5G Security Market Report Scope & Overview:
Get more information on 5G Security Market - Request Free Sample Report
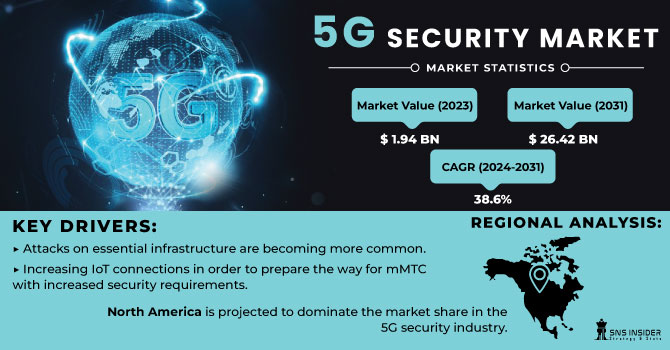
The 5G Security Market Size was valued at USD 2.11 Billion in 2023 and is expected to reach USD 44.94 Billion by 2032, growing at a CAGR of 40.49% over the forecast period 2024-2032.
The 5G security market is a cornerstone of the evolving global telecommunications landscape, driven by the widespread rollout and adoption of 5G networks worldwide. As of 2023, there are over 236 million global 5G subscriptions, with North America leading the charge, accounting for 32% of all wireless cellular connections and adding 22 million new 5G connections this year alone. Globally, 135 5G networks operate in compliance with 3rd Generation Partnership Project (3GPP) standards, enabling ultra-fast connectivity, low latency, and seamless device integration. This rapid growth opens doors for innovative applications across industries, from smart cities and autonomous vehicles to industrial automation and IoT ecosystems. However, the advancements also bring an increased risk of cyber threats, necessitating robust and scalable 5G security solutions.
The 5G security market is poised for significant growth, fueled by rising concerns over data breaches, regulatory mandates, and the urgent need for advanced frameworks to secure sensitive consumer and enterprise data. Leading telecom operators and infrastructure providers such as Ericsson, Nokia, and Huawei have integrated sophisticated security features into their 5G solutions. Simultaneously, cybersecurity leaders like Palo Alto Networks, Fortinet, and Cisco are innovating specialized tools designed to safeguard 5G infrastructure and connected devices. Regulatory bodies across the globe are enforcing stringent 5G security standards, further accelerating the adoption of advanced 5G cybersecurity technologies. With the rise of 5G adoption, the demand for 5G network security, IoT protection, and cloud-native security solutions is projected to surge, cementing the 5G security market as a critical enabler of secure, next-generation connectivity.
5G Security Market Dynamics:
Drivers
-
As 5G networks enable a wide range of innovations, the increase in cybersecurity threats has become a driving force for the 5G security market.
Cyber risks like DDoS attacks, data breaches, and APTs are a major threat to the security of networks, devices, and applications that depend on 5G connectivity. There are more opportunities for cybercriminals to take advantage of with the increasing number of connected devices, such as critical infrastructure, industrial systems, and personal devices. For example, the increased bandwidth from 5G networks allows for more data to be captured, emphasizing the importance of encryption protocols even further. Likewise, vulnerabilities in network slicing, which is utilized to divide 5G networks for various purposes, might allow attackers to infiltrate significant parts of the network, resulting in data exposure, service interruptions, and potential exploitation of confidential data. With the ongoing evolution of these threats, security solutions must also evolve to stop breaches. The growing number of complex cyber-attacks on 5G networks highlights the necessity for specialized security solutions that can effectively mitigate the risks, leading to an increased demand for advanced security technologies.
-
Public Safetys around the world recognize the strategic importance of securing 5G networks which drives the growth of the 5G security market.
As a result, many governments are investing heavily in the development of 5G security solutions and frameworks. In some countries, national security concerns regarding the use of foreign technologies in 5G infrastructure have led to regulations requiring heightened security standards. This has prompted both the private and public sectors to explore innovative security technologies that can protect the integrity of the network. For example, the U.S. and European Union have implemented initiatives to ensure that 5G networks are secure by promoting partnerships between telecommunications providers, cybersecurity firms, and government bodies to create a safe 5G ecosystem. These government-led initiatives and investments drive the demand for security solutions designed to safeguard the evolving 5G infrastructure. As national security concerns continue to shape policy and investment in 5G security, the 5G security market will continue to expand.
