Data-Centric Security Market Key Insights:
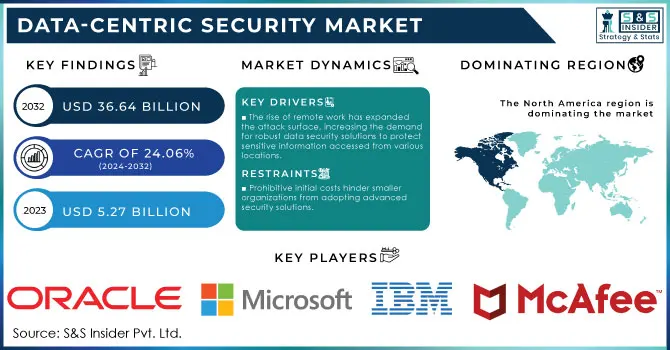
The Data-Centric Security Market size was valued at USD 5.27 billion in 2023 and is expected to reach USD 36.64 Billion by 2032, growing at a CAGR of 24.06% over the forecast period of 2024-2032. The Data-Centric Security Market is gaining recognition for its critical role in protecting sensitive information across multiple sectors. As organizations face an increase in cyber threats, there is a growing emphasis on data-centric security, which focuses on securing the data itself. A report from Cybersecurity Ventures anticipates that global cybercrime damages will surpass USD 10 trillion annually by 2025, underscoring the need for comprehensive security measures. Key growth drivers for this market include the necessity for regulatory compliance with laws like GDPR and HIPAA, along with the rising frequency of data breaches.
To Get More Information on Data-Centric Security Market - Request Sample Report
Recent incidents illustrate the urgency of this focus. In 2023, a significant data breach at a healthcare provider affected the personal information of over 3 million patients, highlighting the need for robust data-centric security strategies. The incorporation of cutting-edge technologies such as artificial intelligence (AI) and machine learning (ML) in security solutions enhances real-time threat detection and response capabilities. For instance, IBM has introduced AI-powered security systems that analyze data patterns to identify anomalies that could indicate potential breaches. These advancements not only strengthen security measures but also boost operational efficiency.
As the emphasis on data protection intensifies within organizational security frameworks, the demand for data-centric security solutions is expected to rise significantly. By 2024, investments in these technologies are projected to grow, reflecting a broader awareness of the essential nature of safeguarding sensitive data in an interconnected digital environment.
Market Dynamics
Drivers
-
The rise of remote work has expanded the attack surface, increasing the demand for robust data security solutions to protect sensitive information accessed from various locations.
-
Stringent data protection regulations, such as GDPR and HIPAA, compel organizations to adopt data-centric security solutions to avoid hefty fines and ensure compliance.
-
Companies are increasingly aware that robust data security measures are essential for maintaining customer trust and loyalty, leading to higher investments in data protection technologies.
In the Data-Centric Security Market, companies are increasingly aware that strong data security is vital for maintaining customer trust and loyalty. With the growing frequency of cyberattacks and data breaches, consumers are becoming more cautious about how their personal information is managed. According to reports, 43% of consumers are likely to stop doing business with a company after a data breach, highlighting the critical need for a robust security framework to maintain trust.
Consequently, organizations are making substantial investments in data protection technologies, recognizing that safeguarding sensitive data is crucial not only for regulatory compliance but also for enhancing customer loyalty and bolstering their brand reputation. Additionally, regulations such as GDPR and CCPA impose strict data protection standards, compelling companies to implement advanced security solutions to avoid significant fines and legal consequences. This regulatory environment has raised awareness about data security, prompting businesses to invest in technologies that not only secure data but also convey a commitment to consumer privacy.
The incorporation of advanced technologies like artificial intelligence (AI) and machine learning (ML) enables organizations to proactively identify and address threats, thereby strengthening their data security posture. AI-driven systems can analyze large datasets in real time to detect anomalies and swiftly respond to potential breaches, which enhances consumer confidence in how their data is handled.
The demand for effective data security in the Data-Centric Security Market is driven by consumer expectations, regulatory demands, and the financial implications of data breaches. As companies prioritize the protection of sensitive information, investments in data-centric security solutions are expected to grow, reflecting a broader trend toward ensuring customer trust in an increasingly interconnected digital landscape. For further insights, you can check reports from sources like Accenture and IBM.
