided by FIDO devices, coupled with widespread support from tech giants like Google and Microsoft, ensures this segment's continued dominance and growth through 2032.
Need any customization research on FIDO Authentication Market - Enquire Now
By Application
In 2023, the Payment Processing application segment led the FIDO authentication market, accounting for approximately 55% of the revenue share. This dominance is driven by the rising demand for secure, user-friendly authentication in the expanding digital payment sector. As e-commerce, mobile banking, and digital wallets grow, securing transactions becomes essential. FIDO's password-less, multi-factor authentication provides robust security, reducing fraud and boosting consumer trust. Regulatory requirements like the EU’s PSD2 further promote FIDO's adoption, ensuring compliance with strong customer authentication standards. The rise of contactless and mobile payments, alongside the growing popularity of biometrics, has enhanced user experience and security. FIDO’s integration with platforms like Apple Pay and Google Pay has solidified its position in the payment ecosystem, ensuring continued growth.
FIDO Authentication Market Regional Overview
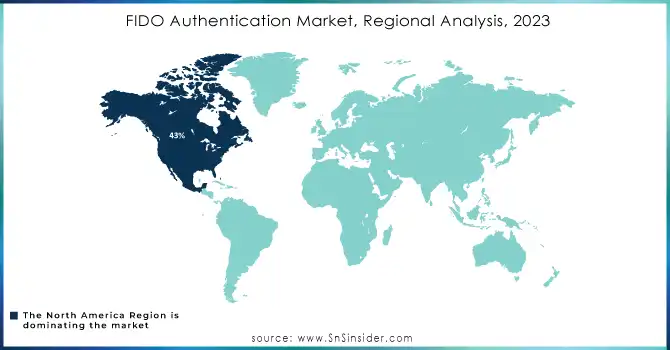
In 2023, North America led the FIDO authentication market with a 43% revenue share, driven by its strong adoption of advanced cybersecurity technologies and a growing demand for secure solutions in sectors like finance, healthcare, government, and enterprise IT. The U.S. plays a key role, with a tech-savvy population, high mobile usage, and widespread e-commerce. Rising cyber threats, including data breaches and fraud, have increased the need for secure authentication, and FIDO’s password-less, multi-factor approach aligns with the region's focus on data privacy. North America's favorable regulations, such as GDPR and PIPEDA, along with major tech companies like Google, Microsoft, and Apple, have further accelerated FIDO adoption, particularly in finance, mobile payments, and cloud services.
In 2023, Asia-Pacific became the fastest-growing region in the FIDO authentication market, driven by rapid digital transformation, rising internet penetration, and increasing cybersecurity focus across markets like China, India, Japan, and Southeast Asia. The region's expanding e-commerce, mobile payments, and banking sectors are fueling demand for secure, password-less authentication solutions. Governments in countries like Japan and South Korea are implementing stringent data protection regulations, boosting FIDO adoption. Additionally, the widespread use of smartphones and mobile payments in China and India has further accelerated biometric authentication. With ongoing digital investments, Asia-Pacific is expected to maintain strong growth in the FIDO Authentication market.
Key Players in FIDO Authentication Market
Some of the major key players in FIDO Authentication Market with product
-
Yubico (YubiKey)
-
Auth0 (Identity Platform)
-
Okta (Okta Adaptive Authentication)
-
Gemalto (Thales) (SafeNet Trusted Access)
-
Microsoft (Windows Hello)
-
Google (Google Authenticator)
-
Apple (Apple Face ID, Touch ID)
-
Mastercard (ID Check Mobile)
-
Amazon Web Services (AWS) (AWS Cognito)
-
Ping Identity (PingOne)
-
SecureAuth (SecureAuth Identity Platform)
-
Ubisoft (Ubisoft Connect Authentication)
-
Duo Security (Duo Push)
-
(RSA SecurID)
-
BioConnect (BioConnect Authentication Platform)
-
Vasco Data Security (Digipass for FIDO)
-
OneLogin (OneLogin Adaptive Authentication)
-
Trustonic (Trustonic Secure User Authentication)
-
Deep Identity (Deep Identity Authentication Services)
-
HID Global (HID Approve, FIDO2 Authentication)
List of Potential Customers in FIDO Authentication Market:
-
Bank of America
-
PayPal
-
Amazon
-
Google
-
Microsoft
-
Apple
-
Facebook (Meta)
-
Alibaba
-
IBM
-
Salesforce
-
Twitter
-
Uber
-
Netflix
-
Spotify
-
Intel
Recent Development
-
June 20, 2024, Yubico launches the Yubico Enrollment Suite for Microsoft users, designed to streamline the transition to passwordless, phishing-resistant authentication. The suite, including Yubico FIDO Pre-reg and YubiEnroll, integrates with Microsoft’s Entra ID to improve cyber resilience and support Zero Trust models by enabling multi-factor authentication.
-
Nov. 19, 2024, OneSpan integrates with Ping Identity to offer FIDO-enabled solutions for stronger, passwordless authentication. This collaboration eliminates the need for passwords and enhances security, with OneSpan now listed in Ping Identity’s Integration Directory, providing seamless solutions for enterprises focused on improving user experience while maintaining high security standards.
-
19 October 2024, RSA partners with Swissbit to launch the RSA iShield Key 2 series for enhanced security in the government and private sectors. Featuring FIDO2, PIV, HOTP support, and a FIPS 140-3 certified smart chip, the new hardware authenticator meets high-security standards and aligns with U.S. federal regulations, offering a robust solution for Zero Trust Architecture. The RSA iShield Key 2 series will be available by the end of 2024.
| Report Attributes | Details |
|---|---|
| Market Size in 2023 | USD 1.5 Billion |
| Market Size by 2032 | USD 9.90 Billion |
| CAGR | CAGR of 23.33% From 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Component(FIDO Authentication Devices, FIDO Authentication SDKs, Support Services), • By Application(Payment Processing, PKI / Credential Management, Database Encryption, Application Level Encryption, Others), • By Vertical(Banking & Financial Services, Government, Technology & Communication, Industrial & Manufacturing, Energy & Utility, Retail & Consumer Products, Healthcare & Lifesciences, Others) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe [Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles | Key players in the FIDO authentication market include Yubico, Auth0, Okta, Gemalto (Thales), Microsoft, Google, Apple, Mastercard, Amazon Web Services (AWS), Ping Identity, SecureAuth, Ubisoft, Duo Security, RSA Security, BioConnect, Vasco Data Security, OneLogin, Trustonic, Deep Identity, and HID Global. |
| Key Drivers | • Zero Trust Architecture Accelerates Demand for FIDO Authentication Solutions |
| Restraints | • Overcoming Interoperability and Compatibility Barriers in FIDO Authentication for Widespread Adoption |