Restraints
-
A major limitation of the 5G security market is the absence of standardized security protocols and practices in various 5G networks.
The deployment of 5G technology is ongoing in different regions and countries, with each telecom operator having the flexibility to adopt their distinct strategy for 5G network structure and security protocols. The absence of standardization makes it harder to create and implement universal security solutions for all 5G networks. The lack of a worldwide security structure results in security providers having to customize their solutions for particular regional, network, or operator needs, leading to higher expenses and impeding the broad implementation of security measures. Moreover, the variation in the implementation of 5G networks can lead to security gaps due to certain areas lacking the necessary resources or regulations to properly handle 5G-related security threats. The lack of consistency in security implementation poses a major challenge until 5G networks are standardized.
5G Security Market Segmentation Analysis
By Offering
The solutions segment dominated the 5G security market in 2023, capturing 68% of the market share. These are pivotal in addressing the increased risks posed by 5G's hyper-connectivity and massive data flows. The high demand for comprehensive solutions is driven by organizations' need to safeguard critical infrastructures, manage cybersecurity risks, and comply with regulations like GDPR. For example, Palo Alto Networks provides 5G-ready firewall solutions to secure telecom infrastructures, while Ericsson offers 5G network slicing security.
The services segment is projected to become the fastest-growing segment in the 5G security market during 2024-2032, driven by the need for consultancy, integration, and managed services. As enterprises adopt 5G technology, they require expert guidance for deploying and maintaining robust security systems. Services include risk assessment, security implementation, and ongoing support to handle dynamic 5G threats. For instance, Accenture provides consultancy services for secure 5G implementations, while IBM offers managed services for 5G network security monitoring. Companies also rely on AT&T Cybersecurity for continuous security operations.
By Architecture
The 5G NR non-standalone architecture segment dominated the 5G security market in 2023, accounting for a 58% market share. NSA uses 4G as the control plane while leveraging 5G for enhanced data speeds and network capacity, making it an attractive option for telecom operators seeking cost-effective solutions for urban and suburban areas. Its reliance on existing infrastructure allows a gradual transition to 5G, reducing the need for complete overhauls. Companies such as AT&T utilize NSA to roll out 5G services quickly while ensuring compatibility with 4G networks, while Ericsson offers NSA solutions that enable seamless upgrades for service providers.
The 5G NR standalone architecture segment is projected to be the fastest-growing segment in the 5G security market, primarily because it fully harnesses the capabilities of 5G technology. These capabilities make SA ideal for advanced applications like industrial automation, autonomous vehicles, and smart city systems, which require real-time responsiveness and tailored network solutions. Companies like Huawei support SA networks with advanced security measures and scalable infrastructure for 5G-exclusive ecosystems, while Qualcomm provides the necessary hardware with chips designed for optimized 5G performance.
5G Security Market Regional Overview
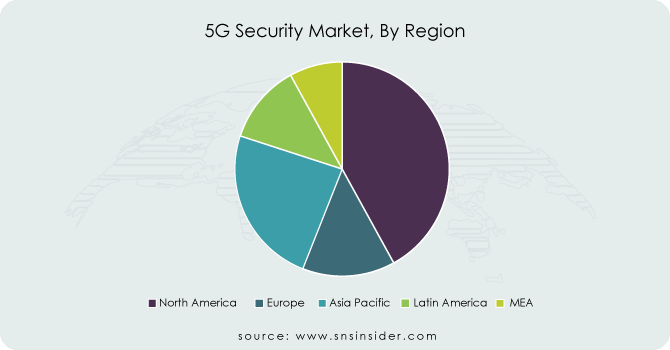
North America led the 5G security market in 2023 with a 32% market share, due to its advanced technological infrastructure and early adoption of 5G technology. The U.S. and Canada play pivotal roles, driven by strong investments in telecom infrastructure and cybersecurity. Public Safetys in this region have emphasized robust security frameworks for 5G deployments to mitigate risks like espionage and cyberattacks. For instance, Cisco offers solutions to protect 5G networks against DDoS attacks, and AT&T collaborates with enterprises to secure IoT devices over 5G. These factors have bolstered North America’s leadership in the market.