Restraints
-
The initial costs associated with implementing advanced data-centric security solutions can be prohibitive for smaller organizations, hindering their ability to adopt necessary technologies
-
There is a shortage of skilled professionals in data security, making it difficult for organizations to find qualified personnel to implement and manage data-centric security measures effectively
-
The rapidly changing landscape of cyber threats can render existing security measures inadequate, necessitating continuous updates and improvements that may strain resources
The shifting landscape of cyber threats presents considerable challenges for the Data Centric Security Market. As cybercriminals adapt their strategies—utilizing techniques such as ransomware, phishing, and advanced persistent threats (APTs)—traditional security measures become less effective. This ongoing requirement for updates can significantly burden an organization’s resources, impacting both finances and operations. Companies often find themselves allocating substantial portions of their budgets to new security technologies, threat intelligence, and the recruitment of skilled personnel to address evolving threats. Integrating new security solutions with existing systems poses its own challenges, often requiring the expertise of qualified professionals for seamless implementation. However, a shortage of cybersecurity talent complicates this issue, as many organizations struggle to locate individuals capable of establishing and maintaining advanced security frameworks.
Moreover, managing security across various data environments—especially with the rise of cloud computing and IoT devices—demands a more dynamic approach to data security. Failing to keep up can heighten the risk of data breaches and lead to compliance violations, which can result in substantial fines under regulations like GDPR and HIPAA.
The rapidly changing nature of cyber threats compels organizations in the Data Centric Security Market to invest in continual updates and improvements to their security measures. Ignoring these necessary adaptations can lead to significant repercussions, including financial losses, damage to reputation, and regulatory penalties.
Segment Analysis
By Solution
In 2023, the software segment dominated the Market, commanding a notable 65.7% share. This surge in demand is primarily driven by the escalating frequency of cyberattacks and data breaches, particularly in essential sectors such as Banking, Financial Services, and Insurance (BFSI), IT & Telecom, and retail. High-profile security breaches have highlighted the urgent need for these industries to implement robust software solutions to protect sensitive data. Additionally, the increasing focus from governments on improving data privacy and ensuring adherence to regulatory standards across various regions further enhances the growth of this segment.
The services segment is anticipated to grow at the fastest compound annual growth rate (CAGR) of 25.7% throughout the forecast period. This significant growth is fueled by the rising demand for effective user access controls and the safeguarding of confidential and regulated information. Data-centric security services are pivotal for establishing a zero-trust framework, enabling organizations to protect critical datasets in real-time while enforcing a least-privilege access strategy across diverse storage environments.
By Deployment
In 2023, the on-premise segment dominated the market and represented a significant 49.8% share of the Data Centric Security Market. Organizations operating in highly regulated industries or those following stringent governance policies often opt for complete control over their data assets. On-premise data-centric security solutions allow these organizations to manage their data within their own physical infrastructure, ensuring full oversight of data storage, access, and security. This focus on autonomy and regulatory compliance is likely to sustain the demand for on-premise solutions throughout the forecast period.
The cloud segment is expected to grow at a compound annual growth rate (CAGR) of 27.3% during the same period. As more organizations shift their data storage to the cloud, there is an increasing need for robust security measures, driving demand for cloud-based data-centric security solutions. These offerings typically include strong access controls, data masking, and encryption techniques, which are crucial for safeguarding sensitive information. Moreover, the rising need for secure collaboration and data sharing within and between organizations in cloud environments has significantly contributed to the demand for cloud-based data-centric security services.
By Organization Size
In 2023, the large enterprise segment dominated the Data-Centric Security Market, accounting for over 54.9% of the overall market share. This leadership is primarily attributed to the rising incidence of cyberattacks aimed at large organizations, which typically have extensive data storage capabilities and resource access. The increasing sophistication of these cyber threats highlights the urgent need for advanced cybersecurity measures. Data-centric security solutions improve visibility within organizations, facilitating effective monitoring and enforcement of data protection policies, as well as enabling timely detection and response to security incidents.
The Small and Medium-sized Enterprises (SME) segment is expected to grow at a compound annual growth rate (CAGR) of 25.9% during the forecast period. This anticipated growth is driven by a growing awareness among SMEs of the critical importance of implementing strong cybersecurity measures in response to increasingly sophisticated threats. High-profile incidents such as phishing, ransomware attacks, and data breaches have reinforced the need for SMEs to protect their sensitive information and data assets, encouraging them to invest in data-centric security solutions.