Asia-Pacific is anticipated to become the fastest-growing region with a rapid CAGR for 5G security market during 2024-2032, driven by widespread 5G deployments and surging demand for connected devices. Nations like China, South Korea, and Japan are heavily investing in 5G networks, with telecom giants like Huawei, ZTE, and Samsung leading the charge. The region’s diverse industrial landscape-spanning manufacturing, healthcare, and entertainment-requires robust security solutions to protect against advanced threats. Companies such as Huawei are integrating AI-powered security for 5G networks, while NTT Communications in Japan focuses on securing critical infrastructure against cyber threats.
Need any customization research on 5G Security Market - Enquiry Now
Key Players in 5G Security Market
The major key players in the 5G Security Market are:
-
Ericsson (Ericsson Security Manager, 5G Core Security Solutions)
-
Nokia (NetGuard Security Suite, Nokia Cloud Packet Core Security)
-
Huawei Technologies (5G Core Security Solutions, CloudFabric Security Solution)
-
Cisco Systems (Cisco Umbrella, Secure Firewall)
-
ZTE Corporation (5G Network Slicing Security, CloudStudio Security)
-
Palo Alto Networks (Prisma Access for 5G, Next-Generation Firewall)
-
Fortinet (FortiGate 5G Security Gateway, FortiAnalyzer)
-
Check Point Software Technologies (Quantum Security Gateway, CloudGuard for 5G)
-
Juniper Networks (SRX Series Firewalls, Contrail Networking)
-
Qualcomm (Snapdragon Secure Processing Unit, Wireless Edge Security)
-
Thales Group (5G SIM Security Solutions, CipherTrust Data Security Platform)
-
Radware (DefensePro, Cloud DDoS Protection for 5G)
-
A10 Networks (Thunder CFW, Thunder TPS for 5G)
-
NETSCOUT Systems (nGeniusONE, Arbor Edge Defense for 5G)
-
F5 Networks (BIG-IP Advanced Firewall Manager, NGINX App Protect for 5G)
-
Spirent Communications (Landslide Security Test Solution, 5G Core Test Automation)
-
Keysight Technologies (5G Security Test Solutions, Threat Simulator)
-
Trend Micro (Trend Micro Mobile Network Security, Trend Micro Deep Security)
-
IBM (QRadar SIEM, Cloud Pak for Security)
-
Samsung Electronics (5G Network Security Solutions, Knox Security Platform)
Recent Development
-
August 2024: Samsung, the biggest brand of consumer electronics in India, revealed the introduction of the Galaxy M35 5G in the country. The newest addition to Samsung's highly popular Galaxy M series aims to revolutionize the smartphone experience with a range of cutting-edge features.
-
February 2024: Palo Alto Networks introduced advanced 5G security and services for enterprises, working with Celona, Druid, Ataya, Netscout, Nvidia, and NTT Data.
-
September 2024: NTT DATA, a respected worldwide creator of business and technology services, together with IBM, revealed the introduction of SimpliZCloud, a completely managed cloud service developed on IBM LinuxONE.
| Report Attributes | Details |
|---|---|
| Market Size in 2023 | USD 2.11 Billion |
| Market Size by 2032 | USD 44.94 Billion |
| CAGR | CAGR of 40.49% From 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Offering (Solutions, Services) • By Architecture (5G NR Standalone, 5G NR Non-standalone) • By Network Security (RAN Security, Mobile Core Security) • By End User (Telecom Operators, Enterprises) • By Application (Virtual and Augmented Reality, Connected Automotive, Smart Manufacturing, Wireless eHealth, Smart Cities) • By Vertical (Manufacturing, Healthcare, Energy & Utilities, Retail, Automotive & Transportation, Public Safety, Media & Entertainment, Other) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles | Ericsson, Nokia, Huawei Technologies, Cisco Systems, ZTE Corporation, Palo Alto Networks, Fortinet, Check Point Software Technologies, Juniper Networks, Qualcomm, Thales Group, Radware, A10 Networks, NETSCOUT Systems, F5 Networks, Spirent Communications, Keysight Technologies, Trend Micro, IBM, Samsung Electronics |
| Key Drivers | • As 5G networks enable a wide range of innovations, the increase in cybersecurity threats has become a driving force for the 5G security market. • Governments around the world recognize the strategic importance of securing 5G networks which drives the growth of the 5G security market. |
| RESTRAINTS | • A major limitation of the 5G security market is the absence of standardized security protocols and practices in various 5G networks. |