Regional Analysis
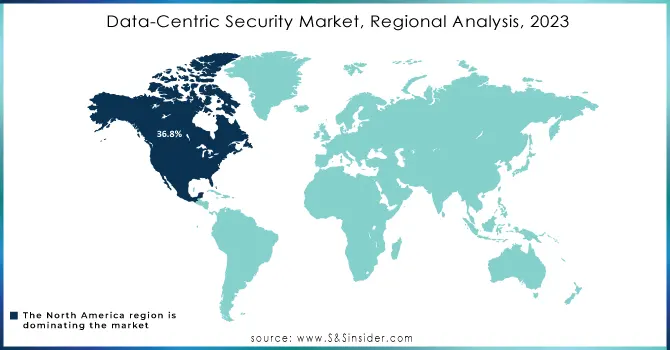
In 2023, North America emerged as the leader in the Data Centric Security Market, accounting for 36.8% of the market share. This dominant position is largely attributed to the increasing frequency of cyberattacks targeting government bodies, businesses, critical infrastructure, and the general populace, which has spurred a growing demand for robust data security solutions. The region's complex and evolving cyber threat landscape has emphasized the critical need for effective data-centric security measures. Furthermore, the presence of major companies such as Microsoft, IBM, and McAfee is expected to further drive market growth. Strict regulatory measures, including the California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR), have also heightened the demand for advanced cybersecurity solutions to mitigate potential legal and financial repercussions.
The Asia Pacific region is projected to experience the fastest compound annual growth rate (CAGR) of 27.7% during the forecast period. The rapid adoption of digital technologies, machine learning, artificial intelligence (AI), and the Internet of Things (IoT) in countries such as India, Australia, South Korea, and China has generated substantial data assets that need protection from various threats, including ransomware, malware, and data breaches. To tackle these cybersecurity challenges, governments are instituting laws and regulations like India's Information Technology Act, 2000, Singapore's Cybersecurity Act, and Australia's Security of Critical Infrastructure Protection Act, which are further fueling the demand for data-centric security solutions.
Do You Need any Customization Research on Data-Centric Security Market - Inquire Now
Key Players
The major key players are
-
Microsoft - Azure Information Protection
-
IBM - IBM Security Guardium
-
McAfee - McAfee Total Protection
-
Symantec (Broadcom) - Symantec Data Loss Prevention
-
Oracle - Oracle Advanced Security
-
Forcepoint - Forcepoint Data Loss Prevention
-
Digital Guardian - Digital Guardian Data Protection Platform
-
Cisco - Cisco Cloudlock
-
Thales - Thales CipherTrust Data Security Platform
-
Palo Alto Networks - Prisma Cloud
-
Vormetric (Thales) - Vormetric Data Security Platform
-
Varonis - Varonis Data Security Platform
-
Imperva - Imperva Data Security
-
SailPoint - SailPoint IdentityNow
-
CyberArk - CyberArk Privileged Access Security
-
Micro Focus - Micro Focus Voltage SecureData
-
F5 Networks - F5 Advanced WAF
-
RSA Security - RSA Data Protection Manager
-
Check Point Software - Check Point Data Security Solutions
-
Tenable - Tenable.io
Recent Developments
-
January 2024: Fortinet announced the integration of enhanced AI-driven data protection features into their existing security frameworks, allowing businesses to detect and respond to data breaches more effectively
-
March 2024: Symantec unveiled advancements in their endpoint security solutions that incorporate real-time data monitoring and anomaly detection to prevent insider threats
| Report Attributes | Details |
|---|---|
| Market Size in 2023 | USD 5.27 Billion |
| Market Size by 2032 | USD 36.64 Billion |
| CAGR | CAGR of 24.06% From 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Solutions (Solution, Services) • By Deployment (On-Premises, Cloud) • By Organization Size (Large Enterprise, SMEs) • By Vertical (BFSI, Government and Public Sector, Healthcare, IT and Telecom, Retail, Others) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles | Microsoft, IBM, McAfee, Symantec, Oracle, Forcepoint, Digital Guardian, Cisco, Thales, Palo Alto Networks, Vormetric ,Varonis, Imperva, SailPoint. |
| Key Drivers | • The rise of remote work has expanded the attack surface, increasing the demand for robust data security solutions to protect sensitive information accessed from various locations. • Stringent data protection regulations, such as GDPR and HIPAA, compel organizations to adopt data-centric security solutions to avoid hefty fines and ensure compliance. |
| RESTRAINTS | • The initial costs associated with implementing advanced data-centric security solutions can be prohibitive for smaller organizations, hindering their ability to adopt necessary technologies • There is a shortage of skilled professionals in data security, making it difficult for organizations to find qualified personnel to implement and manage data-centric security measures effectively |

